Proper study guides for Renewal GAQM Certified Ethical Hacker (CEH) certified begins with GAQM CEH-001 preparation products which designed to deliver the Precise CEH-001 questions by making you pass the CEH-001 test at your first time. Try the free CEH-001 demo right now.
NEW QUESTION 1
Which of the following statements would NOT be a proper definition for a Trojan Horse?
- A. An authorized program that has been designed to capture keyboard keystroke while the user is unaware of such activity being performed
- B. An unauthorized program contained within a legitimate progra
- C. This unauthorized program performs functions unknown (and probably unwanted) by the user
- D. A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user
- E. Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user
Answer: A
NEW QUESTION 2
You perform the above traceroute and notice that hops 19 and 20 both show the same IP address.
This probably indicates what?
- A. A host based IDS
- B. A Honeypot
- C. A stateful inspection firewall
- D. An application proxying firewall
Answer: C
NEW QUESTION 3
What are the two basic types of attacks? (Choose two.
- A. DoS
- B. Passive
- C. Sniffing
- D. Active
- E. Cracking
Answer: BD
Explanation:
Passive and active attacks are the two basic types of attacks.
NEW QUESTION 4
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
- A. These ports are open because they do not illicit a response.
- B. He can tell that these ports are in stealth mode.
- C. If a port does not respond to an XMAS scan using NMAP, that port is closed.
- D. The scan was not performed correctly using NMAP since all ports, no matter what their state, will illicit some sort of response from an XMAS scan.
Answer: A
NEW QUESTION 5
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
- A. This command will provide you the entire list of hosts in the LAN
- B. This command will check if someone is poisoning you and will report its IP.
- C. This command will detach from console and log all the collected passwords from the network to a file.
- D. This command broadcasts ping to scan the LAN instead of ARP request of all the subnet IPs.
Answer: C
Explanation:
-N = NON interactive mode (without ncurses)
-C = collect all users and passwords
-L = if used with -C (collector) it creates a file with all the password sniffed in the session in the form "YYYYMMDD-collected-pass.log"
-z = start in silent mode (no arp storm on start up)
-s = IP BASED sniffing
--quiet = "demonize" ettercap. Useful if you want to log all data in background.
NEW QUESTION 6
You are attempting to map out the firewall policy for an organization. You discover your target system is one hop beyond the firewall. Using hping2, you send SYN packets with the exact TTL of the target system starting at port 1 and going up to port 1024. What is this process known as?
- A. Footprinting
- B. Firewalking
- C. Enumeration
- D. Idle scanning
Answer: B
Explanation:
Firewalking uses a traceroute-like IP packet analysis to determine whether or not a particular packet can pass from the attacker’s host to a destination host through a packet-filtering device. This technique can be used to map ‘open’ or ‘pass through’ ports on a gateway. More over, it can determine whether packets with various control information can pass through a given gateway.
NEW QUESTION 7
Where should a security tester be looking for information that could be used by an attacker against an organization? (Select all that apply)
- A. CHAT rooms
- B. WHOIS database
- C. News groups
- D. Web sites
- E. Search engines
- F. Organization’s own web site
Answer: ABCDEF
Explanation:
A Security tester should search for information everywhere that he/she can access. You never know where you find that small piece of information that could penetrate a strong defense.
NEW QUESTION 8
Which types of detection methods are employed by Network Intrusion Detection Systems (NIDS)? (Choose two.)
- A. Signature
- B. Anomaly
- C. Passive
- D. Reactive
Answer: AB
NEW QUESTION 9
How can telnet be used to fingerprint a web server?
- A. telnet webserverAddress 80 HEAD / HTTP/1.0
- B. telnet webserverAddress 80 PUT / HTTP/1.0
- C. telnet webserverAddress 80 HEAD / HTTP/2.0
- D. telnet webserverAddress 80 PUT / HTTP/2.0
Answer: A
NEW QUESTION 10
A security policy will be more accepted by employees if it is consistent and has the support of
- A. coworkers.
- B. executive management.
- C. the security officer.
- D. a supervisor.
Answer: B
NEW QUESTION 11
A covert channel is a channel that _____
- A. transfers information over, within a computer system, or network that is outside of the security policy.
- B. transfers information over, within a computer system, or network that is within the security policy.
- C. transfers information via a communication path within a computer system, or network for transfer of data.
- D. transfers information over, within a computer system, or network that is encrypted.
Answer: A
NEW QUESTION 12
Jackson discovers that the wireless AP transmits 128 bytes of plaintext, and the station responds by encrypting the plaintext. It then transmits the resulting ciphertext using the same key and cipher that are used by WEP to encrypt subsequent network traffic. What authentication mechanism is being followed here?
- A. no authentication
- B. single key authentication
- C. shared key authentication
- D. open system authentication
Answer: C
NEW QUESTION 13
An attacker finds a web page for a target organization that supplies contact information for the company. Using available details to make the message seem authentic, the attacker drafts e-mail to an employee on the contact page that appears to come from an individual who might reasonably request confidential information, such as a network administrator.
The email asks the employee to log into a bogus page that requests the employee's user name and password or click on a link that will download spyware or other malicious programming.
Google's Gmail was hacked using this technique and attackers stole source code and sensitive data from Google servers. This is highly sophisticated attack using zero-day exploit vectors, social engineering and malware websites that focused on targeted individuals working for the company.
What is this deadly attack called?
- A. Spear phishing attack
- B. Trojan server attack
- C. Javelin attack
- D. Social networking attack
Answer: A
NEW QUESTION 14
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
- A. Covert keylogger
- B. Stealth keylogger
- C. Software keylogger
- D. Hardware keylogger
Answer: D
Explanation:
As the hardware keylogger never interacts with the Operating System it is undetectable by anti-virus or anti-spyware products.
NEW QUESTION 15
What is one thing a tester can do to ensure that the software is trusted and is not changing
or tampering with critical data on the back end of a system it is loaded on?
- A. Proper testing
- B. Secure coding principles
- C. Systems security and architecture review
- D. Analysis of interrupts within the software
Answer: D
NEW QUESTION 16
Fake Anti-Virus, is one of the most frequently encountered and persistent threats on the web. This malware uses social engineering to lure users into infected websites with a technique called Search Engine Optimization.
Once the Fake AV is downloaded into the user's computer, the software will scare them into believing their system is infected with threats that do not really exist, and then push users to purchase services to clean up the non-existent threats.
The Fake AntiVirus will continue to send these annoying and intrusive alerts until a payment is made.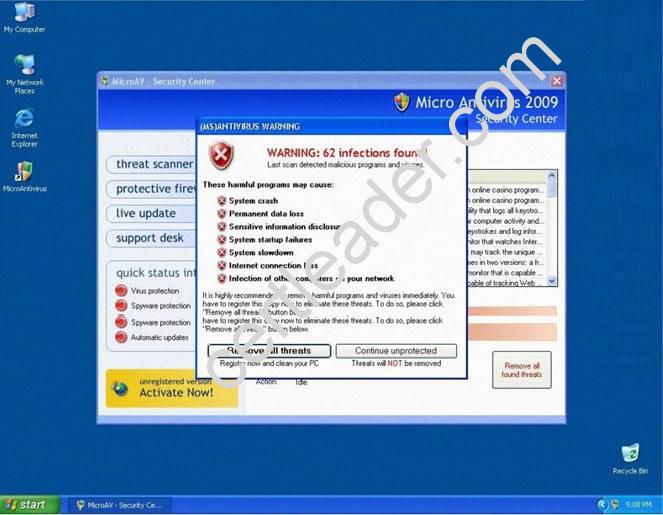
What is the risk of installing Fake AntiVirus?
- A. Victim's Operating System versions, services running and applications installed will be published on Blogs and Forums
- B. Victim's personally identifiable information such as billing address and credit card details, may be extracted and exploited by the attacker
- C. Once infected, the computer will be unable to boot and the Trojan will attempt to format the hard disk
- D. Denial of Service attack will be launched against the infected computer crashing other machines on the connected network
Answer: B
NEW QUESTION 17
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
- A. Man-in-the-middle attack
- B. Brute-force attack
- C. Dictionary attack
- D. Session hijacking
Answer: C
NEW QUESTION 18
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
- A. Hardware, Software, and Sniffing.
- B. Hardware and Software Keyloggers.
- C. Passwords are always best obtained using Hardware key loggers.
- D. Software only, they are the most effective.
Answer: A
Explanation:
Different types of keylogger planted into the environment would retrieve the passwords for Bob.
NEW QUESTION 19
From the two screenshots below, which of the following is occurring?
- A. 10.0.0.253 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
- B. 10.0.0.253 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
- C. 10.0.0.2 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
- D. 10.0.0.252 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
Answer: A
NEW QUESTION 20
What makes web application vulnerabilities so aggravating? (Choose two)
- A. They can be launched through an authorized port.
- B. A firewall will not stop them.
- C. They exist only on the Linux platform.
- D. They are detectable by most leading antivirus software.
Answer: AB
Explanation:
As the vulnerabilities exists on a web server, incoming traffic on port 80 will probably be allowed and no firewall rules will stop the attack.
NEW QUESTION 21
Jeremy is web security consultant for Information Securitas. Jeremy has just been hired to
perform contract work for a large state agency in Michigan. Jeremy's first task is to scan all the company's external websites. Jeremy comes upon a login page which appears to allow employees access to sensitive areas on the website. James types in the following statement in the username field:
SELECT * from Users where username='admin' ?AND password='' AND email like '%@testers.com%'
What will the SQL statement accomplish?
- A. If the page is susceptible to SQL injection, it will look in the Users table for usernames of admin
- B. This statement will look for users with the name of admin, blank passwords, and email addresses that end in @testers.com
- C. This Select SQL statement will log James in if there are any users with NULL passwords
- D. James will be able to see if there are any default user accounts in the SQL database
Answer: B
Explanation:
This query will search for admin user with blank password with mail address @testers.com
NEW QUESTION 22
What type of port scan is shown below?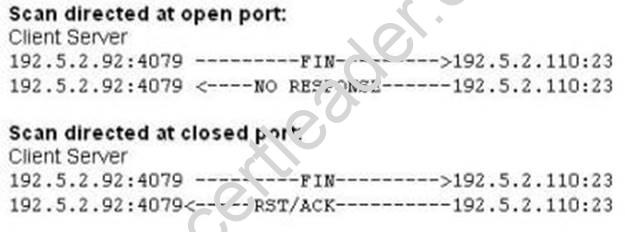
- A. Idle Scan
- B. FIN Scan
- C. XMAS Scan
- D. Windows Scan
Answer: B
NEW QUESTION 23
Which command line switch would be used in NMAP to perform operating system detection?
- A. -OS
- B. -sO
- C. -sP
- D. -O
Answer: D
NEW QUESTION 24
This kind of attack will let you assume a users identity at a dynamically generated web page or site:
- A. SQL Injection
- B. Cross Site Scripting
- C. Session Hijacking
- D. Zone Transfer
Answer: B
Explanation:
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by malicious web users into the web pages viewed by other users. Examples of such code include HTML code and client-side scripts. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy.
NEW QUESTION 25
A developer for a company is tasked with creating a program that will allow customers to update their billing and shipping information. The billing address field used is limited to 50 characters. What pseudo code would the developer use to avoid a buffer overflow attack on the billing address field?
- A. if (billingAddress = 50) {update field} else exit
- B. if (billingAddress != 50) {update field} else exit
- C. if (billingAddress >= 50) {update field} else exit
- D. if (billingAddress <= 50) {update field} else exit
Answer: D
NEW QUESTION 26
......
P.S. Certstest now are offering 100% pass ensure CEH-001 dumps! All CEH-001 exam questions have been updated with correct answers: https://www.certstest.com/dumps/CEH-001/ (878 New Questions)