Master the 350-901 Developing Applications using Cisco Core Platforms & APIs content and be ready for exam day success quickly with this Testking 350-901 vce. We guarantee it!We make it a reality and give you real 350-901 questions in our Cisco 350-901 braindumps.Latest 100% VALID Cisco 350-901 Exam Questions Dumps at below page. You can use our Cisco 350-901 braindumps and pass your exam.
Cisco 350-901 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”. Which solution handles rate limiting by the remote API?
- A.
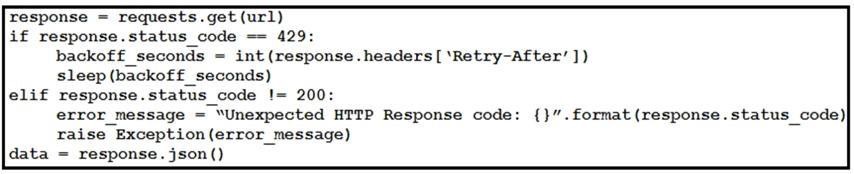
- B.

- C.
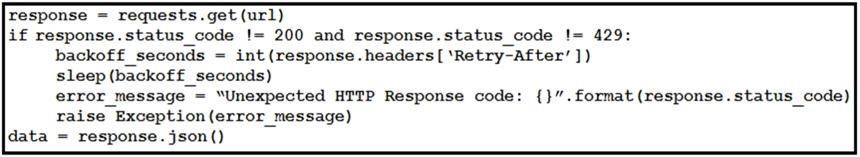
- D.
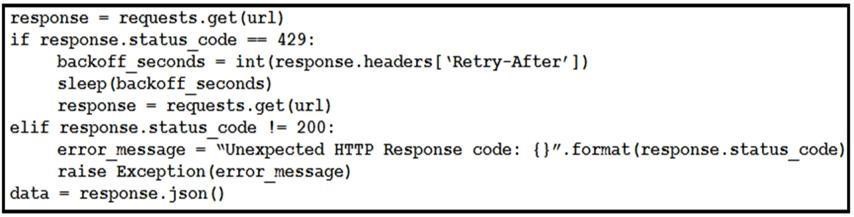
Answer: D
NEW QUESTION 2
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 3
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
- A. 202
- B. 401
- C. 429
- D. 503
Answer: C
NEW QUESTION 4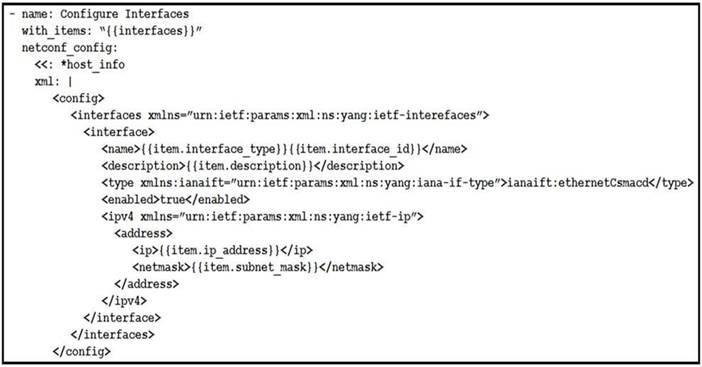
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
- A. ietf-interfaces and ietf-ip
- B. iana-if-type and ietf-interfaces
- C. ietf-ip and openconfig-interface
- D. ietf-ip and iana-if-type
Answer: B
NEW QUESTION 5
A heterogeneous network of vendors and device types needs automating for better efficiency and to enable future automated testing. The network consists of switches, routers, firewalls and load balancers from different vendors, however they all support the NETCONF/RESTCONF configuration standards and the YAML models with every feature the business requires. The business is looking for a buy versus build solution because they cannot dedicate engineering resources, and they need configuration diff and rollback functionality from day 1.
Which configuration management for automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 6
DRAG DROP
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
Select and Place: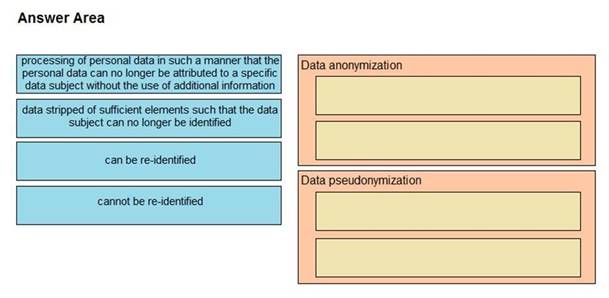
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 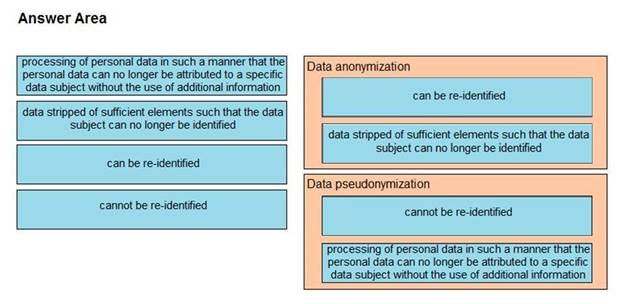
NEW QUESTION 7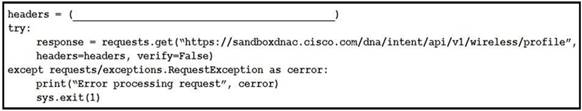
Refer to the exhibit. Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?
- A. headers = {‘X-auth-token’:’fa8426a0-8eaf-4d22-8e13-7c1b16a9370c’} B.headers = {‘Authorization’:’Basic YWRtaW46R3JhcGV2aW5IMQ==’}
- B. headers = {‘Authorization’:’Bearer ASDNFALKJER23412RKDALSNKF”}
- C. headers = {‘Content-type’:’application/json}
Answer: A
NEW QUESTION 8
Which transport protocol is used by gNMI?
- A. HTTP/2
- B. HTTP 1.1
- C. SSH
- D. MQTT
Answer: A
NEW QUESTION 9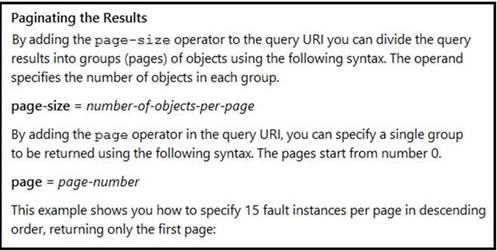
Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
- A. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=1&page-size=15
- B. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=2&page-size=15
- C. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=30
- D. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultinst.severity|desc&page=2&page-size=30
Answer: D
NEW QUESTION 10
Which two methods are API security best practices? (Choose two.)
- A. Use tokens after the identity of a client has been established.
- B. Use the same operating system throughout the infrastructure.
- C. Use encryption and signatures to secure data.
- D. Use basic auth credentials over all internal API interactions.
- E. Use cloud hosting services to manage security configuration.
Answer: AC
NEW QUESTION 11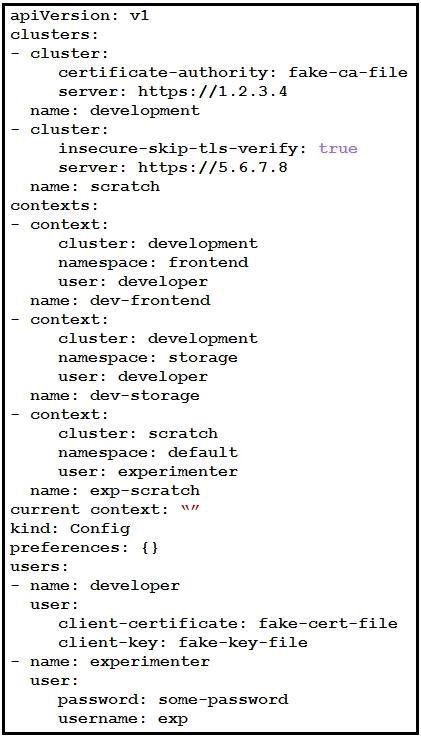
Refer to the exhibit. A kubeconfig file to manage access to clusters is provided. How many clusters are defined and which of them are accessed using username/password authentication versus certificate?
- A. two clusters; scratch
- B. three clusters; scratch
- C. three clusters; development
- D. two clusters; development
Answer: C
NEW QUESTION 12
Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
- A. This file is a container to log possible error responses in the request.
- B. This file is given as input to store the access token received from FDM.
- C. This file is used to send authentication related headers.
- D. This file contains raw data that is needed for token authentication.
Answer: B
NEW QUESTION 13
How should a web application be designed to work on a platform where up to 1000 requests per second can be served?
- A. Use algorithms like random early detection to deny excessive requests.
- B. Set a per-user limit (for example, 5 requests/minute/user) and deny the requests from the users who have reached the limit.
- C. Only 1000 user connections are allowed; further connections are denied so that all connected users can be served.
- D. All requests are saved and processed one by one so that all users can be served eventually.
Answer: D
NEW QUESTION 14
Which two strategies are used to protect personally identifiable information? (Choose two.)
- A. Encrypt data in transit.
- B. Encrypt hash values of data.
- C. Encrypt data at rest.
- D. Only hash usernames and passwords for efficient lookup.
- E. Only encrypt usernames and passwords for efficient lookup.
Answer: AB
NEW QUESTION 15
User report that they can no longer process transactions with the online ordering application, and the logging dashboard is displaying these messages.
Fri Jan 10 19:37:31.123 EST 2021 [FRONTEND] INFO: Incoming request to add item to cart from user 45834534858 Fri Jan 10 19:37:31 247 EST 2021 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31 250 EST 2021 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused What is causing the problem seen in these log messages?
- A. The database server container has crashed.
- B. The backend process is overwhelmed with too many transactions.
- C. The backend is not authorized to commit to the database.
- D. The user is not authorized to add the item to their cart.
Answer: A
NEW QUESTION 16
What is submitted when an SSL certificate is requested?
- A. PEM
- B. CRT
- C. DER
- D. CSR
Answer: D
NEW QUESTION 17
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
- A. Store data in a NoSQL database.
- B. Implement message authentication (HMAC).
- C. Enable end-to-end encryption.
- D. Remove stack traces from errors.
- E. Use short-lived access tokens.
Answer: BE
NEW QUESTION 18
Which two data encoding techniques are supported by gRPC? (Choose two.)
- A. XML
- B. JSON
- C. ASCII
- D. ProtoBuf
- E. YAML
Answer: BE
NEW QUESTION 19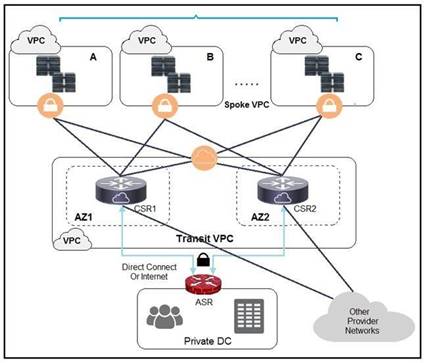
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
- A. Dynamic routing combined with multi-AZ- deployment creates a robust network infrastructure.
- B. VPC virtual gateways provide highly available connections to virtual networks.
- C. Dedicated VPC simplifies load balancing by combining internal and external web services.
- D. VPC virtual gateways provide more secure connections to virtual networks.
- E. Dedicated VPC simplifies routing by not combining this service with other shared services.
Answer: BD
NEW QUESTION 20
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
- A. It checks for potential tainted data where input is not checked.
- B. It enforces proper coding standards and style.
- C. It performs a quick analysis of whether tests will pass or fail when run.
- D. It checks for race conditions in threaded applications.
- E. It estimates the performance of the code when run.
Answer: BC
NEW QUESTION 21
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
- A. rate limiting
- B. time outs
- C. caching
- D. redirection
Answer: A
NEW QUESTION 22
Which two statements are considered best practices according to the 12-factor app methodology for application design? (Choose two.)
- A. Application code writes its event stream to stdout.
- B. Application log streams are archived in multiple replicated databases.
- C. Application log streams are sent to log indexing and analysis systems.
- D. Application code writes its event stream to specific log files.
- E. Log files are aggregated into a single file on individual nodes.
Answer: AD
NEW QUESTION 23
......
Thanks for reading the newest 350-901 exam dumps! We recommend you to try the PREMIUM 2passeasy 350-901 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/350-901/ (0 Q&As Dumps)