Breathing of 220-1002 test materials and answers for CompTIA certification for customers, Real Success Guaranteed with Updated 220-1002 pdf dumps vce Materials. 100% PASS CompTIA A+ Certification Exam: Core 2 exam Today!
Free 220-1002 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
Users notify the help desk of an email that was just received. The email came from the help desk’s email address and asked the users to click on an embedded link. This email is BEST described as:
- A. phishing.
- B. zombie.
- C. whaling.
- D. spoofing.
Answer: D
NEW QUESTION 2
Which of the following types of scripts would be seen on the user end of a web page?
- A. .bat
- B. .js
- C. .sh
- D. .vbs
Answer: D
NEW QUESTION 3
A technician logs on to a Linux computer and runs the following command: ps -aux | grep vi
Which of the following MOST accurately describes the effect of the command?
- A. It kills any running programs starting with the letters vi.
- B. It opens a list of directories that start with the letters vi.
- C. It creates a new file named grep in the current working directory.
- D. If finds a list of processes running a text editor.
Answer: D
NEW QUESTION 4
Which of the following is the MOST secure wireless security protocol?
- A. AES
- B. WPA
- C. WPA2
- D. WEP
Answer: A
NEW QUESTION 5
A user calls a technician regarding an iOS mobile device that is having problems with standby time after a new update was applied. The technician verifies no new applications were installed since the update, but the device still has poor standby time even after the update is removed. Which of the following is the MOST likely cause of the issue?
- A. Zero-day malware
- B. Safari code injection
- C. OS corruption
- D. Overheating
- E. Time sync failure
Answer: D
NEW QUESTION 6
A technician needs to connect to a network switch in a remote location. The technician wants to make sure the data passed over the wire is encrypted so it cannot be read by someone using a sniffer. Which of the following connection protocols should the technician use?
- A. Telnet
- B. SSH
- C. SMB
- D. HTTP
- E. SFTP
Answer: B
NEW QUESTION 7
A network administrator has noticed unusual activity with a user’s login credentials on the network. The user is attempting multiple simultaneous login across the network, some of which are attempting to access workstations and servers to which the user does not have access.
Which of the following should the network administrator do NEXT?
- A. Delete the user’s AD account.
- B. Decrease the user’s AD privileges.
- C. Disable the user’s AD account.
- D. Reset the password on the user’s AD account.
Answer: C
NEW QUESTION 8
A network administrator has given a technician documentation detailing the switchports the technician will need to patch in for a network upgrade. Which of the following documents did the network administrator MOST likely give to the technician?
- A. Process diagram
- B. Physical network diagram
- C. Fiber backbone diagram
- D. Logical topology diagram
Answer: B
NEW QUESTION 9
A user reports slow performance on a computer. A technician checks the computer and finds the RAM utilization Is very high. The technician restarts the computer, and the RAM use is still high. The technician discovers a program running in the background Is using most of the RAM. The user only uses this program once at the end of the year to produce a report. Which of the following steps should the technician take to improve the computer's performance?
- A. Uninstall and reinstall the program.
- B. Perform a repair installation of the program
- C. Install the latest updates for the program.
- D. Disable the program on startup.
Answer: A
NEW QUESTION 10
A user is attempting to install an application and receives an error stating there is not enough space to install the application. Which of the following did the user overlook?
- A. Installation method
- B. System requirements
- C. OS compatibility
- D. File permissions
Answer: B
NEW QUESTION 11
A technician is setting up a SOHO wireless network for a healthcare office that does not have a server. The user requires the highest level of wireless security and various levels of desktop authentication to access cloud resources.
Which of the following protocols and authentication methods should the technician implement? (Select two.)
- A. WPA
- B. WPA2
- C. WEP
- D. TKIP
- E. RADIUS
- F. Multifactor
- G. TACACS
- H. SSO
Answer: BF
NEW QUESTION 12
A user’s mobile device appears to be losing battery life rapidly and often feels warm to the touch, even when it is put away.
The device is relatively new, so the user is concerned it is defective. A technician inspects the device and see the following:
Which of the following should be changed to resolve this issue?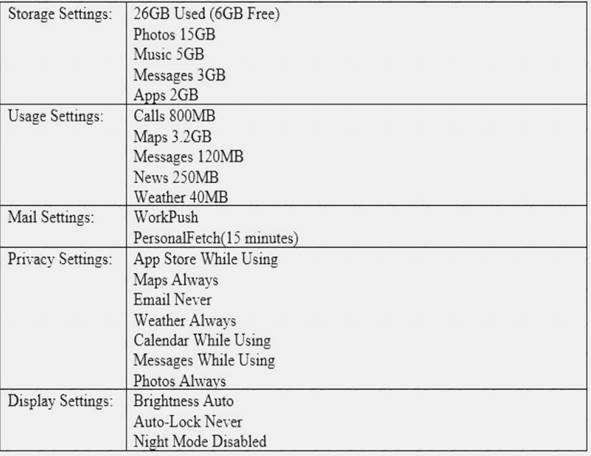
- A. Privacy – Maps
- B. Display – Brightness
- C. Storage – Photos
- D. Mail – Work
Answer: B
NEW QUESTION 13
A user is working on a shared computer and attempts to open the email application, which freezes when opened. A technician logs into the computer, and the email application works without issue. The technician has the user log back in, but the application still freezes when opened. Which of the following is the NEXT step the technician should take to resolve the issue?
- A. Check for and apply software updates
- B. Perform repair installation on the application
- C. Add the user to the local administrators group
- D. Rebuild the user’s mail profile
Answer: D
NEW QUESTION 14
A user calls the help desk regarding a new Windows issue that started in the morning. The user can no longer use any locally attached devices such as a mouse or a printer, and a reboot did not fix the problem Which of the following would MOST likely fix the issue?
- A. Roll back updates.
- B. Disable the Windows Update service
- C. Check for updates
- D. Restore hidden updates
Answer: A
NEW QUESTION 15
A new company policy states that all end-user access to network resources will be controlled based on the users’ roles and responsibilities within the organization. Which of the following security concepts has the company just enabled?
- A. Certificates
- B. Least privilege
- C. Directory permissions
- D. Blacklists
Answer: B
NEW QUESTION 16
An end user’s PC is taking a long time to boot. Which of the following operations would be the BEST to resolve this issue with minimal expense? (Select two.)
- A. Remove applications from startup
- B. Defragment the hard drive
- C. Install additional RAM
- D. Install a faster hard drive
- E. End the processes in Task Manager
- F. Run the Disk Cleanup utility
Answer: AB
NEW QUESTION 17
A small business has an open wireless network so vendors can connect to the network without logging in. The business owners are concerned that a nearby company is connecting and using the wireless connection without permission. If the small business requires that the network remain open, which of the following configuration settings should be changed to address these concerns?
- A. Default SSID
- B. MAC filtering
- C. Power levels
- D. Content filtering
- E. Firewall
Answer: C
NEW QUESTION 18
Joe, an employee, took a company-issues Windows laptop home, but is having trouble connecting to any of the shares hosted on his home media server.
Joe has verified he is connected to the Internet.
Which of the following would explain why Joe cannot access his personal shares?
- A. An IP conflict is present
- B. A corporate VPN is enabled
- C. A firewall exception must be set
- D. HomeGroup must be enabled
Answer: C
NEW QUESTION 19
A user is trying to install a very large .dmg file on a Windows computer but is receiving an error message. Which of the following is causing the error?
- A. Small hard drive
- B. Insufficient RAM
- C. OS compatibility
- D. Folder permissions
Answer: C
NEW QUESTION 20
A MAC user’s operating system became corrupted, and files were deleted after malware was downloaded. The user needs to access the data that was previously stored on the MAC. Which of the following built-in utilities should be used?
- A. Time Machine
- B. Snapshot
- C. System Restore
- D. Boot Camp
Answer: A
NEW QUESTION 21
During the firmware upgrade of a web server, a power outage occurred. The outage caused a failure within the upgrade. Which of the following plans must be implemented to revert back to the most recent version of the firmware?
- A. Backout plan
- B. Contingency plan
- C. Alternative plan
- D. Backup plan
Answer: D
NEW QUESTION 22
Company policy states that users must secure their laptops before leaving the office for the evening Which of the following physical security measures should be used?
- A. Cable lock
- B. Windows key + L
- C. Smart card removal
- D. Key fob
- E. BIOS password
Answer: A
NEW QUESTION 23
Joe, a user, calls the help desk from a coffee shop while on a business trip to report the WiFi hotspot on his phone is extremely slow. The technician runs a speed test from a laptop connected to the hotspot and gets 200Kbps. Ann, Joe’s coworker with whom he is travelling, also has a hotspot on her phone, and the speed test result on that hotspot is 15Mbps. The technician checks the hotspot settings on Joe’s phone and sees the following:
Which of the following is the MOST likely cause of the problem?
- A. Joe should be using WEP security on his hotspot for faster throughput
- B. Someone else is using Joe’s hotspot due to weak password
- C. Joe’s hotspot gave him an invalid IP address
- D. Joe is likely in a poor signal area and should try another area
Answer: B
NEW QUESTION 24
A technician receives a phone call regarding ransomware that has been detected on a PC in a remote office. Which of the following steps should the technician take FIRST?
- A. Disconnect the PC from the network
- B. Perform an antivirus scan
- C. Run a backup and restore
- D. Educate the end user
Answer: A
NEW QUESTION 25
Which of the following is the amount of memory a user is limited to with a 32-bit version of Windows?
- A. 2GB
- B. 4GB
- C. 8GB
- D. 16GB
Answer: B
NEW QUESTION 26
A SOHO technician needs to upgrade two computers quickly and is not concerned about retaining user settings. The users currently have Windows 8 and want to upgrade to Windows 10.
Which of the following installation methods would the technician MOST likely use to accomplish this quickly?
- A. Unattended installation
- B. Remote network installation
- C. In-place upgrade
- D. Clean installation
Answer: A
NEW QUESTION 27
A user contacts a technician to troubleshoot server errors. The user explains that some files will not open on the server, the data backups are operational, and the weather has been bad. The technician notices missing time slots in the event log.
Which of the following should the technician replace to prevent these issues in the future?
- A. System memory
- B. Surge protector
- C. Hard drives
- D. Battery backup
Answer: D
NEW QUESTION 28
An administrator is setting up a Windows terminal server. Which of the following settings should the administrator modify to increase server security? (Select two.)
- A. Change the default access port
- B. Enforce password complexity
- C. Put the terminal server into the router’s DMZ
- D. Disable logon time restrictions
- E. Block all unused ports on the LAN smart switch
- F. Use the local client certificate for server authentication
Answer: BE
NEW QUESTION 29
A technician is setting up a kiosk. The technician needs to ensure the kiosk is secure and users will have access to only the application needed for customer interaction. The technician must also ensure that whenever the computer is rebooted or powered on it logs on automatically without a password.
Which of the following account types would the technician MOST likely set up on this kiosk machine?
- A. Guest
- B. Administrator
- C. Power User
- D. Remote Desktop User
Answer: A
NEW QUESTION 30
......
100% Valid and Newest Version 220-1002 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/220-1002-pdf-download.html (New 188 Q&As)