It is impossible to pass Cisco 350-401 exam without any help in the short term. Come to Actualtests soon and find the most advanced, correct and guaranteed Cisco 350-401 practice questions. You will get a surprising result by our Renew Implementing and Operating Cisco Enterprise Network Core Technologies practice guides.
Cisco 350-401 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which statements are used for error handling in Python?
- A. try/catch
- B. try/except
- C. block/rescue
- D. catch/release
Answer: B
NEW QUESTION 2
Which two steps are required for a complete Cisco DNA Center upgrade? (Choose two.)
- A. golden image selection
- B. automation backup
- C. proxy configuration
- D. application updates
- E. system update
Answer: DE
NEW QUESTION 3
Which method displays text directly into the active console with a synchronous EEM applet policy?
- A. event manager applet boom event syslog pattern 'UP'action 1.0 gets 'logging directly to console'
- B. event manager applet boom event syslog pattern 'UP'action 1.0 syslog priority direct msg 'log directly to console'
- C. event manager applet boom event syslog pattern 'UP'action 1.0 puts 'logging directly to console'
- D. event manager applet boom event syslog pattern 'UP'action 1.0 string 'logging directly to console'
Answer: B
NEW QUESTION 4
Which exhibit displays a valid JSON file?
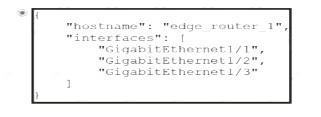
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 5
Refer to the exhibit.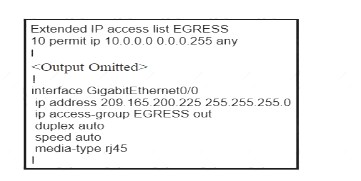
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router However, the router can still ping hosts on the 209.165.200.0/24 subnet. Which
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. Only standard access control lists can block traffic from a source IP address.
C. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
D. The access control list must contain an explicit deny to block traffic from the router.
Answer: A
NEW QUESTION 6
Refer to this output. What is the logging severity level?
R1#Feb 14 37:15:12:429: %LINEPROTO-5-UPDOWN Line protocol on interface GigabitEthernet0/1. Change state to up
- A. Notification
- B. Alert
- C. Critical
- D. Emergency
Answer: A
NEW QUESTION 7
When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
- A. logging host 10.2.3.4 vrf mgmt transport tcp port 6514
- B. logging host 10.2.3.4 vrf mgmt transport udp port 6514
- C. logging host 10.2.3.4 vrf mgmt transport tcp port 514
- D. logging host 10.2.3.4 vrf mgmt transport udp port 514
Answer: A
NEW QUESTION 8
What is the difference between a RIB and a FIB?
- A. The RIB is used to make IP source prefix-based switching decisions
- B. The FIB is where all IP routing information is stored
- C. The RIB maintains a mirror image of the FIB
- D. The FIB is populated based on RIB content
Answer: D
NEW QUESTION 9
Which statement explains why Type 1 hypervisor is considered more efficient than Type 2 hypervisor?
- A. Type 1 hypervisor runs directly on the physical hardware of the host machine without relying on the underlying OS.
- B. Type 1 hypervisor enables other operating systems to run on it.
- C. Type 1 hypervisor relics on the existing OS of the host machine to access CPU, memory, storage, andnetwork resources.
- D. Type 1 hypervisor is the only type of hypervisor that supports hardware acceleration techniques.
Answer: A
NEW QUESTION 10
Which NGFW mode block flows crossing the firewall?
- A. Passive
- B. Tap
- C. Inline tap
- D. Inline
Answer: C
NEW QUESTION 11
Drag and drop the description from the left onto the correct QoS components on the right.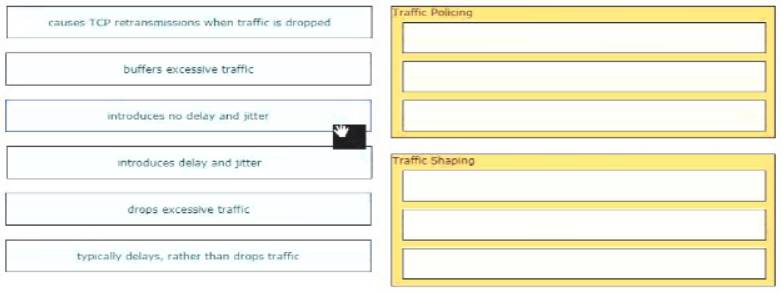
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Traffic Policing: Drops excessive Traffic, causes TCP retransmissions, introduce no delay/jitter Shaping: buffers, excessive traffic, introduce delay and jitter, typically delays, rather than drops traffic
NEW QUESTION 12
Which IP SLA operation requires the IP SLA responder to be configured on the remote end?
- A. ICMP echo
- B. UDP jitter
- C. CMP jitter
- D. TCP connect
Answer: D
NEW QUESTION 13
Which feature must be configured to allow packet capture over Layer 3 infrastructure'?
- A. VSPAN
- B. IPSPAN
- C. RSPAN
- D. ERSPAN
Answer: D
NEW QUESTION 14
What is the difference between the enable password and the enable secret password when service password encryption is enable on an IOS device?
- A. The enable password is encrypted with a stronger encryption method.
- B. There is no difference and both passwords are encrypted identically.
- C. The enable password cannot be decrypted.
- D. The enable secret password is protected via stronger cryptography mechanisms.
Answer: D
NEW QUESTION 15
What is the correct EBGP path attribute list, ordered from most preferred to the least preferred, that the BGP best-path algorithm uses?
- A. weigh
- B. AS path, local preferenc
- C. MED
- D. weight, local preference AS path, MED
- E. local preference weight AS path, MED
- F. local preference, weight MED, AS path
Answer: B
NEW QUESTION 16
Which statement about TLS is true when using RESTCONF to write configurations on network devices?
- A. It is provided using NGINX acting as a proxy web server.
- B. It is no supported on Cisco devices.
- C. It required certificates for authentication.
- D. It is used for HTTP and HTTPs requests.
Answer: C
NEW QUESTION 17
Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
- A. event manager applet ondemand event registeraction 1.0 syslog priority critical msg 'This is a message from ondemand'
- B. event manager applet ondemand event manualaction 1.0 syslog priority critical msg 'This is a message from ondemand'
- C. event manager applet ondemand event noneaction 1.0 syslog priority critical msg 'This is a message from ondemand'
- D. event manager applet ondemandaction 1.0 syslog priority critical msg 'This is a message from ondemand'
Answer: C
NEW QUESTION 18
Which standard access control entry permits from odd-numbered hosts in the 10.0.0.0/24 subnet?
- A. Permit 10.0.0.0.0.0.0.1
- B. Permit 10.0.0.1.0.0.0.0
- C. Permit 10.0.0.1.0.0.0.254
- D. Permit 10.0.0.0.255.255.255.254
Answer: C
NEW QUESTION 19
Refer to the exhibit.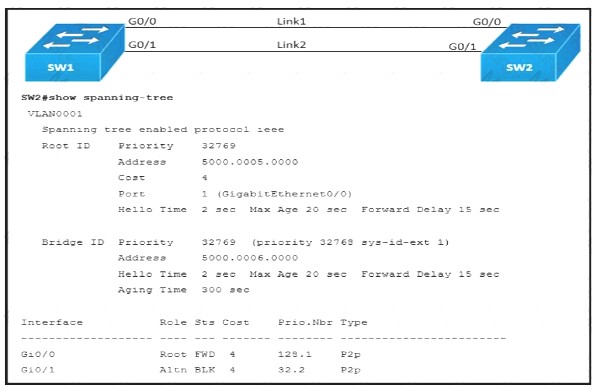
Link1 is a copper connection and Link2 is a fiber connection. The fiber port must be the primary port for all forwarding. The output of the show spanning-tree command on SW2 shows that the fiber port is blocked by spanning tree. An engineer enters the spanning- tree port-priority 32 command on GO/1 on SW2, but the port remains blocked. Which command should be entered on the ports that are connected to Link2 to resolve the issue?
- A. Enter spanning-tree port-priority 32 on SW1.
- B. Enter spanning-tree port-priority 224 on SW1.
- C. Enter spanning-tree port-priority 4 on SW2.
- D. Enter spanning-tree port-priority 64 on SW2.
Answer: A
NEW QUESTION 20
Which two methods are used by an AP that is typing to discover a wireless LAN controller? (Choose two.)
- A. Cisco Discovery Protocol neighbour
- B. broadcasting on the local subnet
- C. DNS lookup cisco-DNA-PRIMARY.localdomain
- D. DHCP Option 43
- E. querying other APs
Answer: CD
NEW QUESTION 21
Refer to the exhibit.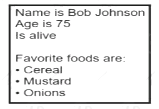
What is the JSON syntax that is formed the data?
- A. Name: Bob, Johson, Age: 75, Alive: true, Favourite Food
- B. [Cereal, ''Mustard'', ''Onions}}
- C. Name'', ''Bob'' Johson'', ''Age'', 75, ''Alive'', true, ''favourite Foods'', [''Cereal, ''Mustard'', Onions''}}
- D. Name', 'Bob Johson,' 'Age', 75, 'Alive', true, 'favourite Foods' 'Cereal’, ’Mustard', 'Onions'}
- E. Name''. ''Bob Johson'', ''Age'': Seventyfive, ''Alive'' true, ''favourite Foods'' ,[Cereal'' ''Mustard'' ''Onions''}}
Answer: C
NEW QUESTION 22
Which two descriptions of FlexConnect mode for Cisco APs are true? (Choose two.)
- A. APs that operate in FlexConnect mode cannot detect rogue Aps.
- B. FlexConnect mode is used when the APs are set up in a mesh environment and used to bridge between each other.
- C. FlexConnect mode is a feature that is designed to allow specified CAPWAP-enabled APs to exclude themselves from managing data traffic between clients and infrastructure.
- D. When connected to the controller, FlexConnect APs can tunnel traffic back to the controller.
- E. FlexConnect mode is a wireless solution for branch office and remote office deployments.
Answer: CD
NEW QUESTION 23
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
- A. LISP
- B. IS-IS
- C. Cisco TrustSec
- D. VXLAN
Answer: D
NEW QUESTION 24
Which two protocols are used with YANG data models? (Choose two.)
- A. HTTPS
- B. SSH
- C. RESTCONF
- D. TLS
- E. NFTCONF
Answer: CE
NEW QUESTION 25
......
P.S. Easily pass 350-401 Exam with 100 Q&As Passcertsure Dumps & pdf Version, Welcome to Download the Newest Passcertsure 350-401 Dumps: https://www.passcertsure.com/350-401-test/ (100 New Questions)