Your success in is our sole target and we develop all our in a way that facilitates the attainment of this target. Not only is our material the best you can find, it is also the most detailed and the most updated. for Cisco 200-601 are written to the highest standards of technical accuracy.
Also have 200-601 free dumps questions for you:
NEW QUESTION 1
Which in-depth approach is used when deploying defense in an industrial zone?
- A. Use PLCs and control systems from multiple vendors in such a way that the process will become resilient for failures of one vendor.
- B. Deploy two factor authentications for all operators which need to login remote while working from home.
- C. Collect log files at a central location for easy back-up and encryption to provide privacy.
- D. Create multiple zones in the industrial zone and protect / inspect traffic between the zones with firewalls and intrusion monitors.
Answer: D
NEW QUESTION 2
Refer to the exhibit.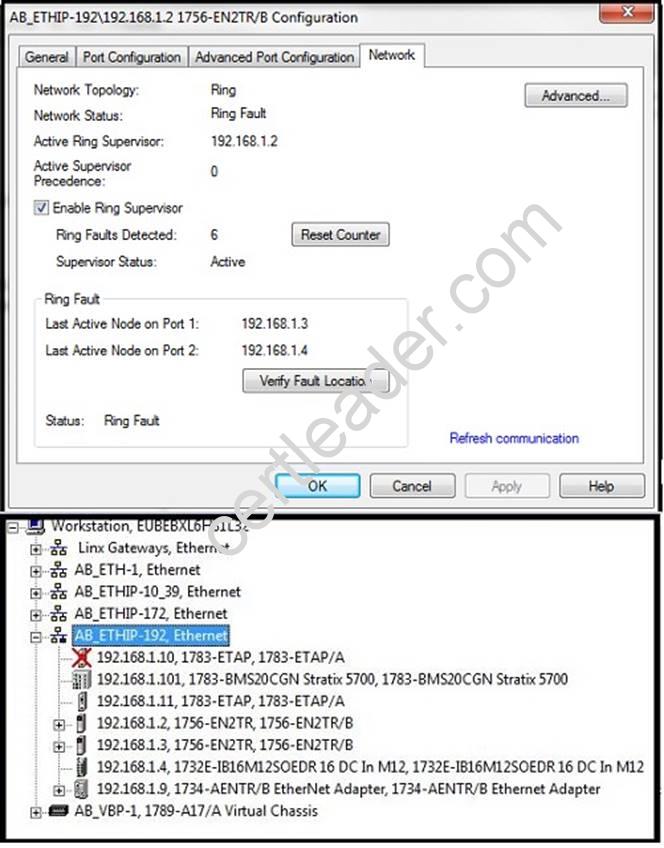
Network Faceplates have not been installed on the HMI and so you need to map a network based on information available from RSLinx. Which most accurately represents the network configuration?
- A. [MISSING]
- B. [MISSING]
- C. [MISSING]
- D. [MISSING]
Answer: B
NEW QUESTION 3
Given a ring topology, which loop prevention mechanism provides the fastest reconvergence time after a link failure?
- A. Rapid Per-VLAN Spanning Tree Protocol
- B. Resilient Ethernet Protocol
- C. Multiple Spanning Tree Protocol
- D. Spanning Tree Protocol
Answer: B
NEW QUESTION 4
Which CLI command will display IGMP snooping information in a Cisco IE2000 or Stratix 5700 switch?
- A. switch#show snooping ip igmp
- B. switch#show igmp snooping
- C. switch#show ip igmp snooping
- D. switch#show ip snooping
Answer: C
NEW QUESTION 5
Refer to the exhibit.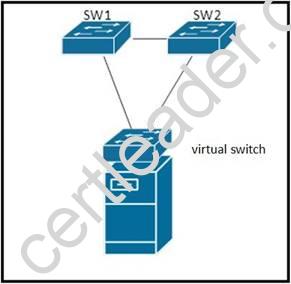
SW1, SW2 and virtual switch are connected in a loop. SW1 and SW2 are standard layer-2 switches. Which loop prevention mechanism is best suited for use within this topology?
- A. Per-VLAN Rapid Spanning Tree Protocol+
- B. End-Host Mode
- C. Multi-chassis EtherChannel
- D. BPDU Guard
Answer: B
NEW QUESTION 6
You have been tasked to design an Ethernet network capable of Motion control with cycle times not to exceed 1ms. In order to create a more deterministic network, what characteristic/s should you primarily focus on?
- A. Lattency and Jitter
- B. Redundancy and high availability
- C. Explicit and Implicit messaging
- D. This cycle time is not possible on an Ethernet network
- E. Gigabit port speed
Answer: A
NEW QUESTION 7
Which statement is correct regarding Media Redundancy Protocol (MRP) in a ring of ProfiNET devices?
- A. When a link fault is detected, MRP rings must converge in less than 100 milliseconds
- B. MRP defines two device roles, Media Redundancy Master and Media Redundancy Client
- C. MRP can support rings of up to 250 devices
- D. MRP is only supported on network switches
Answer: B
NEW QUESTION 8
Why is SSH preferred over Telnet as a method of accessing a network device to alter or view the configuration?
- A. Telnet encrypts only the login information, not the entire transmission.
- B. SSH requires fewer network resources and no additional configuration.
- C. Telnet is more difficult to use and configure than SSH.
- D. SSH encrypts the login and session information.
Answer: D
NEW QUESTION 9
A shutdown in the cookie cutter machine was traced to a broken network cable. What are two reasons that explain why using DLR is an appropriate choice for network resiliency? (Choose two)
- A. DLR is designed for single network operation at the machine level
- B. Moving to a linear topology will reduce the number of cables and so reduce risk of cable failure
- C. DLR is the only resiliency technology that is supported by CIP Safety
- D. Layer 2 resiliency protocols like REP and RSTP do not have a fast enough convergence time for motion control
- E. Half of the network traffic goes clockwise on the ring and the other half counter- clockwise, reducing by 50% the impact of cable failure
Answer: AD
NEW QUESTION 10
Which scenario represents the correct configuration to support the SSIDs of this autonomous access point?
- A. [MISSING]
- B. [MISSING]
- C. [MISSING]
- D. [MISSING]
Answer: D
NEW QUESTION 11
What is the purpose of Spanning Tree Protocol?
- A. to prevent routing loops
- B. to create a default route
- C. to provide multiple gateways for hosts
- D. to maintain a loop-free Layer 2 network topology
- E. to enhance the functions of SNMP
Answer: D
NEW QUESTION 12
Which is an issue with running CIP Motion on a REP network and identifies an alternate resiliency protocol that works for CIP Motion?
- A. CIP Motion requires a star topology which is not supported by RE
- B. DLR is a suitable resiliency protocol for CIP motion.
- C. REP convergence is not fast enoug
- D. DLR is a suitable resiliency protocol for CIP motion.
- E. CIP Motion requires a star topology which is not supported by RE
- F. RPVST+ is a suitable resiliency protocol for CIP motion.
- G. REP convergence is not fast enoug
- H. RPVST+ is a suitable resiliency protocol for CIP motion.
Answer: B
NEW QUESTION 13
Which describes the relationship between a workgroup bridge?
- A. Wired clients of a workgroup bridge can communicate, through the workgroup bridge, with wireless clients of an autonomous or a controller-based access point
- B. Wireless clients of a controller-based AP can communicate, through the workgroup bridge, with wireless clients of an autonomous access point
- C. Wireless clients of an autonomous access point can communicate with wired clients of a workgroup bridge, but Wireless clients of a controller-based access point cannot communicate with wired clients of a workgroup bridge
- D. Wireless clients of a controller-based access point can communicate with wired clients of a workgroup bridge, but Wireless clients of an autonomous access point cannot communicate with wired clients of a workgroup bridge
Answer: A
NEW QUESTION 14
Refer to the exhibit.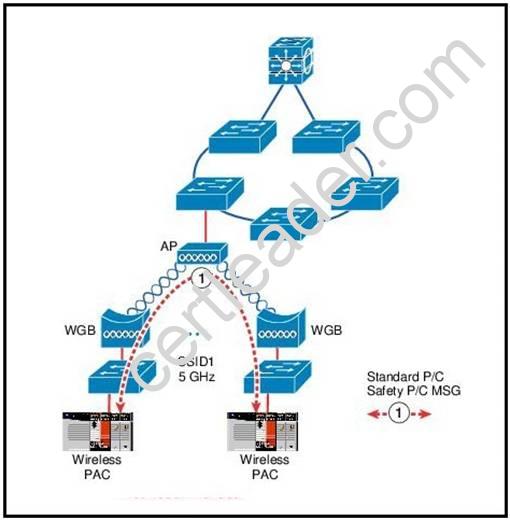
What issue does this topology present for the represented traffic flow?
- A. Standard Produce/Consume traffic is not suitable for an 802.11 wireless environment.
- B. Only one of the Work Group Bridges can transmit at a time, because 802.11 is half duplex.
- C. The Converged Plant-wide Ethernet best practices for 802.11 wireless don't allow for PAC to PAC traffic.
- D. I/O control traffic should utilize the 2.4 GHz band based on best practices.
Answer: B
NEW QUESTION 15
A ProfiNET management system operator is unable to add a ProfiNET Conformance Class B device to a SIMATIC management station. The device is connected to interface FastEthernet1/3. Based on the provided CLI output, which statement is correct?
switch#show profinet lldp Fa1/1 port-003-00000 On Fa1/2 port-004-00000 On Fa1/3 port-005-00000 Off Fa1/4 port-006-00000 Off Fa1/5 port-007-00000 On Fa1/6 port-008-00000 Off Fa1/7 port-009-00000 On Fa1/8 port-010-00000 Off
- A. LLDP has been disabled on this switch
- B. The connected device is not sending LLDP packets with ProfiNET extensions
- C. The port label needs to be changed on interface FastEthernet 1/3 to "port-003-00000"
- D. ProfiNET is disabled on this switch
Answer: B
NEW QUESTION 16
A ProfiNET management system operator is unable to see diagnostic information for a Cisco Industrial Ethernet switch that has been added to a SIMATIC management station. Based on the provided CLI output, which statement is correct?
switch# show profinet status State : Enabled
Vlan : 201
Id : IE2000-Switch Connected : Yes ReductRatio : 128
GSD version : Mis-match
- A. The assigned ProfiNET VLAN is not valid and should be less than 100
- B. LLDP has been disabled on this switch
- C. The GSD file version on the switch does not match the GSD file version on the management station
- D. The Reduction Ration has been set too low
Answer: C
NEW QUESTION 17
Which selection is a reason why IGMP snooping should be configured on a switched network?
- A. IGMP snooping populates the snooping table with the results of DHCP requests and can be used by Dynamic ARP Inspection to block IP spoofing attacks at Layer-2.
- B. IGMP snooping verifies the source IP address of every IPv4 packet to ensure that it hasn't been originated from a port different than its return path.
- C. IGMP snooping is used to filter ping requests and results to avoid overflowing the MAC address table of the switch.
- D. IGMP snooping allows a Layer-2 switch to limit the transmission of multicast frames to only the ports that have members of the relevant IGMP group.
Answer: D
NEW QUESTION 18
Which option best describes the ProfiNET Discovery and Configuration Protocol (DCP)?
- A. Can be used to override both static and dynamically (DHCP/BOOTP) assigned IP addresses
- B. Cannot be used to reset a device to factory defaults
- C. Is only supported in Conformance Class B and C devices
- D. Uses the ProfiNET-IRT communication class
Answer: A
P.S. Exambible now are offering 100% pass ensure 200-601 dumps! All 200-601 exam questions have been updated with correct answers: https://www.exambible.com/200-601-exam/ (87 New Questions)