We provide real 400-251 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Cisco 400-251 Exam quickly & easily. The 400-251 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Cisco 400-251 dumps pdf and vce product and material, you can easily pass the 400-251 exam.
NEW QUESTION 1
Which of the following correctly describes NVGRE functionality?
- A. In NVGRE network the endpoints are not responsible for the NVGRE encapsulation removal
- B. It allows to create physical layer-2 topologies on physical layer-3 network
- C. It tunnels PPP frames inside an IP packet over a physical network
- D. In NVGRE network VSID does not need to be unique
- E. It tunnels Ethernet frames inside an IP packet over a virtual network
- F. It allows to create physical layer-2 topologies on virtual layer-3 network
- G. In NVGRE network VSID is used to identify tenant’s address space
Answer: G
NEW QUESTION 2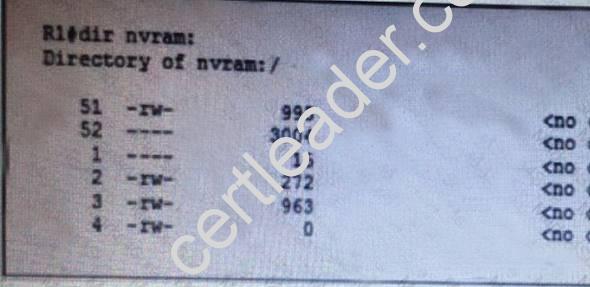
Refer to the exhibit. Which statement about router R1 is true?
- A. Its NVRAM contains public and private crypto keys
- B. RMON is configured
- C. Its private-config is corrupt
- D. Its startup configuration is missing
- E. It running configuration is missing
Answer: A
Explanation:
https://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/50282-ios-caios. html
NEW QUESTION 3
Which description of a Botnet attack is true ?
- A. It can be used to participate in DDOS
- B. It is from a wireless attack where the attacker installs an access point to create backdoor to a network
- C. It is launched by collection of non compromised machines controlled by the command and control system
- D. It is launched by a single machine controlled by the command and Control system
- E. It is from of a fragmentation attack to evade an intrusion prevention security device
- F. It is a from of a man-in-the-middle attack where the compromised machine is controlled remotely
Answer: A
NEW QUESTION 4
Which statement is true regarding securing connection using MACsec?
- A. It secures connection between two supplicant clients
- B. Switch uses session keys to calculate decrypted packet ICV value for the frame integrity check
- C. Switch configured for MACSec can only accept MACSec frames from the MACSec client
- D. It is implemented after a successful MAB authentication of supplicant
- E. It provides network layer encryption on a wireless network
- F. ISAKMP protocol is used to manage MACSec encryption keys
Answer: B
NEW QUESTION 5
Which statement about the failover link when ASAs are configured in the failover mode is true?
- A. The information sent over the failover link can he sent only as a secured communication
- B. The information sent over the failover link cannot be sent in clear text, but it could be secured communication using a failover key
- C. It is not recommended to use secure communication over the failover link when ASA terminating the VPN tunnel
- D. Only the configuration replication that is sent across the link can be secured using a failover key
- E. The information sent over the failover link can be in clear text
- F. Failover key is not required for the secure communication over the failover link
Answer: E
NEW QUESTION 6
Which statement about MDM with the Cisco ISE is true?
- A. The MDM’s server certificate must be imported into the Cisco ISE Certificate Store before the MDM andISE can establish a connection.
- B. MDM servers can generate custom ACLs for the Cisco ISE to apply to network devices.
- C. The Cisco ISE supports a built-in list of MDM dictionary attributes it can use in authorization policies.
- D. The Cisco ISE supports limited built-in MDM functionality.
- E. If a mobile endpoint fails posture compliance, both the user and the administrator are notified immediately.
- F. When a mobile endpoint becomes compliant the Cisco ISE records the updated device status in its internal database.
Answer: A
Explanation:
Mobile Device Management https://meraki.cisco.com/blog/tag/mobile-device-management/
NEW QUESTION 7
Refer to the exhibit.
What are two effects of the given configuration? (Choose two.)
- A. It enables the ASA to download the static botnet filter database.
- B. It enables the ASA to download the dynamic botnet filter database.
- C. It enables botnet filtering in single context mode.
- D. It enables botnet filtering in mutiple context mode.
- E. It enables multiple context mode.
- F. It enables single context mode.
Answer: BD
NEW QUESTION 8
Which three statements about 802.1x multiauthentication mode are true? (Choose three.)
- A. It is recommended for guest VLANs.
- B. On non-802.1x devices, it can support only one authentication method on a single port.
- C. Each multiauthentication port can support only one voice VLAN.
- D. It is recommended for auth-fall VLANs.
- E. It requires each connected client to authenticate individually.
- F. It can be deployed in conjunction with MDA functionality on voice VLANs.
Answer: CEF
NEW QUESTION 9
Which definition of Machine Access Restriction is true?
- A. MAR offer security information and event management
- B. MAR provides detailed malware analysis reports
- C. MAR identifies threats on the cisco network by “learning” the topology, configuration and behavior you environment
- D. MAR is feature introduced into ISE and ACS as a way to verify a successful machine authenticated
- E. MAR provides user authentication
Answer: D
NEW QUESTION 10
Which statement is true regarding the wireless security technologies?
- A. WPA provides message integrity using AES
- B. WPA2-PSK mode allows passphrase to store locally on the device
- C. WEP is more secure than WPA2 because it uses AES for encryption
- D. WPA-ENT mode does not require RADIUS for authentication
- E. WPÁ2-PSK mode provides better security by having same passphrase across the network
- F. WPA2 is more secure than WPA because it uses TKIP for encryption
Answer: A
NEW QUESTION 11
Refer to the exhibit.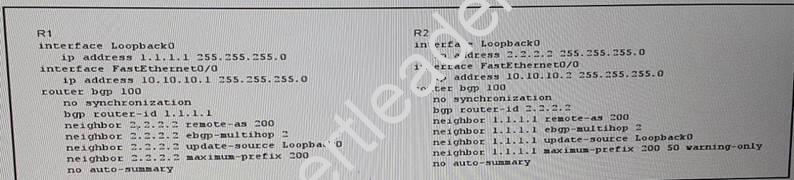
Which two effects of this configuration are true? (Choose two.)
- A. The BGP neighbor session between R1 and R2 re-establishes after 100 minutes.
- B. A warning message is displayed on R2 after it receives 50 prefixes.
- C. A warning message is displayed on R2 after it receives 100 prefixes from neighbor 1.1.1.1.
- D. The BGP neighbor session between R1 and R2 re-establishes after 50 minutes.
- E. The BGP neighbor session tears down after R1 receive 100 prefixes from neighbor 1.1.1.1.
- F. The BGP neighbor session tears down after R1 receive 200 prefixes from neighbor 2.2.2.2.
Answer: CF
NEW QUESTION 12
196) Which four tasks are needed to configure RSA token authenticate
- A. Generate the sdconf.rec file on the RSA server for the authenticate
- B. Add the ACS server to the allowed ODBC query list on the server
- C. Define an OSBC client connection on the SRA server
- D. On the ACS server, define the ODBC connection and the s RSA server
- E. Define an authentication agent on the RSA server
- F. Add the RSA server as an external identity serve on ACS
- G. Define an accounting agent on the RSA server
- H. Upload the sdconf.rec to the ACS server
Answer: AEFH
NEW QUESTION 13
Refer to the exhibit. Refer to the exhibit.
FMC with address 161.1.7.15 is not seeing AMP connector scan events reported to
AMP cloud from "test-pc" windows machine that belongs to "Protect" group. What could be the issue?
- A. Windows machine not reporting scan events to AMP cloud
- B. Windows machine not reporting events to FMC
- C. Incorrect group is selected for the events export in AMP cloud for FMC
- D. AMP cloud not added in FMC
- E. FMC not added in AMP cloud
- F. Windows machine belongs to incorrect group in AMP cloud policy.
- G. Event should be viewed as "Connection" event in FMC
Answer: F
NEW QUESTION 14
Refer to the exhibit.
Which effect of this command is true?
- A. The route immediately deletes its current public key from the cache and generates a new one.
- B. The public key of the remote peer is deleted from the router cache.
- C. The CA revokes the public key certificate of the router.
- D. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.
- E. The router sends a request to the CA to delete the router certificate from its configuration.
Answer: B
NEW QUESTION 15
Which two options can be used to further harden a Cisco Email Security Appliance? (Choose two.)
- A. Disable telnet
- B. Rename the default administrator password
- C. Disable HTTP and FTP services that are not required
- D. Enable Cisco Discovery Protocol
- E. Turn off TCP small services
Answer: AB
NEW QUESTION 16
All your employees are required to authenticate their devices to the network, be it company owned or employee owned assets, with ISE as the authentication server. The primary identity store used is Microsoft
Active directory, with username and password authentication. To ensure the security of your enterprise, your security policy dictates that only company owned assets should be able to get access to the enterprise network, while personal assets should have restricted access. Which option would allow you to enforce this policy using only ISE and Active Directory?
- A. Configure an authentication policy that uses the computer credentials in Active Directory to determine whether the device is company owned or personal.
- B. This would require deployment of a Mobile Device Management (MDM) solution, which can be used to register all devices against the MDM server, and use that to assign appropriate access levels.
- C. Configure an authentication policy that checks against the MAC address database of company assets in ISE endpoint identity store to determine the level of access depending on the device.
- D. Configure an authorization policy that checks against the MAC address database of company assets in ISE endpoint identity store to determine the level of access depending on the device.
- E. Configure an authorization policy that assigns the device the appropriate profile based on whether the device passes Machine Authentication or not.
Answer: D
NEW QUESTION 17
Which statement is true about Remote Triggered Black Hole Filtering feature (RTBH)?
- A. It drops malicious traffic at the customer edge router by forwarding it to a Null0 interface
- B. In RTBH filtering the trigger device redistributes static route to the iBGP peers
- C. The Null0 interface used for filtering is able to receive the traffic, but never forwards it
- D. It works in conjunction with QoS to drop the traffic that has less priority
- E. It helps mitigate DDoS attack based only on source address
- F. In FTBH filtering the trigger device is always an ISP edge router
Answer: B
NEW QUESTION 18
A customer is developing a strategy to deal with Wanna Cry variants that defect sandboxing attempts and mask their present analyzed. Which four mechanisms can be used in this strategy?
- A. Employ a DNS forwarder that responds to unknown domain names with a reachable IP (honey pot) that can mimic sandboxing containment responses and alert when a possible threat is detected.
- B. Apply route maps at the access layer that prevent all RPC and SMB communication throughout the network.
- C. Ensure that the standard desktop image used in the organization is an actively supported operating system and that security patches are applied.
- D. Run antimalware software on user endpoints and servers as well as ensure regular signature updates.
- E. Ensure that vulnerable services used for propagation of malware such as SMB are blocked on publicfacing segments.
- F. Employ URL/DNS inspection mechanisms that blackhole the reques
- G. This action prevents malware from communicating with unknown domains and thus prevents the WannaCry malware from becoming active.
- H. Apply ACLs at the access layer that prevents all RPC and SMP communication throughout the network..
Answer: DEFG
NEW QUESTION 19
Which statement correctly represents the ACI security principle of Object Model?
- A. It is logical representation of an application and its interdependencies in the network fabric
- B. It is policy placed at the intersection of a source and destination EPGs.
- C. It is defined by the policy applied between EPGs for communication.
- D. lt consists of one or more tenants having multiple contexts.
- E. These are rules and policies used by an EPG to communicate with other EPGs.
- F. It is collection of endpoints representing an application with in a context.
Answer: D
NEW QUESTION 20
Which statement is true about Social Engineering attack?
- A. It uses the reconnaissance method for exploitation.
- B. It is a method of extracting a non-confidential information.
- C. The "Phishing" technique is one of the ways to launch the attack.
- D. It is always performed through an email from a person that you know.
- E. It is always done by having malicious ads on untrusted websites for the users to browse.
- F. It can be only done by a person who is not part of the organization.
Answer: A
NEW QUESTION 21
Refer to the exhibit. aaa new-model
aaa authentication login default group radius aaa authentication login NO_AUTH none aaa authentication login vty local
aaa authentication dot1x default group radius aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
!u
sername cisco privilege 15 password 0 cisco dot1x system-auth-control
!i
nterface GigabitEthernet0/2 switchport mode access
ip access-group Pre-Auth in authentication open authentication port-control auto dot1x pae authenticator
!v
lan 50
interface Vlan50
ip address 50.1.1.1 255.255.255.0
!i
p dhcp excluded-address 5.1.1.1 ip dhcp pool pc-pool
network 50.1.1.0 255.255.255.0
default-router 50.1.1.1
!i
p access-list extended Pre-Auth
permit udp any eq bootpc any eq bootps deny ip any any
!
radius server ccie
address ipv4 161.1.7.14 auth-port 1645 acct-port 1646 key cisco
!l
ine con 0
login authentication NO_AUTH lien vty 0 4
login authentication vty
One of the Windows machines in your network is having connectivity issues using
802.1 x. Windows machines are set up to acquire an address from the DHCP server configured on the switch, which is supposed to hand out IP addresses from the 50.1.1.0/24 network and forward AAA requests to the RADIUS server at 161.1.7.14 using the key "cisco". Knowing that the interface Gi0/2 on the switch may receive authentication requests from other devices and looking at the provided switch
configuration, what could be the possible cause of this failure?
- A. There ia a RADIUS key mismatch
- B. 802.1x is disabled on the switch
- C. aaa network authorization is not configured
- D. Authentication for multiple hosts is not configured on interface Gi0/2
- E. An incorrect IP address was configured on SVI 50
- F. An incorrect default route is pushed on the supplicant form SW1
- G. 802.1x authentication is not enabled on the interface Gi0/2
Answer: D
NEW QUESTION 22
Which two options are unicast address types for IPv6 addressing? (Choose two.)
- A. static
- B. link-local
- C. established
- D. dynamic
- E. global
Answer: BE
NEW QUESTION 23
Which two statements about SPAN sessions are true? (Choose two.)
- A. A single switch stack can support up to 32 source and RSPAN destination sessions.
- B. Source ports and source VLANs can be mixed in the same session
- C. They can monitor sent and received packets in the same session.
- D. Multiple SPAN sessions can use the same destination port.
- E. Local SPAN and RSPAN can be mixed in the same session.
- F. They can be configured on ports in the disabled state before enabling the port.
Answer: CF
NEW QUESTION 24
Refer to the exhibit.
What feature must be implemented on the network to produce the given output?
- A. CAR
- B. PQ
- C. WFQ
- D. NBAR
- E. CQ
Answer: D
NEW QUESTION 25
Refer to the exhibit.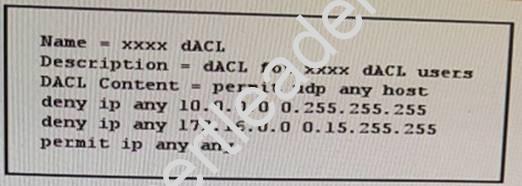
For which type of user is this downloadable ACL appropriate?
- A. management
- B. employees
- C. guest users
- D. network administrator
- E. onside contractors
Answer: C
NEW QUESTION 26
Which statement description of the Strobe scan is true?
- A. It never opens a full TCP connection.
- B. It relies on ICMP "port unreachable" message to determine if the port is open.
- C. It is used to find the ports that already have an existing vulnerability to exploit.
- D. It checks the firewall deployment in the path.
- E. It is a directed scan to a known TCP/UDP port.
- F. It evades network auditing tools.
Answer: C
NEW QUESTION 27
......
100% Valid and Newest Version 400-251 Questions & Answers shared by Exambible, Get Full Dumps HERE: https://www.exambible.com/400-251-exam/ (New 448 Q&As)