It is more faster and easier to pass the Check-Point 156-315.80 exam by using Practical Check-Point Check Point Certified Security Expert - R80 questuins and answers. Immediate access to the Improve 156-315.80 Exam and find the same core area 156-315.80 questions with professionally verified answers, then PASS your exam with a high score now.
Online 156-315.80 free questions and answers of New Version:
NEW QUESTION 1
What is the protocol and port used for Health Check and State Synchronization in ClusterXL?
- A. CCP and 18190
- B. CCP and 257
- C. CCP and 8116
- D. CPC and 8116
Answer: C
NEW QUESTION 2
As an administrator, you may be required to add the company logo to reports. To do this, you would save the logo as a PNG file with the name ‘cover-company-logo.png’ and then copy that image file to which directory on the SmartEvent server?
- A. SFWDIR/smartevent/conf
- B. $RTDIR/smartevent/conf
- C. $RTDIR/smartview/conf
- D. $FWDIR/smartview/conf
Answer: C
NEW QUESTION 3
What component of R80 Management is used for indexing?
- A. DBSync
- B. API Server
- C. fwm
- D. SOLR
Answer: D
NEW QUESTION 4
Which directory below contains log files?
- A. /opt/CPSmartlog-R80/log
- B. /opt/CPshrd-R80/log
- C. /opt/CPsuite-R80/fw1/log
- D. /opt/CPsuite-R80/log
Answer: C
NEW QUESTION 5
Which command gives us a perspective of the number of kernel tables?
- A. fw tab -t
- B. fw tab -s
- C. fw tab -n
- D. fw tab -k
Answer: B
NEW QUESTION 6
Which of these statements describes the Check Point ThreatCloud?
- A. Blocks or limits usage of web applications
- B. Prevents or controls access to web sites based on category
- C. Prevents Cloud vulnerability exploits
- D. A worldwide collaborative security network
Answer: D
NEW QUESTION 7
What can we infer about the recent changes made to the Rule Base?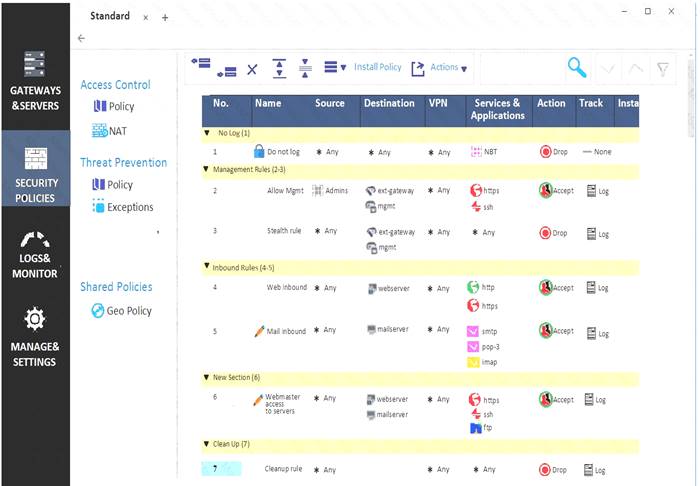
- A. Rule 7 was created by the ‘admin’ administrator in the current session
- B. 8 changes have been made by administrators since the last policy installation
- C. The rules 1, 5 and 6 cannot be edited by the ‘admin’ administrator
- D. Rule 1 and object webserver are locked by another administrator
Answer: D
NEW QUESTION 8
Pamela is Cyber Security Engineer working for Global Instance Firm with large scale deployment of Check Point Enterprise Appliances using GAiA/R80.10. Company’s Developer Team is having random access issue to newly deployed Application Server in DMZ’s Application Server Farm Tier and blames DMZ Security Gateway as root cause. The ticket has been created and issue is at Pamela’s desk for an investigation. Pamela decides to use Check Point’s Packet Analyzer Tool-fw monitor to iron out the issue during approved Maintenance window.
What do you recommend as the best suggestion for Pamela to make sure she successfully captures entire traffic in context of Firewall and problematic traffic?
- A. Pamela should check SecureXL status on DMZ Security gateway and if it’s turned O
- B. She should turn OFF SecureXL before using fw monitor to avoid misleading traffic captures.
- C. Pamela should check SecureXL status on DMZ Security Gateway and if it’s turned OF
- D. She should turn ON SecureXL before using fw monitor to avoid misleading traffic captures.
- E. Pamela should use tcpdump over fw monitor tool as tcpdump works at OS-level and captures entire traffic.
- F. Pamela should use snoop over fw monitor tool as snoop works at NIC driver level and captures entire traffic.
Answer: A
NEW QUESTION 9
What is the difference between SSL VPN and IPSec VPN?
- A. IPSec VPN does not require installation of a resilient VPN client.
- B. SSL VPN requires installation of a resident VPN client.
- C. SSL VPN and IPSec VPN are the same.
- D. IPSec VPN requires installation of a resident VPN client and SSL VPN requires only an installed Browser.
Answer: D
NEW QUESTION 10
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret the administrator found that the check box to enable pre-shared secret and cannot be enabled.
Why does it not allow him to specify the pre-shared secret?
- A. IPsec VPN blade should be enabled on both Security Gateway.
- B. Pre-shared can only be used while creating a VPN between a third party vendor and Check Point Security Gateway.
- C. Certificate based Authentication is the only authentication method available between two Security Gateway managed by the same SMS.
- D. The Security Gateways are pre-R75.40.
Answer: C
NEW QUESTION 11
Connections to the Check Point R80 Web API use what protocol?
- A. HTTPS
- B. RPC
- C. VPN
- D. SIC
Answer: A
NEW QUESTION 12
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
- A. To satellites through center only
- B. To center only
- C. To center and to other satellites through center
- D. To center, or through the center to other satellites, to Internet and other VPN targets
Answer: D
NEW QUESTION 13
When an encrypted packet is decrypted, where does this happen?
- A. Security policy
- B. Inbound chain
- C. Outbound chain
- D. Decryption is not supported
Answer: A
NEW QUESTION 14
In the Check Point Security Management Architecture, which component(s) can store logs?
- A. SmartConsole
- B. Security Management Server and Security Gateway
- C. Security Management Server
- D. SmartConsole and Security Management Server
Answer: B
NEW QUESTION 15
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
- A. UDP port 265
- B. TCP port 265
- C. UDP port 256
- D. TCP port 256
Answer: D
Explanation:
Synchronization works in two modes:
Full Sync transfers all Security Gateway kernel table information from one cluster member to another. It is handled by the fwd daemon using an encrypted TCP connection on port 256.
Delta Sync transfers changes in the kernel tables between cluster members. Delta sync is handled by the Security Gateway kernel using UDP connections on port 8116.
NEW QUESTION 16
......
Recommend!! Get the Full 156-315.80 dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/156-315.80-dumps/ (New 428 Q&As Version)