we provide Realistic EC-Council ECSAv10 rapidshare which are the best for clearing ECSAv10 test, and to get certified by EC-Council EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing. The ECSAv10 Questions & Answers covers all the knowledge points of the real ECSAv10 exam. Crack your EC-Council ECSAv10 Exam with latest dumps, guaranteed!
EC-Council ECSAv10 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
- A. Visit Google’s search engine and view the cached copy
- B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
- C. Visit the company's partners’ and customers' website for this information
- D. Use Way Back Machine in Archive.org web site to retrieve the Internet archive
Answer: D
NEW QUESTION 2
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum.
Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.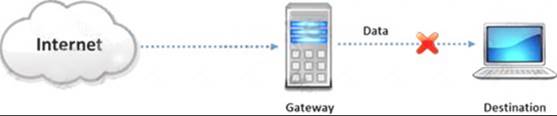
Which of the following ICMP messages will be generated if the destination port is not reachable?
- A. ICMP Type 11 code 1
- B. ICMP Type 5 code 3
- C. ICMP Type 3 code 2
- D. ICMP Type 3 code 3
Answer: D
NEW QUESTION 3
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories.
Identify the attacks that fall under Passive attacks category.
- A. Wardriving
- B. Spoofing
- C. Sniffing
- D. Network Hijacking
Answer: A
NEW QUESTION 4
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?
- A. Service-based Assessment Solutions
- B. Product-based Assessment Solutions
- C. Tree-based Assessment
- D. Inference-based Assessment
Answer: C
NEW QUESTION 5
What operating system would respond to the following command?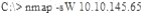
- A. Mac OS X
- B. Windows XP
- C. Windows 95
- D. FreeBSD
Answer: D
NEW QUESTION 6
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and G.
Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- A. 802.11b
- B. 802.11g
- C. 802.11-Legacy
- D. 802.11n
Answer: A
NEW QUESTION 7
The objective of social engineering pen testing is to test the strength of human factors in a security chain within the organization. It is often used to raise the level of security awareness among employees.
The tester should demonstrate extreme care and professionalism during a social engineering pen test as it might involve legal issues such as violation of privacy and may result in an embarrassing situation for the organization.
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts, and becoming involved in a personal relationship to befriend someone inside the company?
- A. Accomplice social engineering technique
- B. Identity theft
- C. Dumpster diving
- D. Phishing social engineering technique
Answer: A
NEW QUESTION 8
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
- A. Hash Key Length
- B. C/R Value Length
- C. C/R Key Length
- D. Hash Value Length
Answer: B
NEW QUESTION 9
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram.
Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a TYPE field.
If the destination is not reachable, which one of the following are generated?
- A. Type 8 ICMP codes
- B. Type 12 ICMP codes
- C. Type 3 ICMP codes
- D. Type 7 ICMP codes
Answer: C
NEW QUESTION 10
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.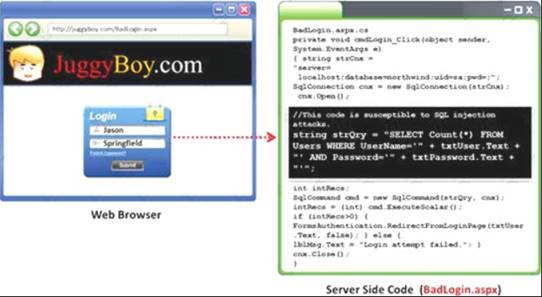
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes. Pen testers need to perform this testing during the development phase to find and fix the SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
- A. Send single quotes as the input data to catch instances where the user input is not sanitized
- B. Send double quotes as the input data to catch instances where the user input is not sanitized
- C. Send long strings of junk data, just as you would send strings to detect buffer overruns
- D. Use a right square bracket (the “]” character) as the input data to catch instances where the user input is used as part of a SQL identifier without any input sanitization
Answer: D
NEW QUESTION 11
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 12
When setting up a wireless network with multiple access points, why is it important to set each access point on a different channel?
- A. Avoid cross talk
- B. Avoid over-saturation of wireless signals
- C. So that the access points will work on different frequencies
- D. Multiple access points can be set up on the same channel without any issues
Answer: A
NEW QUESTION 13
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.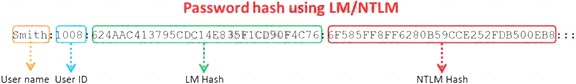
The SAM file in Windows Server 2008 is located in which of the following locations?
- A. c:windowssystem32configSAM
- B. c:windowssystem32driversSAM
- C. c:windowssystem32SetupSAM
- D. c:windowssystem32BootSAM
Answer: D
NEW QUESTION 14
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
- A. 802.11b
- B. 802.11a
- C. 802.11n
- D. 802.11-Legacy
Answer: D
NEW QUESTION 15
Which of the following statements is true about the LM hash?
- A. Disabled in Windows Vista and 7 OSs
- B. Separated into two 8-character strings
- C. Letters are converted to the lowercase
- D. Padded with NULL to 16 characters
Answer: A
NEW QUESTION 16
Which one of the following is a supporting tool for 802.11 (wireless) packet injections, it spoofs 802.11 packets to verify whether the access point is valid or not?
- A. Airsnort
- B. Aircrack
- C. Airpwn
- D. WEPCrack
Answer: C
NEW QUESTION 17
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 18
George is the network administrator of a large Internet company on the west coast. Per corporate policy, none of the employees in the company are allowed to use FTP or SFTP programs without obtaining approval from the IT department. Few managers are using SFTP program on their computers.
Before talking to his boss, George wants to have some proof of their activity. George wants to use Ethereal t monitor network traffic, but only SFTP traffic to and from his network. What filter should George use in Ethereal?
- A. net port 22
- B. udp port 22 and host 172.16.28.1/24
- C. src port 22 and dst port 22
- D. src port 23 and dst port 23
Answer: C
NEW QUESTION 19
Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
include <stdio.h>
#include <string.h>
int main(int argc, char *argv[])
{
char buffer[10]; if (argc < 2)
{
fprintf(stderr, "USAGE: %s stringn", argv[0]); return 1;
}
strcpy(buffer, argv[1]); return 0;
}
- A. Buffer overflow
- B. Format string bug
- C. Kernal injection
- D. SQL injection
Answer: A
NEW QUESTION 20
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
- A. SDW Encryption
- B. EFS Encryption
- C. DFS Encryption
- D. IPS Encryption
Answer: B
NEW QUESTION 21
Which of the following policy forbids everything with strict restrictions on all usage of the company systems and network?
- A. Information-Protection Po
- B. Paranoid Policy
- C. Promiscuous Policy
- D. Prudent Policy
Answer: B
NEW QUESTION 22
How many bits is Source Port Number in TCP Header packet?
- A. 48
- B. 32
- C. 64
- D. 16
Answer: D
NEW QUESTION 23
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 24
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
- A. ROCHESTON fileformat:+ppt
- B. ROCHESTON ppt:filestring
- C. ROCHESTON filetype:ppt
- D. ROCHESTON +ppt:filesearch
Answer: C
NEW QUESTION 25
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
- A. Connect Scanning Techniques
- B. SYN Scanning Techniques
- C. Stealth Scanning Techniques
- D. Port Scanning Techniques
Answer: C
NEW QUESTION 26
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, where 'xx' is the
- A. ASCII value of the character
- B. Binary value of the character
- C. Decimal value of the character
- D. Hex value of the character
Answer: D
NEW QUESTION 27
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
- A. XMAS Scan
- B. SYN scan
- C. FIN Scan
- D. NULL Scan
Answer: B
NEW QUESTION 28
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A. PortQry
- B. Netstat
- C. Telnet
- D. Tracert
Answer: A
NEW QUESTION 29
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
http://172.168.4.131/level/99/exec/show/config
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
- A. URL Obfuscation Arbitrary Administrative Access Vulnerability
- B. Cisco IOS Arbitrary Administrative Access Online Vulnerability
- C. HTTP Configuration Arbitrary Administrative Access Vulnerability
- D. HTML Configuration Arbitrary Administrative Access Vulnerability
Answer: C
NEW QUESTION 30
......
P.S. Easily pass ECSAv10 Exam with 201 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com ECSAv10 Dumps: https://www.dumps-files.com/files/ECSAv10/ (201 New Questions)