Proper study guides for Abreast of the times EC-Council EC-Council Network Security Administrator (ENSA) certified begins with EC-Council 312-38 preparation products which designed to deliver the Certified 312-38 questions by making you pass the 312-38 test at your first time. Try the free 312-38 demo right now.
Free 312-38 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
Katie has implemented the RAID level that split data into blocks and evenly write the data to multiple hard drives but does not provide data redundancy. This type of RAID level requires a minimum of _______ in order to setup.
- A. Four drives
- B. Three drives
- C. Two drives
- D. Six drives
Answer: C
NEW QUESTION 2
Which of the information below can be gained through network sniffing? (Select all that apply)
- A. Telnet Passwords
- B. Syslog traffic
- C. DNS traffic
- D. Programming errors
Answer: ABC
NEW QUESTION 3
Alex is administrating the firewall in the organization's network. What command will he use to check the ports applications open?
- A. Netstat -an
- B. Netstat -o
- C. Netstat -a
- D. Netstat -ao
Answer: A
NEW QUESTION 4
Paul is a network security technician working on a contract for a laptop manufacturing company in Chicago. He has focused primarily on securing network devices, firewalls, and traffic traversing in and out of the network. He just finished setting up a server a gateway between the internal private network and the outside public network. This server will act as a proxy, limited amount of services, and will filter packets. What is this type of server called?
- A. Bastion host
- B. Edge transport server
- C. SOCKS hsot
- D. Session layer firewall
Answer: A
NEW QUESTION 5
Which of the following is a best practice for wireless network security?
- A. Enabling the remote router login
- B. Do not changing the default SSID
- C. Do not placing packet filter between the AP and the corporate intranet
- D. Using SSID cloaking
Answer: D
NEW QUESTION 6
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
- A. System Specific Security Policy (SSSP)
- B. Incident Response Policy (IRP)
- C. Enterprise Information Security Policy (EISP)
- D. Issue Specific Security Policy (ISSP)
Answer: A
NEW QUESTION 7
A network administrator is monitoring the network traffic with Wireshark. Which of the following filters will she use to view the packets moving without setting a flag to detect TCP Null Scan attempts?
- A. TCRflags==0x000
- B. Tcp.flags==0X029
- C. Tcp.dstport==7
- D. Tcp.flags==0x003
Answer: A
NEW QUESTION 8
Liza was told by her network administrator that they will be implementing IPsec VPN tunnels to connect the branch locations to the main office. What layer of the OSI model do IPsec tunnels function on?
- A. The data link layer
- B. The session layer
- C. The network layer
- D. The application and physical layers
Answer: C
NEW QUESTION 9
Management asked their network administrator to suggest an appropriate backup medium for their backup plan that best suits their organization's need. Which of the following factors will the administrator consider when deciding on the appropriate backup medium?
- A. Capability
- B. Accountability
- C. Extensibility
- D. Reliability
Answer: ACD
NEW QUESTION 10
Which VPN QoS model guarantees the traffic from one customer edge (CE) to another?
- A. Pipe Model
- B. AAA model
- C. Hub-and-Spoke VPN model
- D. Hose mode
Answer: A
NEW QUESTION 11
Identify the minimum number of drives required to setup RAID level 5.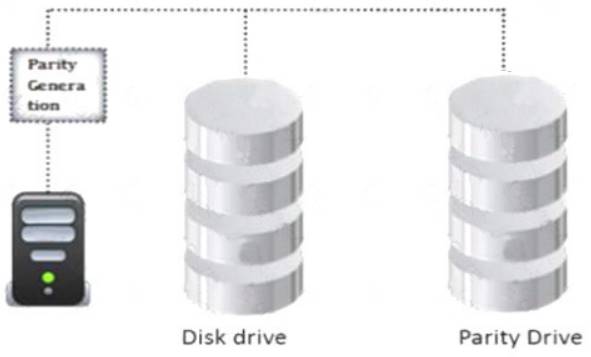
- A. Multiple
- B. 3
- C. 4
- D. 2
Answer: B
NEW QUESTION 12
-----------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
- A. 802.15.4
- B. 802.15
- C. 802.12
- D. 802.16
Answer: D
NEW QUESTION 13
Harry has sued the company claiming they made his personal information public on a social networking site in the United States. The company denies the allegations and consulted a/an ________ for legal advice to defend
them against this allegation.
- A. PR Specialist
- B. Attorney
- C. Incident Handler
- D. Evidence Manager
Answer: B
NEW QUESTION 14
Brendan wants to implement a hardware based RAID system in his network. He is thinking of choosing a suitable RAM type for the architectural setup in the system. The type he is interested in provides access times of up to 20 ns. Which type of RAM will he select for his RAID system?
- A. NVRAM
- B. SDRAM
- C. NAND flash memory
- D. SRAM
Answer: D
NEW QUESTION 15
Mark is monitoring the network traffic on his organization's network. He wants to detect a TCP and UDP ping sweep on his network. Which type of filter will be used to detect this on the network?
- A. Tcp.srcport==7 and udp.srcport==7
- B. Tcp.srcport==7 and udp.dstport==7
- C. Tcp.dstport==7 and udp.srcport==7
- D. Tcp.dstport==7 and udp.dstport==7
Answer: D
NEW QUESTION 16
Justine has been tasked by her supervisor to ensure that the company's physical security is on the same level as their logical security measures. She installs video cameras at all entrances and exits and installs badge access points for all doors. The last item she wants to install is a method to prevent unauthorized people piggybacking employees. What should she install to prevent piggybacking?
- A. She should install a mantrap
- B. Justine needs to install a biometrics station at each entrance
- C. Justine will need to install a revolving security door
- D. She should install a Thompson Trapdoor.
Answer: A
NEW QUESTION 17
Simon had all his systems administrators implement hardware and software firewalls to ensure network security. They implemented IDS/IPS systems throughout the network to check for and stop any unauthorized traffic that may attempt to enter. Although Simon and his administrators believed they were secure, a hacker group was able to get into the network and modify files hosted on the company's website. After searching through the firewall and server logs, no one could find how the attackers were able to get in. He decides that the entire network needs to be monitored for critical and essential file changes. This monitoring tool alerts administrators when a critical file is altered. What tool could Simon and his administrators implement to accomplish this?
- A. Snort is the best tool for their situation
- B. They can implement Wireshark
- C. They could use Tripwire
- D. They need to use Nessus
Answer: C
NEW QUESTION 18
Malone is finishing up his incident handling plan for IT before giving it to his boss for review. He is outlining the incident response methodology and the steps that are involved. Which step should Malone list as the last step in the incident response methodology?
- A. Malone should list a follow-up as the last step in the methodology
- B. Recovery would be the correct choice for the last step in the incident response methodology
- C. He should assign eradication to the last step.
- D. Containment should be listed on Malone's plan for incident response.
Answer: B
NEW QUESTION 19
Eric is receiving complaints from employees that their systems are very slow and experiencing odd issues including restarting automatically and frequent system hangs. Upon investigating, he is convinced the systems are infected with a virus that forces systems to shut down automatically after period of time. What type of security incident are the employees a victim of?
- A. Scans and probes
- B. Malicious Code
- C. Denial of service
- D. Distributed denial of service
Answer: B
NEW QUESTION 20
The network administrator wants to strengthen physical security in the organization. Specifically, to implement a solution stopping people from entering certain restricted zones without proper credentials. Which of following physical security measures should the administrator use?
- A. Bollards
- B. Fence
- C. Video surveillance
- D. Mantrap
Answer: B
NEW QUESTION 21
Identify the network topology where each computer acts as a repeater and the data passes from one computer to the other in a single direction until it reaches the destination.
- A. Ring
- B. Mesh
- C. Bus
- D. Star
Answer: A
NEW QUESTION 22
A network is setup using an IP address range of 0.0.0.0 to 127.255.255.255. The network has a default subnet mask of 255.0.0.0. What IP address class is the network range a part of?
- A. Class C
- B. Class A
- C. Class B
- D. Class D
Answer: B
NEW QUESTION 23
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is called a _______ and it has to adhere to the ________
- A. Verification, Security Policies
- B. Mitigation, Security policies
- C. Vulnerability scanning, Risk Analysis
- D. Risk analysis, Risk matrix
Answer: A
NEW QUESTION 24
......
Thanks for reading the newest 312-38 exam dumps! We recommend you to try the PREMIUM Certshared 312-38 dumps in VCE and PDF here: https://www.certshared.com/exam/312-38/ (330 Q&As Dumps)