Exam Code: AZ-303 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Microsoft Azure Architect Technologies (beta)
Certification Provider: Microsoft
Free Today! Guaranteed Training- Pass AZ-303 Exam.
Free AZ-303 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Your company has the groups shown in the following table.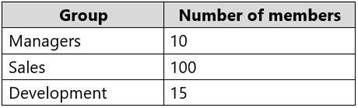
The company has an Azure subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
An administrator named Admin1 attempts to enable Enterprise State Roaming for all the users in the Managers group.
Admin1 reports that the options for Enterprise State Roaming are unavailable from Azure AD. You verify that Admin1 is assigned the Global administrator role.
You need to ensure that Admin1 can enable Enterprise State Roaming. What should you do?
- A. Enforce Azure Multi-Factor Authentication (MFA) for Admin1.
- B. Purchase an Azure AD Premium P1 license for each user in the Managers group.
- C. Assign an Azure AD Privileged Identity Management (PIM) role to Admin1.
- D. Purchase an Azure Rights Management (Azure RMS) license for each user in the Managers group.
Answer: B
Explanation:
Enterprise State Roaming is available to any organization with an Azure AD Premium or Enterprise Mobility
+ Security (EMS) license.
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/devices/enterprise-state-roaming-enable
NEW QUESTION 2
You have an Azure subscription that contains the Azure SQL servers shown in the following table.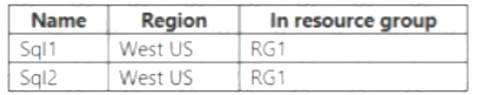
The subscription contains the elastic pool shown in the following table.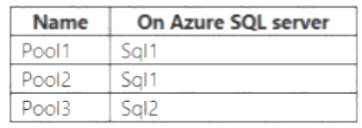
The subscription contains the Azure SQL databases shown in the following table.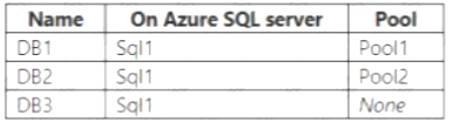
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.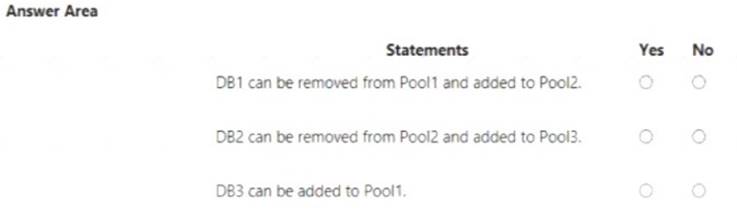
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Note: You cannot add databases from different servers into the same pool Box 1: Yes
Pool2 contains DB2 but DB1 and DB2 are on Sql1. DB1 can thus be added to Pool2. Box 2: Yes
Pool3 is empty. Box 3: Yes
Pool1 contains DB1 but DB3 and DB1 are on Sql1. DB3 can thus be added to Pool1. References:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-elastic-pool
NEW QUESTION 3
You have 10 Azure virtual machines on a subnet named Subnet1. Subnet1 is on a virtual network named VNet1.
You plan to deploy a public Azure Standard Load Balancer named LB1 to the same Azure region as the 10 virtual machines.
You need to ensure that traffic from all the virtual machines to the internet flows through LB1. The solution must prevent the virtual machines from being accessible on the internet.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Add health probes to LB1.
- B. Add the network interfaces of the virtual machines to the backend pool of LB1.
- C. Add an inbound rule to LB1.
- D. Add an outbound rule to LB1.
- E. Associate a network security group (NSG) to Subnet1.
- F. Associate a user-defined route to Subnet1.
Answer: ABD
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/load-balancer/tutorial-load-balancer-standard-manage-portal2
NEW QUESTION 4
You have resources in three Azure regions. Each region contains two virtual machines. Each virtual machine has a public IP address assigned to its network interface and a locally installed application named App1.
You plan to implement Azure Front Door-based load balancing across all the virtual machines.
You need to ensure that App1 on the virtual machines will only accept traffic routed from Azure Front Door. What should you implement?
- A. Azure Private Link
- B. service endpoints
- C. network security groups (NSGs) with service tags
- D. network security groups (NSGs) with application security groups
Answer: C
Explanation:
Configure IP ACLing for your backends to accept traffic from Azure Front Door's backend IP address space and Azure's infrastructure services only. Refer the IP details below for ACLing your backend: Refer AzureFrontDoor.Backend section in Azure IP Ranges and Service Tags for Front Door's IPv4 backend IP address range or you can also use the service tag AzureFrontDoor.Backend in your network security groups.
Refer AzureFrontDoor.Backend section in Azure IP Ranges and Service Tags for Front Door's IPv4 backend IP address range or you can also use the service tag AzureFrontDoor.Backend in your network security groups.
Reference:
https://docs.microsoft.com/en-us/azure/frontdoor/front-door-faq
NEW QUESTION 5
You have SQL Server on an Azure virtual machine named SQL1.
You need to automate the backup of the databases on SQL1 by using Automated Backup v2 for the virtual machines. The backups must meet the following requirements:
• Meet a recovery point objective (RPO) of 15 minutes.
• Retain the backups for 30 days.
• Encrypt the backups at rest.
What should you provision as part of the backup solution?
- A. Azure Key Vault
- B. an Azure Storage account
- C. a Recovery Services vault
- D. Elastic Database jobs
Answer: B
Explanation:
An Azure storage account is used for storing Automated Backup files in blob storage. A container is created at this location to store all backup files. The backup file naming convention includes the date, time, and database GUID.
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/virtual-machines/windows/automated-backup
NEW QUESTION 6
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server 2019. Server1 is a container host. You are creating a Dockerfile to build a container image.
You need to add a file named File1.txt from Server1 to a folder named C:\Folder1 in the container image. Solution: You add the following line to the Dockerfile.
COPY File1.txt /Folder1/
You then build the container image. Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation:
Copy is the correct command to copy a file to the container image. References:
https://docs.docker.com/develop/develop-images/dockerfile_best-practices/#add-or-copy https://docs.docker.com/engine/reference/builder/
NEW QUESTION 7
You have an application named App1 that does not support Azure Active Directory (Azure AD) authentication.
You need to ensure that App1 can send messages to an Azure Service Bus queue. The solution must prevent Appl from listening to the queue.
What should you do?
- A. Modify the locks of the Queue
- B. Configure Access control (IAM) for the Service Bus
- C. Configure Access control (IAM) for the queue.
- D. Add a shared access policy to the queue
Answer: D
Explanation:
There are two ways to authenticate and authorize access to Azure Service Bus resources: Azure Activity Directory (Azure AD) and Shared Access Signatures (SAS).
Each Service Bus namespace and each Service Bus entity has a Shared Access Authorization policy made up of rules.
Reference:
https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-authentication-and-authorization https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-sas
NEW QUESTION 8
You are planning the move of App1 to Azure. You create a network security group (NSG).
You need to recommend a solution to provide users with access to App1. What should you recommend?
- A. Create an outgoing security rule for port 443 from the Interne
- B. Associate the NSG to all the subnets.
- C. Create an incoming security rule for port 443 from the Interne
- D. Associate the NSG to all the subnets.
- E. Create an incoming security rule for port 443 from the Interne
- F. Associate the NSG to the subnet that contains the web servers.
- G. Create an outgoing security rule for port 443 from the Interne
- H. Associate the NSG to the subnet that contains the web servers.
Answer: C
Explanation:
As App1 is public-facing we need an incoming security rule, related to the access of the web servers. Scenario: You have a public-facing application named App1. App1 is comprised of the following three tiers: a SQL database, a web front end, and a processing middle tier.
Each tier is comprised of five virtual machines. Users access the web front end by using HTTPS only.
NEW QUESTION 9
You have several Azure virtual machines on a virtual network named VNet1. You configure an Azure Storage account as shown in the following exhibit.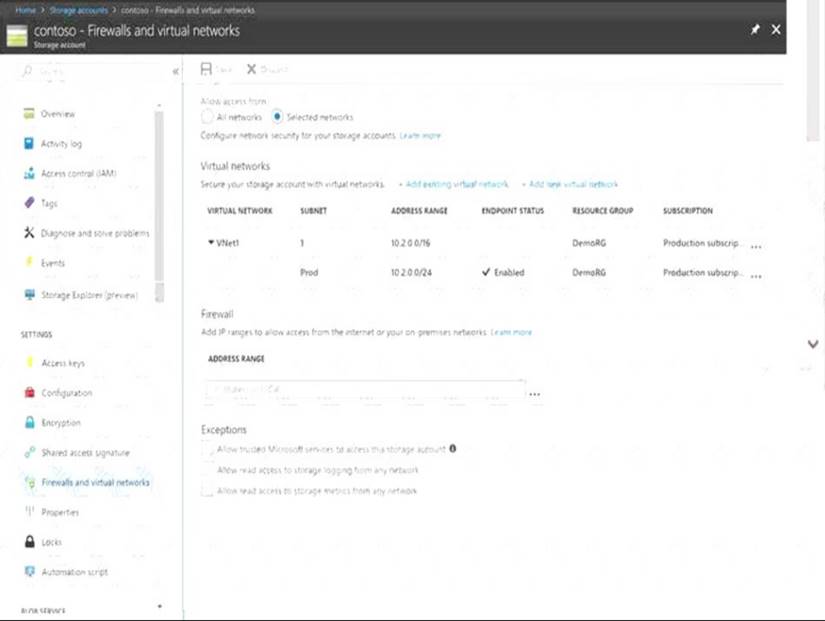
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Never
Box 2: Never
After you configure firewall and virtual network settings for your storage account, select Allow trusted Microsoft services to access this storage account as an exception to enable Azure Backup service to access the network restricted storage account.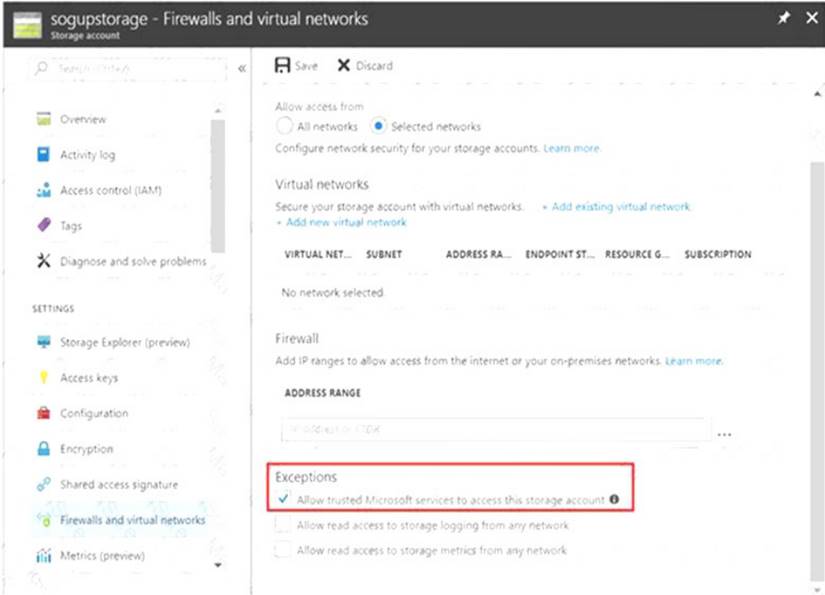
https://docs.microsoft.com/en-us/azure/storage/files/storage-how-to-use-files-windows https://azure.microsoft.com/en-us/blog/azure-backup-now-supports-storage-accounts-secured-with-azure-storage
NEW QUESTION 10
You play to deploy an Azure virtual machine named VM1 by using an Azure Resource Manager template. You need to complete the template.
What should you include in the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.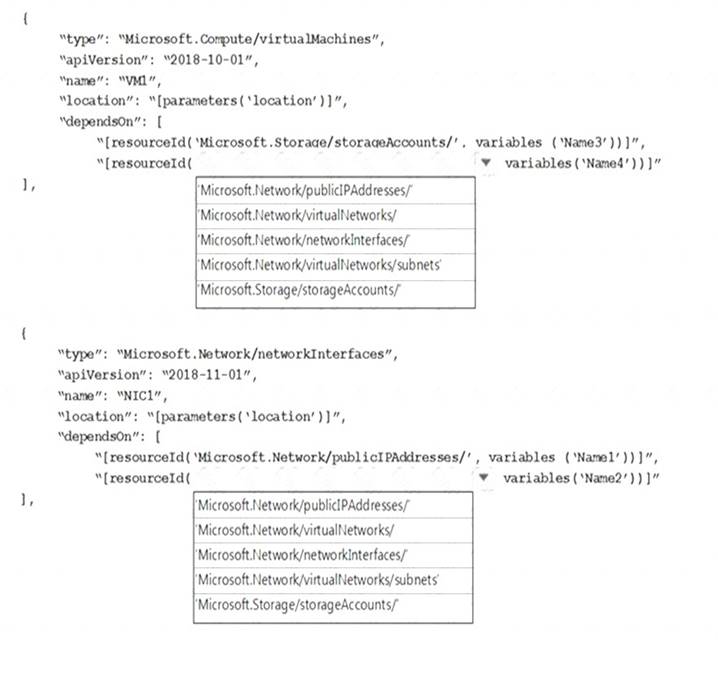
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Within your template, the dependsOn element enables you to define one resource as a dependent on one or more resources. Its value can be a comma-separated list of resource names.
Box 1: 'Microsoft.Network/networkInterfaces'
This resource is a virtual machine. It depends on two other resources: Microsoft.Storage/storageAccounts Microsoft.Network/networkInterfaces
Box 2: 'Microsoft.Network/virtualNetworks/'
The dependsOn element enables you to define one resource as a dependent on one or more resources. The resource depends on two other resources: Microsoft.Network/publicIPAddresses Microsoft.Network/virtualNetworks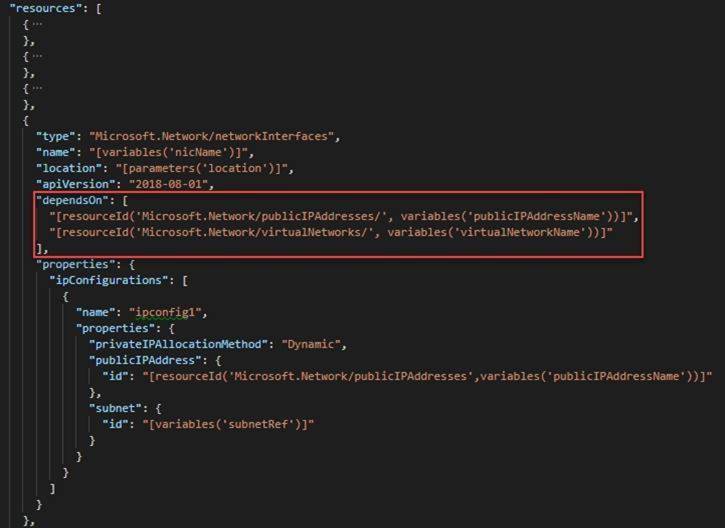
References:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-manager-tutorial-create-templates-with
NEW QUESTION 11
You have an Azure subscription that contains multiple resource groups. You create an availability set as shown in the following exhibit.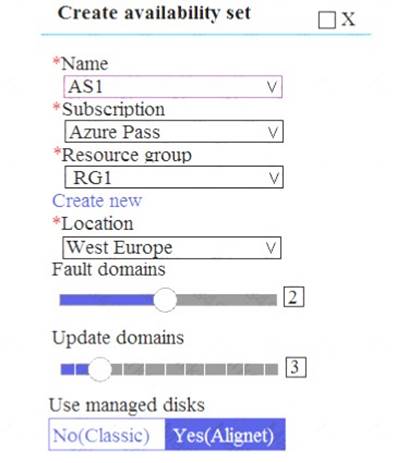
You deploy 10 virtual machines to AS1.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: 6
Two out of three update domains would be available, each with at least 3 VMs.
An update domain is a group of VMs and underlying physical hardware that can be rebooted at the same time. As you create VMs within an availability set, the Azure platform automatically distributes your VMs across these update domains. This approach ensures that at least one instance of your application always remains running as the Azure platform undergoes periodic maintenance.
Box 2: the West Europe region and the RG1 resource group References:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/regions-and-availability
NEW QUESTION 12
Your company plans to develop an application that will use a NoSQL database. The database will be used to store transactions and customer information by using JSON documents. Which two Azure Cosmos DB APIs can developers use for the application? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A. Cassandra
- B. Gremlin (graph)
- C. MongoDB
- D. Azure Table
- E. Core (SQL)
Answer: DE
NEW QUESTION 13
You are implementing authentication for applications in your company. You plan to implement self-service password reset (SSPR) and multifactor authentication (MFA) in Azure Active Directory (Azure AD).
You need to select authentication mechanisms that can be used for both MFA and SSPR.
Which two authentication methods should you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A. Short Message Service (SMS) messages
- B. Authentication app
- C. Email addresses
- D. Security questions
- E. App passwords
Answer: AB
Explanation:
References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
NEW QUESTION 14
You have an Azure subscription that contains the resource groups shown in the following table.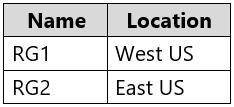
You create an Azure Resource Manager template named Template1 as shown in the following exhibit.
From the Azure portal, you deploy Template1 four times by using the settings shown in the following table.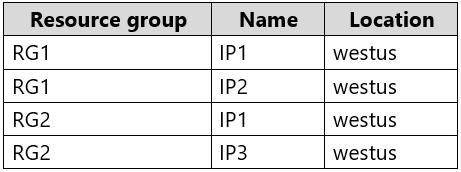
What is the result of the deployment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.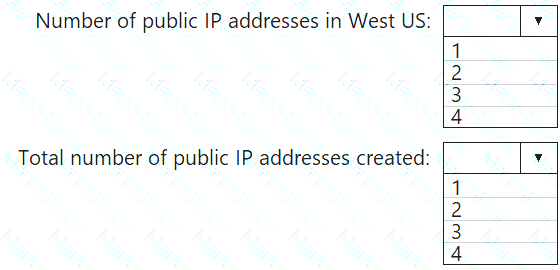
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 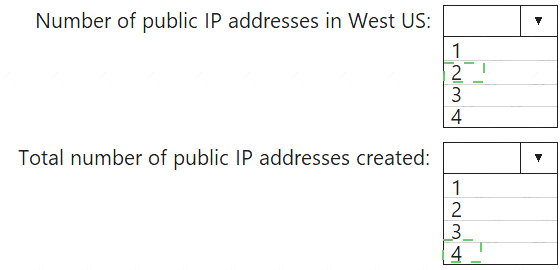
NEW QUESTION 15
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more
than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers that the Access reviews settings are unavailable. Admin1 discovers that all the other Identity Governance settings are available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles. You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You create an access package. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
You do not use access packages for Identity Governance. Instead use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key features of PIM include:
Conduct access reviews to ensure users still need roles References:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure https://docs.microsoft.com/en-us/azure/active-directory/governance/entitlement-management-overview
NEW QUESTION 16
You have an Azure subscription.
You create a custom role in Azure by using the following Azure Resource Manager template.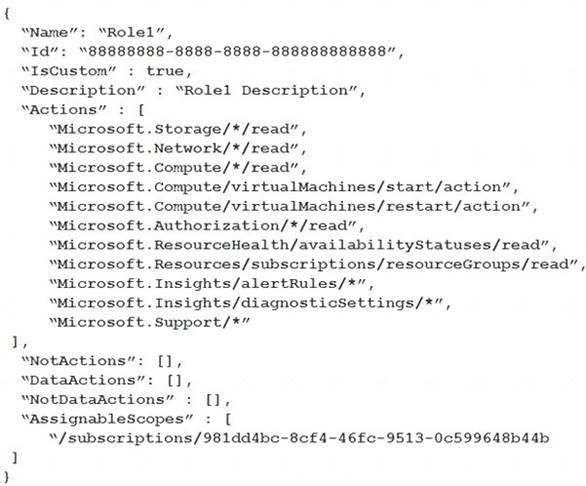
You assign the role to a user named User1. Which action can User1 perform?
- A. Delete virtual machines.
- B. Create resource groups.
- C. Create virtual machines.
- D. Create support requests
Answer: D
Explanation:
The "Microsoft.Support/*" operation will allow the user to create support tickets. References:
https://docs.microsoft.com/en-us/azure/role-based-access-control/tutorial-custom-role-powershell
NEW QUESTION 17
You have an Azure subscription that contains 100 virtual machines.
You have a set of Pester tests in PowerShell that validate the virtual machine environment.
You need to run the tests whenever there is an operating system update on the virtual machines. The solution must minimize implementation time and recurring costs.
D18912E1457D5D1DDCBD40AB3BF70D5D
Which three resources should you use to implement the tests? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Azure Automation runbook
- B. an alert rule
- C. an Azure Monitor query
- D. a virtual machine that has network access to the 100 virtual machines
- E. an alert action group
Answer: ABE
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/automation/automation-create-alert-triggered-runbook https://techsnips.io/snips/how-to-create-and-test-azure-monitor-alerts/?page=13
NEW QUESTION 18
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a group named Group1. You need to enable multi-factor authentication (MFA) for the users in Group1 only.
Solution: From Multi-Factor Authentication, you select Bulk update, and you provide a CSV file that contains the members of Group1.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
We should use a Conditional Access policy.
Note: There are two ways to secure user sign-in events by requiring multi-factor authentication in Azure AD. The first, and preferred, option is to set up a Conditional Access policy that requires multi-factor authentication under certain conditions. The second option is to enable each user for Azure Multi-Factor Authentication. When users are enabled individually, they perform multi-factor authentication each time they sign in (with some exceptions, such as when they sign in from trusted IP addresses or when the remembered devices feature is turned on).
Enabling Azure Multi-Factor Authentication using Conditional Access policies is the recommended approach. Changing user states is no longer recommended unless your licenses don't include Conditional Access as it requires users to perform MFA every time they sign in.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates
NEW QUESTION 19
You have an Azure Kubernetes Service (AKS) cluster named Clus1 in a resource group named RG1. An administrator plans to manage Clus1 from an Azure AD-joined device.
You need to ensure that the administrator can deploy the YAML application manifest file for a container application.
You install the Azure CLI on the device. Which command should you run next?
- A. kubectl get nodes
- B. az aks install-cli
- C. kubectl apply –f app1.yaml
- D. az aks get-credentials --resource-group RG1 --name Clus1
Answer: C
Explanation:
kubectl apply –f appl.yaml applies a configuration change to a resource from a file or stdin. References:
https://kubernetes.io/docs/reference/kubectl/overview/ https://docs.microsoft.com/en-us/cli/azure/aks
NEW QUESTION 20
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company is deploying an on-premises application named Appl. Users will access App1 by using a URL of https://app1.contoso.com. You register App1 in Azure Active Directory (Azure AD) and publish Appl by using the Azure AD Application Proxy. You need to ensure that Appl appears in the My Apps portal for all the users.
Solution: You create a conditional access policy for App1.
- A. Yes
- B. No
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full AZ-303 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/AZ-303-exam-dumps.html (New 0 Q&As Version)