Exam Code: 156-215.80 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Check Point Certified Security Administrator
Certification Provider: Check-Point
Free Today! Guaranteed Training- Pass 156-215.80 Exam.
Check-Point 156-215.80 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Harriet wants to protect sensitive information from intentional loss when users browse to a specific URL: https://personal.mymail.com, which blade will she enable to achieve her goal?
- A. DLP
- B. SSL Inspection
- C. Application Control
- D. URL Filtering
Answer: A
Explanation:
Check Point revolutionizes DLP by combining technology and processes to move businesses from passive detection to active Data Loss Prevention. Innovative MultiSpect™ data classification combines user, content and process information to make accurate decisions, while UserCheck™ technology empowers users to remediate incidents in real time. Check Point’s self-educating network-based DLP solution frees IT/security personnel from incident handling and educates users on proper data handling policies—protecting sensitive corporate information from both intentional and unintentional loss.
NEW QUESTION 2
Which component functions as the Internal Certificate Authority for R77?
- A. Security Gateway
- B. Management Server
- C. Policy Server
- D. SmartLSM
Answer: B
NEW QUESTION 3
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _______
- A. User data base corruption
- B. LDAP conflicts
- C. Traffic issues
- D. Phase two key negotiation
Answer: C
Explanation:
Check Point's FW Monitor is a powerful built-in tool for capturing network traffic at the packet level. The Monitor utility captures network packets at multiple capture points along the FireWall inspection chains. These captured packets can be inspected later using the WireShark
NEW QUESTION 4
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
- A. All options stop Check Point processes
- B. backup
- C. migrate export
- D. snapshot
Answer: D
NEW QUESTION 5
What is the Transport layer of the TCP/IP model responsible for?
- A. It transports packets as datagrams along different routes to reach their destination.
- B. It manages the flow of data between two hosts to ensure that the packets are correctly assembled and delivered to the target application.
- C. It defines the protocols that are used to exchange data between networks and how host programs interact with the Application layer.
- D. It deals with all aspects of the physical components of network connectivity and connects with different network types.
Answer: B
NEW QUESTION 6
Which of the following uses the same key to decrypt as it does to encrypt?
- A. Asymmetric encryption
- B. Dynamic encryption
- C. Certificate-based encryption
- D. Symmetric encryption
Answer: D
NEW QUESTION 7
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
- A. Have the security administrator select the Action field of the Firewall Rule “Redirect HTTP connections to an authentication (captive) portal”.
- B. Have the security administrator reboot the firewall.
- C. Have the security administrator select Any for the Machines tab in the appropriate Access Role.
- D. Install the Identity Awareness agent on her iPad.
Answer: A
NEW QUESTION 8
What does ExternalZone represent in the presented rule?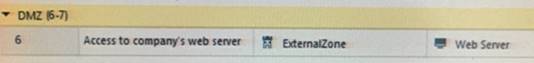
- A. The Internet.
- B. Interfaces that administrator has defined to be part of External Security Zone.
- C. External interfaces on all security gateways.
- D. External interfaces of specific gateways.
Answer: B
Explanation:
Configuring Interfaces
Configure the Security Gateway 80 interfaces in the Interfaces tab in the Security Gateway window. To configure the interfaces:
From the Devices window, double-click the Security Gateway 80.
The Security Gateway
window opens.
Select the Interfaces tab.
Select Use the following settings. The interface settings open.
Select the interface and click Edit.
The Edit window opens.
From the IP Assignment section, configure the IP address of the interface:
Select Static IP.
Enter the IP address and subnet mask for the interface.
In Security Zone, select Wireless, DMS, External, or Internal. Security zone is a type of zone, created by a bridge to easily create segments, while maintaining IP addresses and router configurations. Security zones let you choose if to enable or not the firewall between segments.
References:
NEW QUESTION 9
When defining QoS global properties, which option below is not valid?
- A. Weight
- B. Authenticated timeout
- C. Schedule
- D. Rate
Answer: C
NEW QUESTION 10
Which identity Source(s) should be selected in Identity Awareness for when there is a requirement for a higher level of security for sensitive servers?
- A. ADQuery
- B. Terminal Servers Endpoint Identity Agent
- C. Endpoint Identity Agent and Browser-Based Authentication
- D. RADIUS and Account Logon
Answer: D
NEW QUESTION 11
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
- A. RADIUS
- B. Active Directory Query
- C. Remote Access
- D. Certificates
Answer: D
NEW QUESTION 12
Which application should you use to install a contract file?
- A. SmartView Monitor
- B. WebUI
- C. SmartUpdate
- D. SmartProvisioning
Answer: C
Explanation:
Using SmartUpdate: If you already use an NGX R65 (or higher) Security Management / Provider-1 /
Multi-Domain Management Server, SmartUpdate allows you to import the service contract file that you have downloaded in Step #3.
Open SmartUpdate and from the Launch Menu select 'Licenses & Contracts' -> 'Update Contracts' -> 'From File...' and provide the path to the file you have downloaded in Step #3: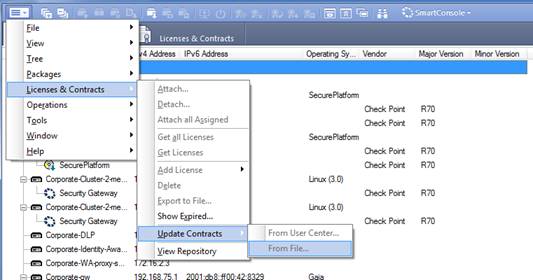
Note: If SmartUpdate is connected to the Internet, you can download the service contract file directly from the UserCenter without going through the download and import steps.
NEW QUESTION 13
Packages and licenses are loaded from all of these sources EXCEPT
- A. Download Center Web site
- B. UserUpdate
- C. User Center
- D. Check Point DVD
Answer: B
Explanation:
the Download Center web site (packages)
the Check Point DVD (packages)
the User Center (licenses)
by importing a file (packages and licenses)
by running the cplic command line
Packages and licenses are loaded into these repositories from several sources: References:
NEW QUESTION 14
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
- A. INSPECT Engine
- B. Stateful Inspection
- C. Packet Filtering
- D. Application Layer Firewall
Answer: B
NEW QUESTION 15
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
- A. Security Gateway IP-address cannot be changed without re-establishing the trust
- B. The Security Gateway name cannot be changed in command line without re-establishing trust
- C. The Security Management Server name cannot be changed in SmartConsole without re-establishing trust
- D. The Security Management Server IP-address cannot be changed without re-establishing the trust
Answer: A
NEW QUESTION 16
Which statement is NOT TRUE about Delta synchronization?
- A. Using UDP Multicast or Broadcast on port 8161
- B. Using UDP Multicast or Broadcast on port 8116
- C. Quicker than Full sync
- D. Transfers changes in the Kernel tables between cluster members
Answer: A
NEW QUESTION 17
Administrator Kofi has just made some changes on his Management Server and then clicks on the Publish button in SmartConsole but then gets the error message shown in the screenshot below.
Where can the administrator check for more information on these errors?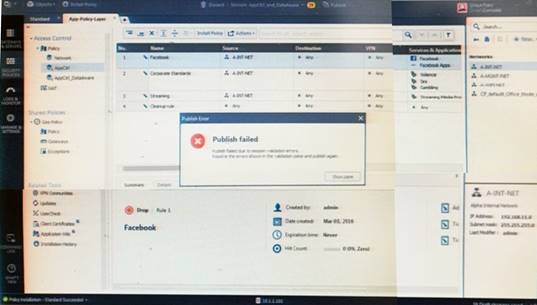
- A. The Log and Monitor section in SmartConsole
- B. The Validations section in SmartConsole
- C. The Objects section in SmartConsole
- D. The Policies section in SmartConsole
Answer: B
Explanation:
Validation Errors
The validations pane in SmartConsole shows configuration error messages. Examples of errors are object names that are not unique, and the use of objects that are not valid in the Rule Base.
To publish, you must fix the errors.
NEW QUESTION 18
What happens when you run the command: fw sam -J src [Source IP Address]?
- A. Connections from the specified source are blocked without the need to change the Security Policy.
- B. Connections to the specified target are blocked without the need to change the Security Policy.
- C. Connections to and from the specified target are blocked without the need to change the Security Policy.
- D. Connections to and from the specified target are blocked with the need to change the Security Policy.
Answer: A
NEW QUESTION 19
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
- A. Detects and blocks malware by correlating multiple detection engines before users are affected.
- B. Configure rules to limit the available network bandwidth for specified users or groups.
- C. Use UserCheck to help users understand that certain websites are against the company’s security policy.
- D. Make rules to allow or block applications and Internet sites for individual applications, categories, and risk levels.
Answer: A
NEW QUESTION 20
Where do we need to reset the SIC on a gateway object?
- A. SmartDashboard > Edit Gateway Object > General Properties > Communication
- B. SmartUpdate > Edit Security Management Server Object > SIC
- C. SmartUpdate > Edit Gateway Object > Communication
- D. SmartDashboard > Edit Security Management Server Object > SIC
Answer: A
NEW QUESTION 21
Fill in the blank: By default, the SIC certificates issued by R80 Management Server are based on the _____ algorithm.
- A. SHA-256
- B. SHA-200
- C. MD5
- D. SHA-128
Answer: A
NEW QUESTION 22
Two administrators Dave and Jon both manage R80 Management as administrators for ABC Corp. Jon logged into the R80 Management and then shortly after Dave logged in to the same server. They are both in the Security Policies view. From the screenshots below, why does Dave not have the rule no.6 in his SmartConsole view even though Jon has it his in his SmartConsole view?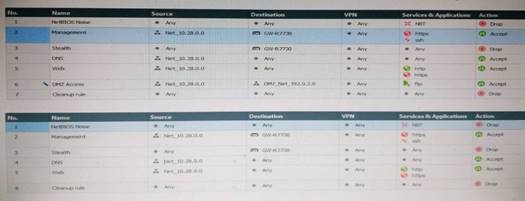
- A. Jon is currently editing rule no.6 but has Published part of his changes.
- B. Dave is currently editing rule no.6 and has marked this rule for deletion.
- C. Dave is currently editing rule no.6 and has deleted it from his Rule Base.
- D. Jon is currently editing rule no.6 but has not yet Published his changes.
Answer: D
Explanation:
When an administrator logs in to the Security Management Server through SmartConsole, a new editing session starts. The changes that the administrator makes during the session are only available to that administrator. Other administrators see a lock icon on object and rules that are being edited. To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
NEW QUESTION 23
......
100% Valid and Newest Version 156-215.80 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/156-215.80-exam-dumps.html (New 485 Q&As)