AZ-102 Exam Questions are updated and AZ-102 Braindumps are verified by experts. Once you have completely prepared with our AZ-102 Dumps Questions you will be ready for the real AZ-102 exam without a problem. We have AZ-102 Braindumps. PASSED AZ-102 Study Guides First attempt! Here What I Did.
Free AZ-102 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
You have an Azure subscription that contains the resources in the following table.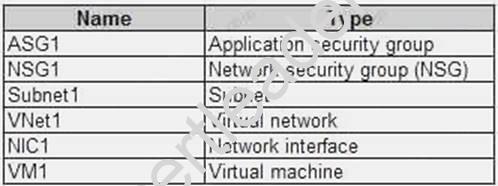
Subnet1 is associated to VNet1. NIC1 attaches VM1 to Subnet1. You need to apply ASG1 to VM1.
What should you do?
- A. Modify the properties of NSG1.
- B. Modify the properties of ASG1.
- C. Associate NIC1 to ASG1.
Answer: B
Explanation: When you deploy VMs, make them members of the appropriate ASGs. You associate the ASG with a subnet.
References: https://azure.microsoft.com/en-us/blog/applicationsecuritygroups/
NEW QUESTION 2
You download an Azure Resource Manager template based on an existing virtual machine. The template will be used to deploy 100 virtual machines.
You need to modify the template to reference an administrative password. You must prevent the password from being stored in plain text.
What should you create to store the password?
- A. Azure Active Directory (AD) Identity Protection and an Azure policy
- B. a Recovery Services vault and a backup policy
- C. an Azure Key Vault and an access policy
- D. an Azure Storage account and an access policy
Answer: C
Explanation: You can use a template that allows you to deploy a simple Windows VM by retrieving the password that is stored in a Key Vault. Therefore the password is never put in plain text in the template parameter file.
References: https://azure.microsoft.com/en-us/resources/templates/101-vm-secure-password/
NEW QUESTION 3
HOT SPOT
You are evaluating the name resolution for the virtual machines after the planned implementation of the Azure networking infrastructure.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.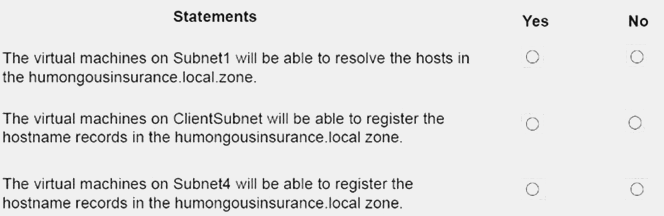
Answer:
Explanation: Scenario: You plan to create a private DNS zone named humongousinsurance.local and set the registration network to the ClientResources-VNet virtual network.
There is a virtual network named ClientResources-VNet that will contain one subnet named ClientSubnet
Note: Azure DNS provides the following capabilities:
Automatic registration of virtual machines from a single virtual network that's linked to a private zone as a registration virtual network.
Forward DNS resolution is supported across virtual networks that are linked to the private zone as resolution virtual networks.
Reverse DNS lookup is supported within the virtual-network scope.
References:
https://docs.microsoft.com/en-us/azure/dns/private-dns-overview
NEW QUESTION 4
You have an Azure virtual network named VNet1 that contains a subnet named Subnet1. Subnet1 contains three Azure virtual machines. Each virtual machine has a public IP address.
The virtual machines host several applications that are accessible over port 443 to user on the Internet.
Your on-premises network has a site-to-site VPN connection to VNet1.
You discover that the virtual machines can be accessed by using the Remote Desktop Protocol (RDP) from the Internet and from the on-premises network.
You need to prevent RDP access to the virtual machines from the Internet, unless the RDP connection is established from the on-premises network. The solution must ensure that all the applications can still be accesses by the Internet users.
What should you do?
- A. Modify the address space of the local network gateway.
- B. Remove the public IP addresses from the virtual machines.
- C. Modify the address space of Subnet1.
- D. Create a deny rule in a network security group (NSG) that is linked to Subnet1.
Answer: D
Explanation: You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
References:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
NEW QUESTION 5
HOT SPOT
You have an Azure subscription named Subscription1. Subscription1 contains the virtual machines in the following table.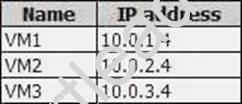
Subscription1 contains a virtual network named VNet1 that has the subnets in the following table.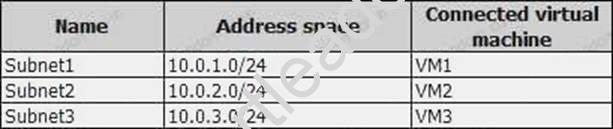
VM3 has a network adapter named NIC3. IP forwarding is enabled on NIC3. Routing is enabled on VM3.
You create a route table named RT1. RT1 is associated to Subnet1 and Subnet2 and contains the routes in the following table.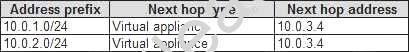
You apply RT1 to Subnet1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.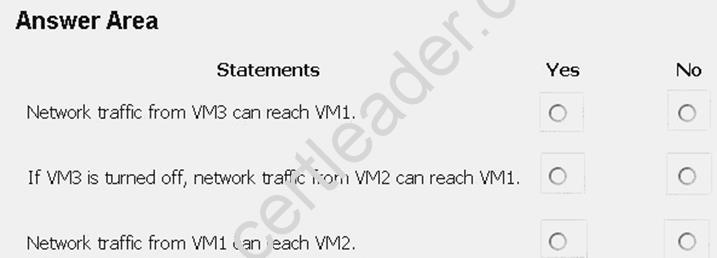
Answer:
Explanation: Box 1: Yes
Traffic from VM1 and VM2 can reach VM3 thanks to the routing table, and as IP forwarding is enabled on VM3, traffic from VM3 can reach VM1.
Box 2: No
VM3, which has IP forwarding, must be turned on, in order for traffic from VM2 to reach VM1. Box 3: Yes
The traffic from VM1 will reach VM3, which thanks to IP forwarding, will send the traffic to VM2. References: https://www.quora.com/What-is-IP-forwarding
NEW QUESTION 6
You need to recommend a solution to automate the configuration for the finance department users. The solution must meet the technical requirements.
What should you include in the recommended?
- A. Azure AP B2C
- B. Azure AD Identity Protection
- C. an Azure logic app and the Microsoft Identity Management (MIM) client
- D. dynamic groups and conditional access policies
Answer: D
Explanation: Scenario: Ensure Azure Multi-Factor Authentication (MFA) for the users in the finance department only.
The recommendation is to use conditional access policies that can then be targeted to groups of users, specific applications, or other conditions.
References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates
NEW QUESTION 7
DRAG DROP
You have an Azure subscription that contains an Azure Service Bus named Bus1.
Your company plans to deploy two Azure web apps named App1 and App2. The web apps will create messages that have the following requirements:
Each message created by App1 must be consumed by only a single consumer Each message created by App2 will be consumed by multiple consumers.
Which resource should you create for each web app? To answer, drag the appropriate resources to the correct web apps. Each resource may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.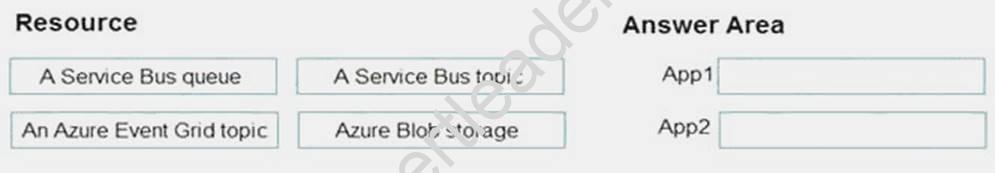
Answer:
Explanation: 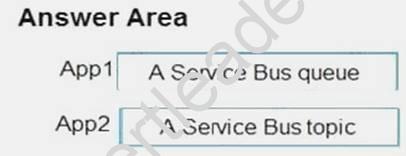
NEW QUESTION 8
DRAG DROP
You need to prepare the New York office infrastructure for the migration of the on-premises virtual machines to Azure.
Which four actions you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.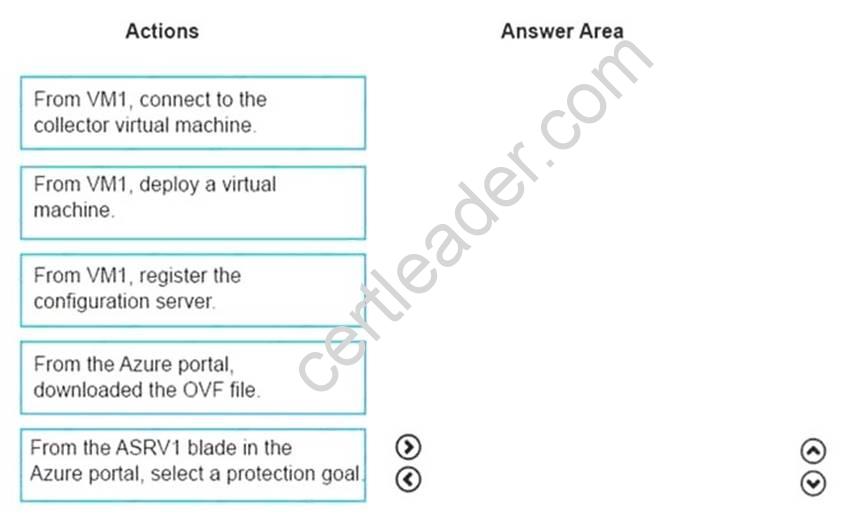
Answer:
Explanation: Box 1:
From the Azure portal, download the OVF file.
In the vCenter Server, import the Collector appliance as a virtual machine using the Deploy OVF Template wizard.
In vSphere Client console, click File > Deploy OVF Template.
In the Deploy OVF Template Wizard > Source, specify the location for the .ovf file. Box 2: From VM1, connect to the collector virtual machine
After you've created the Collector virtual machine, connect to it and run the Collector. Box 3: From the ASRV1 blade in the Azure portal, select a protection goal.
Box 4: From VM1, register the configuration server. Register the configuration server in the vault
Scenario: The Azure infrastructure and the on-premises infrastructure and the on-premises infrastructure must be prepared for the migration of the VMware virtual machines to Azure. References:
Migrate Your Virtual Machines to Microsoft Azure, Includes guidance for optional data migration, Proof of Concept guide, September 2021 https://azuremigrate.blob.core.windows.net/publicpreview/Azure%20Migrate%20-
%20Preview%20User%20Guide.pdf
NEW QUESTION 9
DRAG DROP
You have an Azure subscription that contains a storage account.
You have an on-premises server named Server1 that runs Window Server 2021. Server1 has 2 TB of data.
You need to transfer the data to the storage account by using the Azure Import/Export service.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.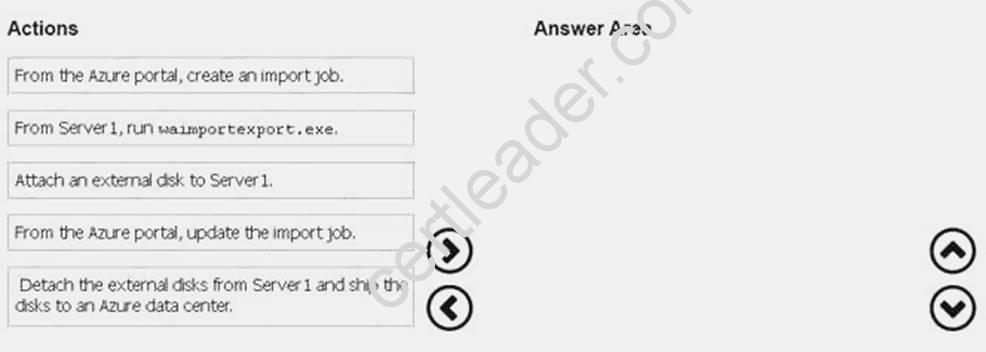
Answer:
Explanation: 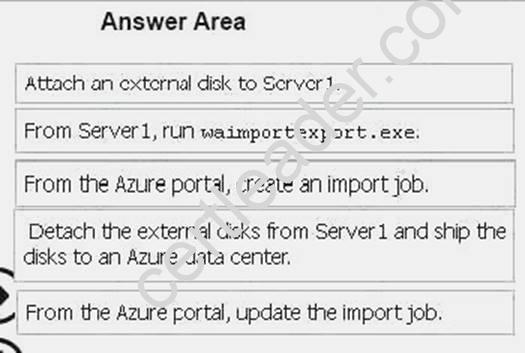
NEW QUESTION 10
HOT SPOT
You have an Azure Active Directory (Azure AD) tenant.
You need to create a conditional access policy that requires all users to use multi-factor authentication when they access the Azure portal.
Which three settings should you configure? To answer, select the appropriate settings in the answer area.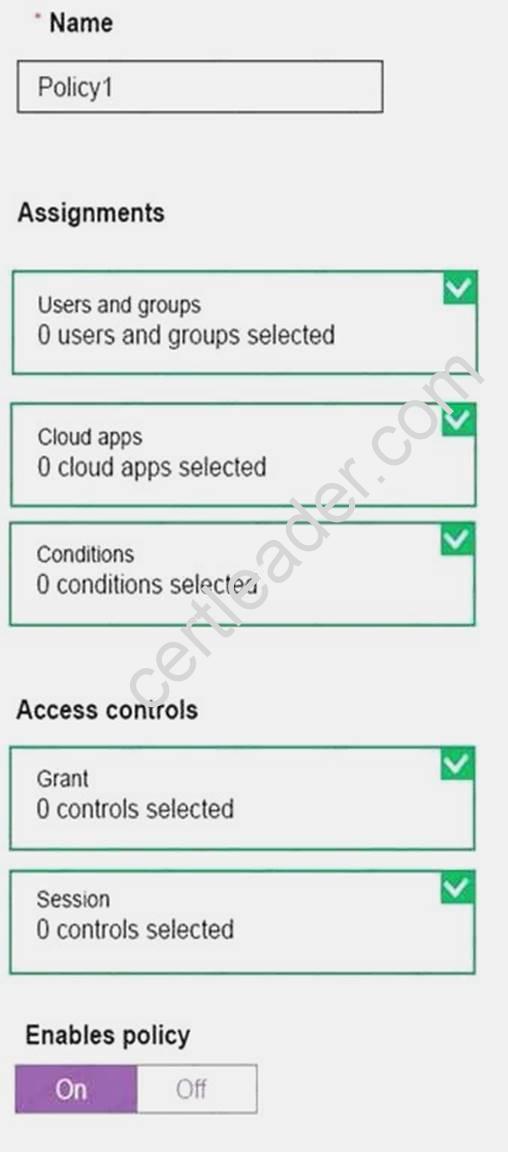
Answer:
Explanation: Box 1: Assignments, Users and Groups
When you configure the sign-in risk policy, you need to set:
The users and groups the policy applies to: Select Individuals and Groups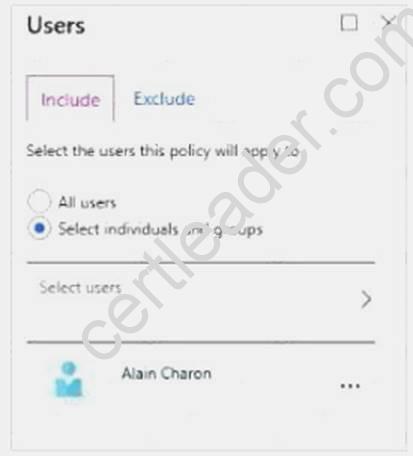
Box 2:
When you configure the sign-in risk policy, you need to set the type of access you want to be enforced.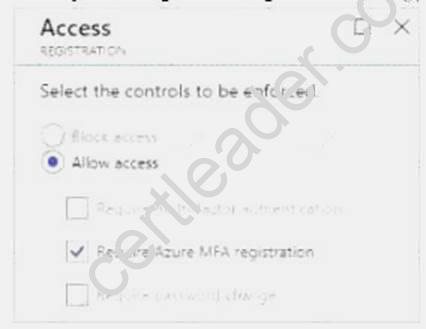
Box 3:
When you configure the sign-in risk policy, you need to set:
The type of access you want to be enforced when your sign-in risk level has been met: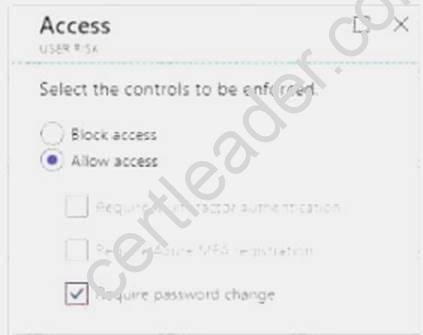
References:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-user-risk-policy
NEW QUESTION 11
You have an Azure subscription named Subscription1 that has the following providers registered: Authorization
Automation Resources Compute KeyVault Network Storage Billing Web
Subscription1 contains an Azure virtual machine named VM1 that has the following configurations: Private IP address: 10.0.0.4 (dynamic)
Network security group (NSG): NSG1 Public IP address: None
Availability set: AVSet Subnet: 10.0.0.0/24 Managed disks: No Location: East US
You need to record all the successful and failed connection attempts to VM1.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Register the Microsoft.Insights resource provider
- B. Add an Azure Network Watcher connection monitor
- C. Register the Microsoft.LogAnalytics provider
- D. Enable Azure Network Watcher in the East US Azure region
- E. Create an Azure Storage account
- F. Enable Azure Network Watcher flow logs
Answer: ADF
Explanation:
Step 1: (D)
We must have a network watcher enabled in the East US region Step 2: (A+F)
A: NSG flow logging requires the Microsoft.Insights provider, which must be registered.
F: Network security groups (NSG) allow or deny inbound or outbound traffic to a network interface in a VM. The NSG flow log capability allows you to log the source and destination IP address, port, protocol, and whether traffic was allowed or denied by an NSG.
References:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-portal
NEW QUESTION 12
HOT SPOT
You have a virtual network named VNet1 that has the configuration shown in the following exhibit.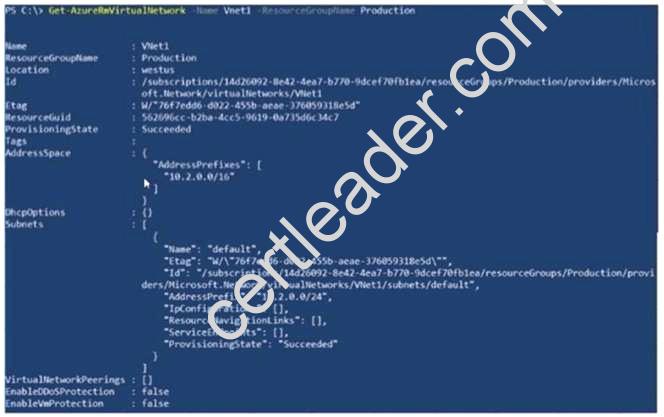
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.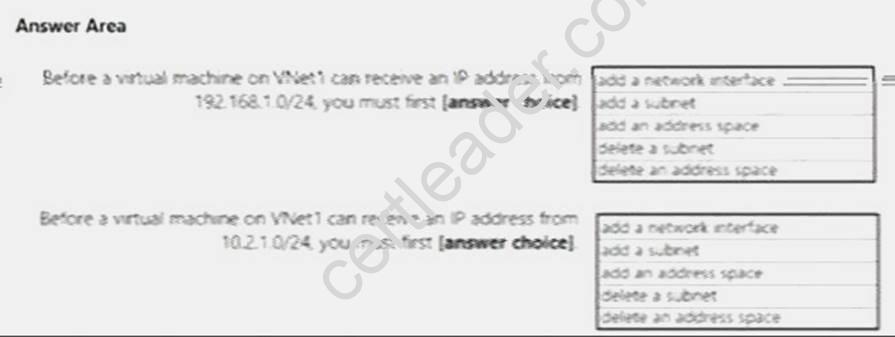
Answer:
Explanation: Box 1: add a subnet
Your IaaS virtual machines (VMs) and PaaS role instances in a virtual network automatically receive a private IP address from a range that you specify, based on the subnet they are connected to. We
need to add the 192.168.1.0/24 subnet. Box 2: add a network interface
The 10.2.1.0/24 network exists. We need to add a network interface.
References: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-static-privateip- arm-pportal
NEW QUESTION 13
You have two Azure virtual networks named VNet1 and VNet2. VNet1 contains an Azure virtual
machine named VM1. VNet2 contains an Azure virtual machine named VM2. VM1 hosts a frontend application that connects to VM2 to retrieve data. Users report that the frontend application is slower than usual.
You need to view the average round-trip time (RTT) of the packets from VM1 to VM2. Which Azure Network Watcher feature should you use?
- A. NSG flow logs
- B. Connection troubleshoot
- C. IP flow verify
- D. Connection monitor
Answer: D
Explanation: The Connection Monitor feature in Azure Network Watcher is now generally available in all public regions. Connection Monitor provides you RTT values on a per-minute granularity. You can monitor a direct TCP connection from a virtual machine to a virtual machine, FQDN, URI, or IPv4 address. References:
https://azure.microsoft.com/en-us/updates/general-availability-azure-network-watcher-connectionmonitor- in-all-public-regions/
NEW QUESTION 14
You are the global administrator for an Azure Active Directory (Azure AD) tenant named adatum.com.
You need to enable two-step verification for Azure users. What should you do?
- A. Configure a playbook in Azure AD conditional access policy.
- B. Create an Azure AD conditional access policy.
- C. Create and configure the Identify Hub.
- D. Install and configure Azure AD Connec
Answer: B
Explanation: References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
NEW QUESTION 15
Note: This questions is part of a series of questions that present the same scenario. Each questions in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution. After you answer a questions in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription. You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You assign a built-in policy definition to the subscription. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 16
You need to deploy an application gateway named appgwl015 to meet the following requirements: Load balance internal IP traffic to the Azure virtual machines connected to subnet0.
Provide a Service Level Agreement (SLA) of 99.99 percent availability for the Azure virtual machines. What should you do from the Azure portal?
Answer:
Explanation: Step 1:
Click New found on the upper left-hand corner of the Azure portal. Step 2:
Select Networking and then select Application Gateway in the Featured list. Step 3:
Enter these values for the application gateway: appgw1015 - for the name of the application gateway. SKU Size: Standard_V2
The new SKU [Standard_V2] offers autoscaling and other critical performance enhancements.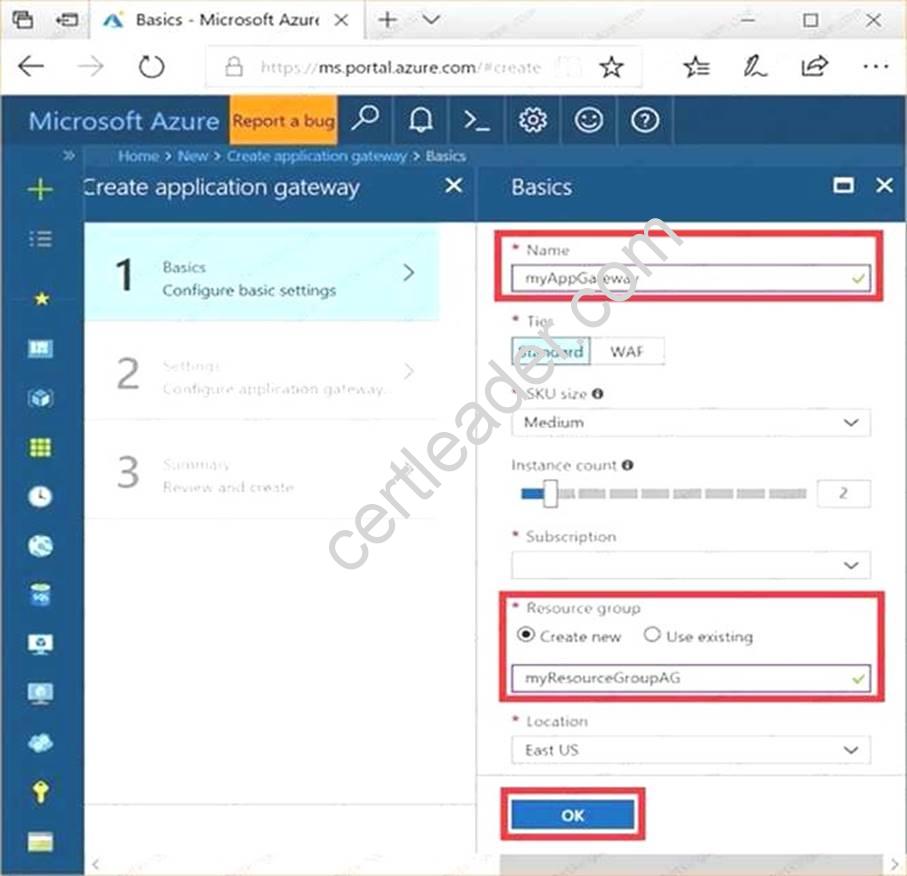
Step 4:
Accept the default values for the other settings and then click OK. Step 5:
Click Choose a virtual network, and select subnet0.
References:
https://docs.microsoft.com/en-us/azure/application-gateway/application-gateway-create-gatewayportal
NEW QUESTION 17
DRAG DROP
You are developing an Azure web app named WebApp1. WebApp1 uses an Azure App Service plan named Plan1 that uses the B1 pricing tier.
You need to configure WebApp1 to add additional instances of the app when CPU usage exceeds 70 percent for 10 minutes.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.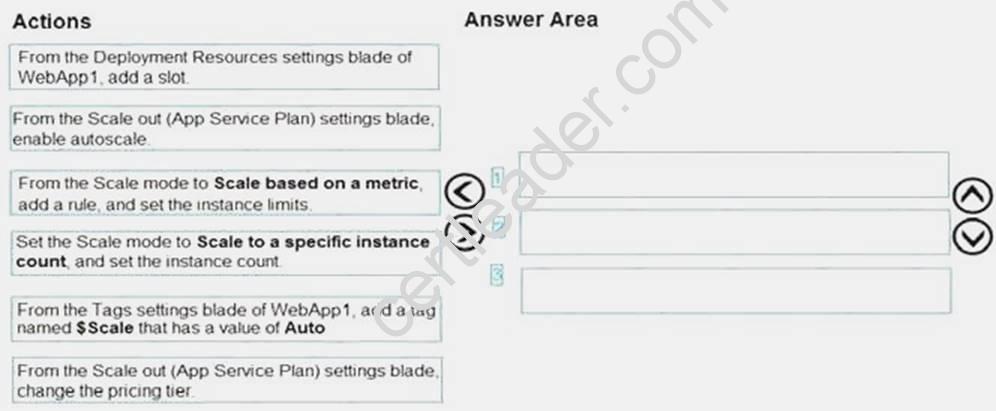
Answer:
Explanation: Box 1: From the Scale out (App Service Plan) settings blade, change the pricing tier The B1 pricing tier only allows for 1 core. We must choose another pricing tier. Box 2: From the Scale out (App Service Plan) settings blade, enable autoscale
Log in to the Azure portal at http://portal.azure.com Navigate to the App Service you would like to autoscale. Select Scale out (App Service plan) from the menu
Click on Enable autoscale. This activates the editor for scaling rules.
Box 3: From the Scale mode to Scale based on metric, add a rule, and set the instance limits.
Click on Add a rule. This shows a form where you can create a rule and specify details of the scaling. References:
https://azure.microsoft.com/en-us/pricing/details/app-service/windows/ https://blogs.msdn.microsoft.com/hsirtl/2021/07/03/autoscaling-azure-web-apps/
NEW QUESTION 18
You create an Azure subscription that is associated to a basic Azure Active Directory (Azure AD) tenant. You need to receive an email notification when any user activates an administrative role. What should you do?
- A. Purchase Azure AD Premium 92 and configure Azure AD Privileged Identity Management,
- B. Purchase Enterprise Mobility + Security E3 and configure conditional access policies.
- C. Purchase Enterprise Mobility + Security E5 and create a custom alert rule in Azure Security Center.
- D. Purchase Azure AD Premium PI and enable Azure AD Identity Protectio
Answer: A
Explanation: When key events occur in Azure AD Privileged Identity Management (PIM), email notifications are sent. For example, PIM sends emails for the following events:
When a privileged role activation is pending approval When a privileged role activation request is completed When a privileged role is activated
When a privileged role is assigned When Azure AD PIM is enabled References:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pimemail- notifications
NEW QUESTION 19
HOT SPOT
You plan to use Azure Network Watcher to perform the following tasks:
Task1: Identify a security rule that prevents a network packet from reaching an Azure virtual machine.
Task2: Validate outbound connectivity from an Azure virtual machine to an external host.
Which feature should you use for each task? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:
Explanation: Task 1: IP flow verify
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
Task 2:
With the addition of Connection Troubleshoot, Network Watcher will see an incremental increase in its capabilities and ways for you to utilize it in your day to day operations. You can now, for example, check connectivity between source (VM) and destination (VM, URI, FQDN, IP Address). References:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview https://azure.microsoft.com/en-us/blog/network-watcher-connection-troubleshoot-now-generallyavailable/
NEW QUESTION 20
Which blade should you instruct the finance department auditors to use?
- A. Cost analysis
- B. Usage + quotas
- C. External services
- D. Payment methods
Answer: B
Explanation: Subscription costs are based on usage. Microsoft Azure limits are also called quotas.
Scenario: During the testing phase, auditors in the finance department must be able to review all Azure costs from the past week.
Incorrect Answers:
C: External services are published by third party software vendors in the Azure marketplace. References: https://docs.microsoft.com/en-us/azure/azure-subscription-service-limits
100% Valid and Newest Version AZ-102 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/AZ-102-exam-dumps.html (New 195 Q&As)