Your success in Cisco 300-735 is our sole target and we develop all our 300-735 braindumps in a way that facilitates the attainment of this target. Not only is our 300-735 study material the best you can find, it is also the most detailed and the most updated. 300-735 Practice Exams for Cisco Cisco Other Exam 300-735 are written to the highest standards of technical accuracy.
Free 300-735 Demo Online For Cisco Certifitcation:
NEW QUESTION 1
DRAG DROP
Drag and drop the code to complete the curl query to the Umbrella Reporting API that provides a detailed report of blocked security activity events from the organization with an organizationId of "12345678" for the last 24 hours. Not all options are used.
Select and Place: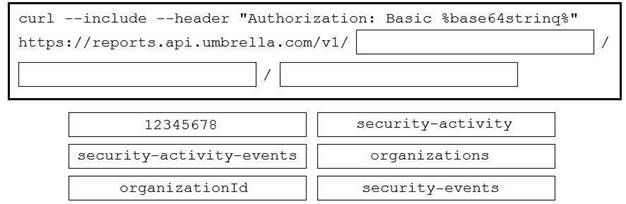
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 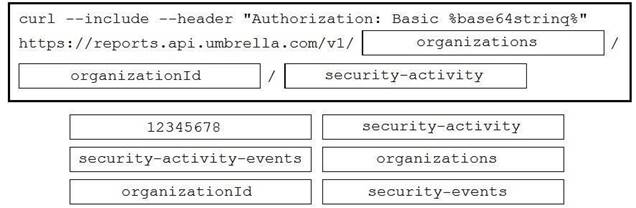
NEW QUESTION 2
DRAG DROP
Drag and drop the code to complete the Cisco Umbrella Investigate WHOIS query that returns a list of domains that are associated with the email address "admin@example.com". Not all options are used.
Select and Place:
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 3
When the URI "/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/policy/accesspolicies" is used to make a POST request, what does "e276abec-e0f2-11e3-8169- 6d9ed49b625f" represent?
- A. API token
- B. domain UUID
- C. access policy UUID
- D. object UUID
Answer: B
NEW QUESTION 4
Refer to the exhibit.
What is the purpose of the API represented by this URL?
- A. Getting or setting intrusion policies in FMC
- B. Creating an intrusion policy in FDM
- C. Updating access policies
- D. Getting the list of intrusion policies configured in FDM
Answer: D
NEW QUESTION 5
What is the purpose of the snapshot APIs exposed by Cisco Stealthwatch Cloud?
- A. Report on flow data during a customizable time period.
- B. Operate and return alerts discovered from infrastructure observations.
- C. Return current configuration data of Cisco Stealthwatch Cloud infrastructure.
- D. Create snapshots of supported Cisco Stealthwatch Cloud infrastructure.
Answer: B
NEW QUESTION 6
Which query parameter is required when using the reporting API of Cisco Security Management Appliances?
- A. device_type
- B. query_type
- C. filterValue
- D. startDate + endDate
Answer: D
NEW QUESTION 7
After changes are made to the Cisco Firepower Threat Defense configuration using the Cisco Firepower Device Manager API, what must be done to ensure that the new policy is activated?
- A. Submit a POST to the /api/fdm/latest/operational/deploy URI.
- B. Submit a GET to the /api/fdm/latest/operational/deploy URI.
- C. Submit a PUT to the /api/fdm/latest/devicesettings/pushpolicy URI.
- D. Submit a POST to the /api/fdm/latest/devicesettings/pushpolicy URI.
Answer: A
NEW QUESTION 8
Which two destinations are supported by the Cisco Security Management Appliance reporting APIs? (Choose two.)
- A. email
- B. Microsoft Word file
- C. FTP
- D. web
- E. csv file
Answer: AD
NEW QUESTION 9
What are two advantages of Python virtual environments? (Choose two.)
- A. Virtual environments can move compiled modules between different platforms.
- B. Virtual environments permit non-administrative users to install packages.
- C. The application code is run in an environment that is destroyed upon exit.
- D. Virtual environments allow for stateful high availability.
- E. Virtual environments prevent packaging conflicts between multiple Python projects.
Answer: CE
NEW QUESTION 10
In Cisco AMP for Endpoints, which API queues to find the list of endpoints in the group "Finance Hosts," which has a GUID of 6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03?
- A. https://api.amp.cisco.com/v1/endpoints?group[]=6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- B. https://api.amp.cisco.com/v1/computers?group_guid[]=6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- C. https://api.amp.cisco.com/v1/computers?group_guid-6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- D. https://api.amp.cisco.com/v1/endpoints?group-6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
Answer: B
NEW QUESTION 11
Refer to the exhibit. A security engineer attempts to query the Cisco Security Management appliance to retrieve details of a specific message. What must be added to the script to achieve the desired result?
- A. Add message ID information to the URL string as a URI.
- B. Run the script and parse through the returned data to find the desired message.
- C. Add message ID information to the URL string as a parameter.
- D. Add message ID information to the headers.
Answer: C
NEW QUESTION 12
Which two statements describe the characteristics of API styles for REST and RPC? (Choose two.)
- A. REST-based APIs function in a similar way to procedures.
- B. REST-based APIs are used primarily for CRUD operations.
- C. REST and RPC API styles are the same.
- D. RPC-based APIs function in a similar way to procedures.
- E. RPC-based APIs are used primarily for CRUD operations.
Answer: BD
NEW QUESTION 13
A security network engineer must implement intrusion policies using the Cisco Firepower Management Center API.
Which action does the engineer take to achieve the goal?
- A. Make a PATCH request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
- B. Make a POST request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
- C. Intrusion policies can be read but not configured using the Cisco Firepower Management Center API.
- D. Make a PUT request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
Answer: C
NEW QUESTION 14
Which snippet describes the way to create an URL object in Cisco FDM using FDM REST APIs with curl?
- A.
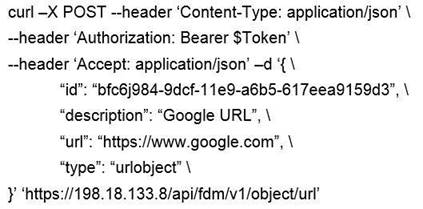
- B.
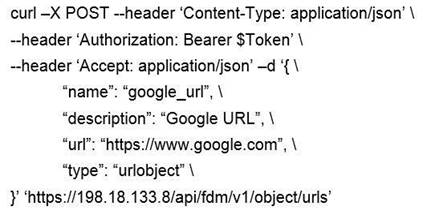
- C.
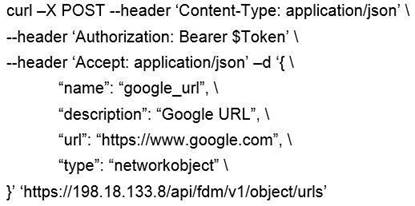
- D.
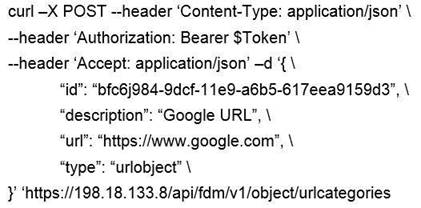
Answer: B
NEW QUESTION 15
Refer to the exhibit.
Which URL returned the data?
- A. https://api.amp.cisco.com/v1/computers
- B. https://api.amp.cisco.com/v0/computers
- C. https://amp.cisco.com/api/v0/computers
- D. https://amp.cisco.com/api/v1/computers
Answer: A
NEW QUESTION 16
Refer to the exhibit. A network operator wants to add a certain IP to a DMZ tag.
Which code segment completes the script and achieves the goal?
- A.

- B.

- C.

- D.

Answer: A
NEW QUESTION 17
Refer to the exhibit. A network operator wrote a Python script to retrieve events from Cisco AMP.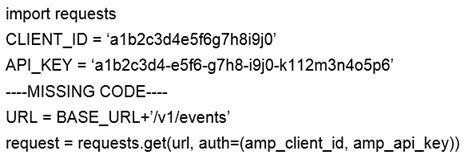
Against which API gateway must the operator make the request?
- A. BASE_URL = “https://api.amp.cisco.com”
- B. BASE_URL = “https://amp.cisco.com/api”
- C. BASE_URL = “https://amp.cisco.com/api/”
- D. BASE_URL = “https://api.amp.cisco.com/”
Answer: A
NEW QUESTION 18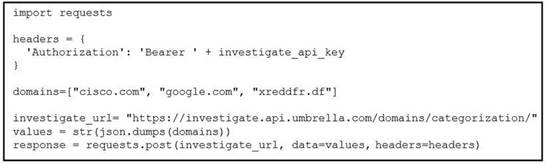
Refer to the exhibit.
What does the response from the API contain when this code is executed?
- A. error message and status code of 403
- B. newly created domains in Cisco Umbrella Investigate
- C. updated domains in Cisco Umbrella Investigate
- D. status and security details for the domains
Answer: D
NEW QUESTION 19
Which two commands create a new local source code branch? (Choose two.)
- A. git checkout -b new_branch
- B. git branch -b new_branch
- C. git checkout -f new_branch
- D. git branch new_branch
- E. git branch -m new_branch
Answer: AD
NEW QUESTION 20
FILL BLANK
Fill in the blank to complete the statement with the correct technology.
Cisco Investigate provides access to data that pertains to DNS security events and correlations collected by the Cisco security team.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Umbrella
NEW QUESTION 21
What are two benefits of Ansible when managing security platforms? (Choose two.)
- A. End users can be identified and tracked across a network.
- B. Network performance issues can be identified and automatically remediated.
- C. Policies can be updated on multiple devices concurrently, which reduces outage windows.
- D. Anomalous network traffic can be detected and correlated.
- E. The time that is needed to deploy a change is reduced, compared to manually applying the change.
Answer: CE
NEW QUESTION 22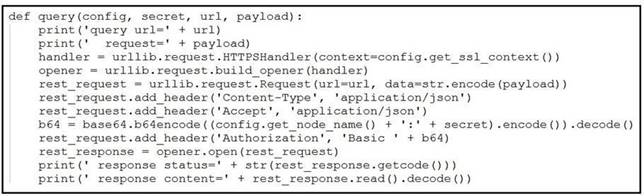
Refer to the exhibit. A Python function named "query" has been developed and the goal is to use it to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs. How is the function called, if the goal is to identify the sessions that are associated with the IP address 10.0.0.50?
- A. query(config, secret, "getSessionByIpAddress/10.0.0.50", "ipAddress")
- B. query(config, "10.0.0.50", url, payload)
- C. query(config, secret, url, "10.0.0.50")
- D. query(config, secret, url, '{"ipAddress": "10.0.0.50"}')
Answer: D
NEW QUESTION 23
Which two API capabilities are available on Cisco Identity Services Engine? (Choose two.)
- A. Platform Configuration APIs
- B. Monitoring REST APIs
- C. Performance Management REST APIs
- D. External RESTful Services APIs
- E. Internal RESTful Services APIs
Answer: BD
NEW QUESTION 24
Which header set should be sent with all API calls to the Cisco Stealthwatch Cloud API?
- A.

- B.
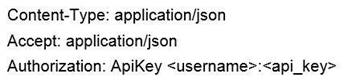
- C.

- D.

Answer: B
NEW QUESTION 25
......
100% Valid and Newest Version 300-735 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/300-735-pdf-download.html (New 0 Q&As)