We provide real 412-79v10 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass EC-Council 412-79v10 Exam quickly & easily. The 412-79v10 PDF type is available for reading and printing. You can print more and practice many times. With the help of our EC-Council 412-79v10 dumps pdf and vce product and material, you can easily pass the 412-79v10 exam.
NEW QUESTION 1
Paulette works for an IT security consulting company that is currently performing an audit for the firm
ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit: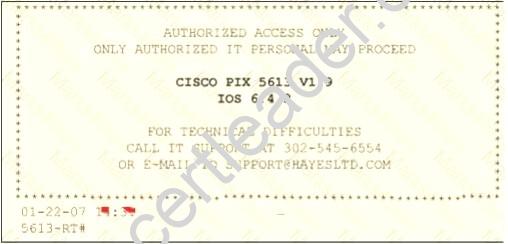
- A. The banner should not state "only authorized IT personnel may proceed"
- B. Remove any identifying numbers, names, or version information
- C. The banner should include the Cisco tech support contact information as well
- D. The banner should have more detail on the version numbers for the network equipment
Answer: B
NEW QUESTION 2
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and G.
Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- A. 802.11b
- B. 802.11g
- C. 802.11-Legacy
- D. 802.11n
Answer: A
NEW QUESTION 3
Which of the following scan option is able to identify the SSL services?
- A. –sS
- B. –sV
- C. –sU
- D. –sT
Answer: B
NEW QUESTION 4
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.
What are the two types of ‘white-box’ penetration testing?
- A. Announced testing and blind testing
- B. Blind testing and double blind testing
- C. Blind testing and unannounced testing
- D. Announced testing and unannounced testing
Answer: D
NEW QUESTION 5
The SnortMain () function begins by associating a set of handlers for the signals, Snort receives. It does this using the signal () function. Which one of the following functions is used as a programspecific signal and the handler for this calls the DropStats() function to output the current Snort statistics?
- A. SIGUSR1
- B. SIGTERM
- C. SIGINT
- D. SIGHUP
Answer: A
NEW QUESTION 6
SQL injection attacks are becoming significantly more popular amongst hackers and there has been an estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal sensitive data from web applications. It takes advantage of non-validated input vulnerabilities to pass SQL commands through a web application for execution by a back-end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.
Which of the following can the attacker use to launch an SQL injection attack?
- A. Blah' “2=2 –“
- B. Blah' and 2=2 --
- C. Blah' and 1=1 --
- D. Blah' or 1=1 --
Answer: D
NEW QUESTION 7
Jim performed a vulnerability analysis on his network and found no potential problems. He runs another utility that executes exploits against his system to verify the results of the vulnerability test. The second utility executes five known exploits against his network in which the vulnerability analysis said were not exploitable.
What kind of results did Jim receive from his vulnerability analysis?
- A. True negatives
- B. False negatives
- C. False positives
- D. True positives
Answer: B
NEW QUESTION 8
What is a good security method to prevent unauthorized users from "tailgating"?
- A. Electronic key systems
- B. Man trap
- C. Pick-resistant locks
- D. Electronic combination locks
Answer: B
NEW QUESTION 9
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 10
Which of the following is the objective of Gramm-Leach-Bliley Act?
- A. To ease the transfer of financial information between institutions and banks
- B. To protect the confidentiality, integrity, and availability of data
- C. To set a new or enhanced standards for all U.
- D. public company boards, management and public accounting firms
- E. To certify the accuracy of the reported financial statement
Answer: A
NEW QUESTION 11
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
- A. Information-Protection Policy
- B. Special-Access Policy
- C. Remote-Access Policy
- D. Acceptable-Use Policy
Answer: C
NEW QUESTION 12
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?
- A. Service-based Assessment Solutions
- B. Product-based Assessment Solutions
- C. Tree-based Assessment
- D. Inference-based Assessment
Answer: C
NEW QUESTION 13
An "idle" system is also referred to as what?
- A. Zombie
- B. PC not being used
- C. Bot
- D. PC not connected to the Internet
Answer: A
NEW QUESTION 14
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
- A. Circuit-level proxy firewall
- B. Packet filtering firewall
- C. Application-level proxy firewall
- D. Statefull firewall
Answer: D
NEW QUESTION 15
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
- A. Inference-based Assessment
- B. Service-based Assessment Solutions
- C. Product-based Assessment Solutions
- D. Tree-based Assessment
Answer: A
NEW QUESTION 16
John, the penetration testing manager in a pen testing firm, needs to prepare a pen testing pricing report for a client. Which of the following factors does he need to consider while preparing the pen testing pricing report?
- A. Number of employees in the client organization
- B. Complete structure of the organization
- C. Number of client computers to be tested and resources required to perform a pen test
- D. Number of servers available in the client organization
Answer: C
NEW QUESTION 17
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.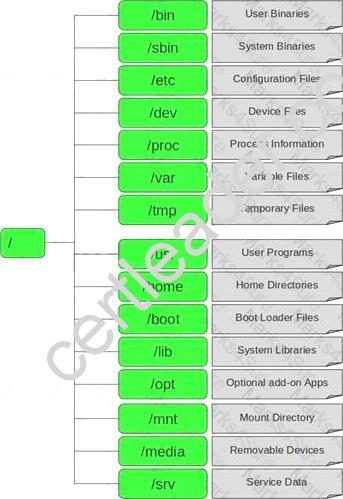
In the example of a /etc/shadow file below, what does the bold letter string indicate?
Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
- A. Number of days the user is warned before the expiration date
- B. Minimum number of days required between password changes
- C. Maximum number of days the password is valid
- D. Last password changed
Answer: B
NEW QUESTION 18
In the context of penetration testing, what does blue teaming mean?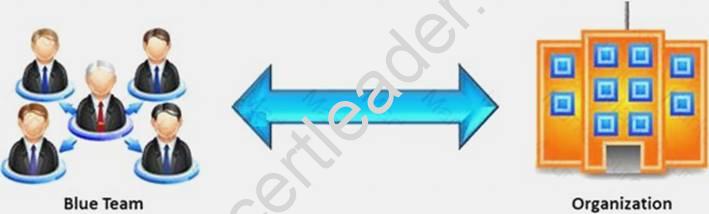
- A. A penetration test performed with the knowledge and consent of the organization's IT staff
- B. It is the most expensive and most widely used
- C. It may be conducted with or without warning
- D. A penetration test performed without the knowledge of the organization's IT staff but with permission from upper management
Answer: A
NEW QUESTION 19
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?
- A. Reverse Address Resolution Protocol (RARP)
- B. HTTP (Hypertext Transfer Protocol)
- C. SMTP (Simple Mail Transfer Protocol)
- D. Telnet
Answer: A
NEW QUESTION 20
How many bits is Source Port Number in TCP Header packet?
- A. 48
- B. 32
- C. 64
- D. 16
Answer: D
NEW QUESTION 21
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
- A. SSI injection attack
- B. Insecure cryptographic storage attack
- C. Hidden field manipulation attack
- D. Man-in-the-Middle attack
Answer: B
NEW QUESTION 22
Security auditors determine the use of WAPs on their networks with Nessus vulnerability scanner which identifies the commonly used WAPs.
One of the plug-ins that the Nessus Vulnerability Scanner uses is ID #11026 and is named “Access Point Detection”. This plug-in uses four techniques to identify the presence of a WAP.
Which one of the following techniques is mostly used for uploading new firmware images while upgrading the WAP device?
- A. NMAP TCP/IP fingerprinting
- B. HTTP fingerprinting
- C. FTP fingerprinting
- D. SNMP fingerprinting
Answer: C
NEW QUESTION 23
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 24
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 25
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 26
As a security analyst you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
- A. The employees network usernames and passwords
- B. The MAC address of the employees' computers
- C. The IP address of the employees computers
- D. Bank account numbers and the corresponding routing numbers
Answer: C
NEW QUESTION 27
Which Wireshark filter displays all the packets where the IP address of the source host is 10.0.0.7?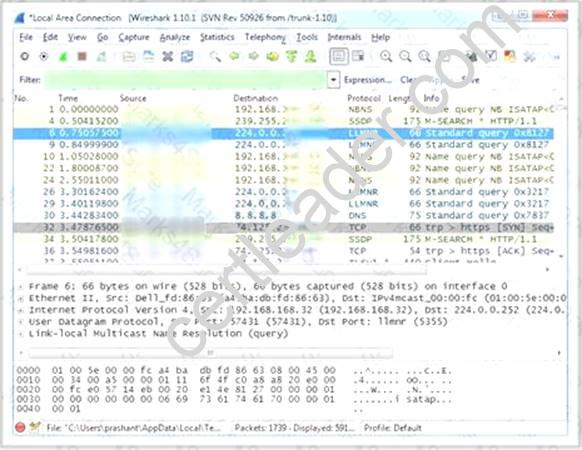
- A. ip.dst==10.0.0.7
- B. ip.port==10.0.0.7
- C. ip.src==10.0.0.7
- D. ip.dstport==10.0.0.7
Answer: C
NEW QUESTION 28
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
- A. Connect Scanning Techniques
- B. SYN Scanning Techniques
- C. Stealth Scanning Techniques
- D. Port Scanning Techniques
Answer: C
NEW QUESTION 29
......
Thanks for reading the newest 412-79v10 exam dumps! We recommend you to try the PREMIUM Dumpscollection 412-79v10 dumps in VCE and PDF here: http://www.dumpscollection.net/dumps/412-79v10/ (201 Q&As Dumps)