It is more faster and easier to pass the Salesforce Identity-and-Access-Management-Architect exam by using Accurate Salesforce Salesforce Certified Identity and Access Management Architect (SU23) questuins and answers. Immediate access to the Improved Identity-and-Access-Management-Architect Exam and find the same core area Identity-and-Access-Management-Architect questions with professionally verified answers, then PASS your exam with a high score now.
Check Identity-and-Access-Management-Architect free dumps before getting the full version:
NEW QUESTION 1
Universal Containers (UC) has an existing Salesforce org configured for SP-Initiated SAML SSO with their Idp. A second Salesforce org is being introduced into the environment and the IT team would like to ensure they can use the same Idp for new org. What action should the IT team take while implementing the second org?
- A. Use the same SAML Identity location as the first org.
- B. Use a different Entity ID than the first org.
- C. Use the same request bindings as the first org.
- D. Use the Salesforce Username as the SAML Identity Type.
Answer: B
Explanation:
The Entity ID is a unique identifier for a service provider or an identity provider in SAML SSO. It is used to differentiate between different service providers or identity providers that may share the same issuer or login URL. In Salesforce, the Entity ID is automatically generated based on the organization ID and can be viewed in the Single Sign-On Settings page1. If you have a custom domain set up, you can use https:// [customDomain].my.salesforce.com as the Entity ID2. If you want to use the same IdP for two Salesforce orgs, you need to use different Entity IDs for each org, otherwise the IdP will not be able to distinguish them
and may send incorrect assertions. You can also use different certificates, issuers, or login URLs for each org, but using different Entity IDs is the simplest and recommended way3.
NEW QUESTION 2
Universal Containers is considering using Delegated Authentication as the sole means of Authenticating of Salesforce users. A Salesforce Architect has been brought in to assist with the implementation. What two risks Should the Architect point out? Choose 2 answers
- A. Delegated Authentication is enabled or disabled for the entire Salesforce org.
- B. UC will be required to develop and support a custom SOAP web service.
- C. Salesforce users will be locked out of Salesforce if the web service goes down.
- D. The web service must reside on a public cloud service, such as Heroku.
Answer: BC
Explanation:
The two risks that the architect should point out for using delegated authentication as the sole means of authenticating Salesforce users are: UC will be required to develop and support a custom SOAP web service. Delegated authentication is a feature that allows Salesforce to delegate the authentication process to an external service by making a SOAP callout to a web service that verifies the user’s credentials. This feature requires UC to develop and support a custom SOAP web service that can accept and validate the user’s username and password, and return a boolean value to indicate whether the authentication is successful or not. This could increase complexity and cost for UC, as they need to write custom code and maintain the web service.
UC will be required to develop and support a custom SOAP web service. Delegated authentication is a feature that allows Salesforce to delegate the authentication process to an external service by making a SOAP callout to a web service that verifies the user’s credentials. This feature requires UC to develop and support a custom SOAP web service that can accept and validate the user’s username and password, and return a boolean value to indicate whether the authentication is successful or not. This could increase complexity and cost for UC, as they need to write custom code and maintain the web service. Salesforce users will be locked out of Salesforce if the web service goes down. Delegated authentication relies on the availability and performance of the external web service that handles the authentication requests from Salesforce. If the web service goes down or becomes slow, Salesforce users will not be able to log in or access Salesforce, as they will receive an error message or a timeout response. This could cause disruption and frustration for UC’s business operations and user satisfaction.
Salesforce users will be locked out of Salesforce if the web service goes down. Delegated authentication relies on the availability and performance of the external web service that handles the authentication requests from Salesforce. If the web service goes down or becomes slow, Salesforce users will not be able to log in or access Salesforce, as they will receive an error message or a timeout response. This could cause disruption and frustration for UC’s business operations and user satisfaction.
The other options are not valid risks for using delegated authentication. Delegated authentication can be enabled or disabled for individual users or groups of users by using permission sets or profiles, not for the entire Salesforce org. The web service does not need to reside on a public cloud service, such as Heroku, as it can be hosted on any platform that supports SOAP services and can communicate with Salesforce. References: [Delegated Authentication], [Enable ‘Delegated Authentication’], [Troubleshoot Delegated Authentication]
NEW QUESTION 3
Which three are capabilities of SAML-based Federated authentication? Choose 3 answers
- A. Trust relationships between Identity Provider and Service Provider are required.
- B. SAML tokens can be in XML or JSON format and can be used interchangeably.
- C. Web applications with no passwords are more secure and stronger against attacks.
- D. Access tokens are used to access resources on the server once the user is authenticated.
- E. Centralized federation provides single point of access, control and auditing.
Answer: ACE
Explanation:
A is correct because SAML-based Federated authentication requires trust relationships between the IdP and the SP. The IdP issues a SAML assertion that contains information about the user’s identity and attributes. The SP validates the assertion and grants access to the user.
C is correct because web applications that use SAML-based Federated authentication do not require passwords for users to log in. Instead, they rely on the IdP to authenticate the users and provide a secure token. This eliminates the risk of password breaches and phishing attacks.
E is correct because centralized federation provides a single point of access, control, and auditing for web applications that use SAML-based Federated authentication. Users can access multiple applications with one login, administrators can manage user access from one place, and auditors can monitor user activity across applications.
B is incorrect because SAML tokens are always in XML format. They cannot be used interchangeably with JSON tokens, which are used by OAuth or OpenID Connect protocols.
D is incorrect because access tokens are not used by SAML-based Federated authentication. Access tokens are used by OAuth or OpenID Connect protocols to access resources on the server once the user is authenticated.
References: : [Single Sign-On Implementation Guide Developer Documentation] : [Identity 101: Design Patterns for Access Management Salesforce Developers YouTube] : Certification - Identity and Access Management Architect - Trailhead : OAuth Authorization Flows Trailblazer Community Documentation : User Authentication Module - Trailhead
NEW QUESTION 4
Universal containers (UC) has implemented ansp-Initiated SAML flow between an external IDP and salesforce. A user at UC is attempting to login to salesforce1 for the first time and is being prompted for salesforce credentials instead of being shown the IDP login page. What is the likely cause of the issue?
- A. The "Redirect to Identity Provider" option has been selected in the my domain configuration.
- B. The user has not configured the salesforce1 mobile app to use my domain for login
- C. The "Redirect to identity provider" option has not been selected the SAML configuration.
- D. The user has not been granted the "Enable single Sign-on" permission
Answer: B
Explanation:
B is correct because the user has not configured the Salesforce1 mobile app to use My Domain for login, which is the likely cause of the issue. The My Domain URL is used to redirect the user to the identity provider’s login page and initiate the SP-Initiated SAML flow. If the user does not configure the Salesforce1 mobile app to use My Domain for login, they will be prompted for Salesforce credentials instead of being shown the IDP login page. A is incorrect because the “Redirect to Identity Provider” option has been selected in the My Domain configuration, which is not the cause of the issue. The “Redirect to Identity Provider” option determines whether users are redirected to the identity provider’s login page automatically or after clicking a button. C is incorrect because the “Redirect to Identity Provider” option has not been selected in the SAML configuration, which is not the cause of the issue. The “Redirect to Identity Provider” option determines whether users are redirected to the identity provider’s login page automatically or after clicking a button. D is incorrect because the user has been granted the “Enable Single Sign-On” permission, which is not the cause of the issue. The “Enable Single Sign-On” permission allows users to use SSO with connected apps or external systems. Verified References: [My Domain URL], [SP-Initiated SAML Flow], [Redirect to Identity Provider Option], [Enable Single Sign-On Permission]
NEW QUESTION 5
Containers (UC) has an existing Customer Community. UC wants to expand the self-registration capabilities such that customers receive a different community experience based on the data they provide during the registration process. What is the recommended approach an Architect Should recommend to UC?
- A. Create an After Insert Apex trigger on the user object to assign specific custom permissions.
- B. Create separate login flows corresponding to the different community user personas.
- C. Modify the Community pages to utilize specific fields on the User and Contact records.
- D. Modify the existing Communities registration controller to assign different profiles.
Answer: C
Explanation:
The recommended approach for UC to expand the self-registration capabilities such that customers receive a different community experience based on the data they provide during the registration process is to modify the community pages to utilize specific fields on the user and contact records. This approach allows UC to customize the community pages based on the user’s profile, preferences, interests, or other attributes that are stored in the user or contact fields. For example, UC can use conditional visibility rules or audience criteria to display different components or content based on the user’s field values. This approach does not require any code or complex configuration, and it provides a flexible and personalized community experience for different customer segments. The other options are not recommended for this scenario. Creating an after-insert Apex trigger on the user object to assign specific custom permissions would require UC to write code and manage custom permissions, which could increase maintenance and testing efforts. Creating separate login flows corresponding to the different community user personas would require UC to create multiple login pages and logic, which could increase complexity and confusion. Modifying the existing communities’ registration controller to assign different profiles would require UC to write code and manage multiple profiles, which could increase security and governance risks. References: [Customize Your Community Pages], [Set Component Visibility], [Create Custom Login Flows], [Customize Self-Registration]
NEW QUESTION 6
Universal Containers is budding a web application that will connect with the Salesforce API using JWT OAuth Flow.
Which two settings need to be configured in the connect app to support this requirement? Choose 2 answers
- A. The Use Digital Signature option in the connected app.
- B. The "web" OAuth scope in the connected app,
- C. The "api" OAuth scope in the connected app.
- D. The "edair_api" OAuth scope m the connected app.
Answer: AC
Explanation:
JWT OAuth Flow is a protocol that allows a client app to obtain an access token from Salesforce by using a JSON Web Token (JWT) instead of an authorization code. The JWT contains information about the client app and the user who wants to access Salesforce. To use this flow, the client app needs to have a connected app configured in Salesforce. The connected app is a framework that enables an external application to integrate with Salesforce using APIs and standard protocols. To support JWT OAuth Flow, two settings need to be configured in the connected app: The Use Digital Signature option, which enables the connected app to verify the signature of the JWT using a certificate.
The Use Digital Signature option, which enables the connected app to verify the signature of the JWT using a certificate. The “api” OAuth scope, which allows the connected app to access Salesforce APIs on behalf of the user.
The “api” OAuth scope, which allows the connected app to access Salesforce APIs on behalf of the user.
References: JWT OAuth Flow, Connected Apps, OAuth Scopes
NEW QUESTION 7
Universal Containers (UC) operates in Asia, Europe and North America regions. There is one Salesforce org for each region. UC is implementing Customer 360 in Salesforce and has procured External Identity and Customer Community licenses in all orgs.
Customers of UC use Community to track orders and create inquiries. Customers also tend to move across regions frequently.
What should an identity architect recommend to optimize license usage and reduce maintenance overhead?
- A. Merge three orgs into one instance of Salesforc
- B. This will no longer require maintaining three separate copies of the same customer.
- C. Delete contact/ account records and deactivate user if user moves from a specific region; Sync will no longer be required.
- D. Contacts are required since Community access needs to be enable
- E. Maintenance is a necessary overhead that must be handled via data integration.
- F. Enable Contactless User in all orgs and downgrade users from Experience Cloud license to External Identity license once users have moved out of that region.
Answer: D
Explanation:
To optimize license usage and reduce maintenance overhead for customers who use Community to track orders and create inquiries and tend to move across regions frequently, the identity architect should recommend enabling Contactless User in all orgs and downgrade users from Experience Cloud license to External Identity license once users have moved out of that region. Contactless User is a feature that allows users to access Experience Cloud sites without having a contact record associated with them. External Identity is a license type that enables users to access Experience Cloud sites using social sign-on or single sign-on, but not access Salesforce objects or data. By enabling Contactless User and downgrading users from Experience Cloud license to External Identity license, the identity architect can reduce the number of contacts and licenses needed for each region and avoid data duplication and synchronization issues. References: Contactless User, External Identity License, User Licenses
NEW QUESTION 8
Universal containers (UC) wants to implement a partner community. As part of their implementation, UC would like to modify both the Forgot password and change password experience with custom branding for their partner community users. Which 2 actions should an architect recommend to UC? Choose 2 answers
- A. Build a community builder page for the change password experience and Custom Visualforce page for the Forgot password experience.
- B. Build a custom visualforce page for both the change password and Forgot password experiences.
- C. Build a custom visualforce page for the change password experience and a community builder page for the Forgot password experience.
- D. Build a community builder page for both the change password and Forgot password experiences.
Answer: BC
Explanation:
The two actions that an architect should recommend to UC are to build a custom Visualforce page for both the change password and forgot password experiences and to build a custom Visualforce page for the change password experience and a community builder page for the forgot password experience. A custom Visualforce page is a page that uses Visualforce markup and Apex code to create a custom user interface. A community builder page is a page that uses the Community Builder tool to create a custom user interface with drag-and-drop components. Both types of pages can be used to modify the look and feel of the password management features for partner community users. However, using a custom Visualforce page for both features requires more coding and customization, while using a community builder page for the forgot password feature allows more flexibility and configuration options.
References: [Visualforce Pages], [Community Builder Pages], [Customize Password Management Features]
NEW QUESTION 9
Universal containers (UC) would like to enable self - registration for their salesforce partner community users. UC wants to capture some custom data elements from the partner user, and based on these data elements, wants to assign the appropriate profile and account values. Which two actions should the architect recommend to UC? Choose 2 answers
- A. Modify the communitiesselfregcontroller to assign the profile and account.
- B. Modify the selfregistration trigger to assign profile and account.
- C. Configure registration for communities to use a custom visualforce page.
- D. Configure registration for communities to use a custom apex controller.
Answer: AC
Explanation:
To enable self-registration for their Salesforce partner community users, UC should modify the communities’ self-registration controller to assign the profile and account based on the custom data elements from the partner user1. UC should also configure registration for communities to use a custom Visualforce page to capture the custom data elements from the partner user2. Therefore, option A and C are the correct answers.
References: Salesforce Partner Community, Partner Community Registration Guide
NEW QUESTION 10
Universal containers(UC) has implemented SAML-BASED single Sign-on for their salesforce application and is planning to provide access to salesforce on mobile devices using the salesforce1 mobile app. UC wants to ensure that single Sign-on is used for accessing the salesforce1 mobile app. Which two recommendations should the architect make? Choose 2 answers
- A. Use the existing SAML SSO flow along with user agent flow.
- B. Configure the embedded Web browser to use my domain URL.
- C. Use the existing SAML SSO flow along with Web server flow
- D. Configure the salesforce1 app to use the my domain URL
Answer: BD
Explanation:
To use SAML SSO for accessing the Salesforce1 mobile app, the architect should recommend configuring the embedded web browser to use the My Domain URL and configuring the Salesforce1 app to use the My Domain URL4. Using the My Domain URL allows Salesforce to identify the identity provider and initiate the SSO process5. Using the existing SAML SSO flow along with user agent flow or web server flow is not necessary because Salesforce Mobile Applications only work with service provider initiated setups46. Therefore, option B and D are the correct answers.
References: Salesforce Mobile Application Single Sign-On overview, SAML SSO with Salesforce as the Service Provider, Single Sign-On
NEW QUESTION 11
A division of a Northern Trail Outfitters (NTO) purchased Salesforce. NTO uses a third party identity provider (IdP) to validate user credentials against Its corporate Lightweight Directory Access Protocol (LDAP) directory. NTO wants to help employees remember as passwords as possible.
What should an identity architect recommend?
- A. Setup Salesforce as a Service Provider to the existing IdP.
- B. Setup Salesforce as an IdP to authenticate against the LDAP directory.
- C. Use Salesforce connect to synchronize LDAP passwords to Salesforce.
- D. Setup Salesforce as an Authentication Provider to the existing IdP.
Answer: A
Explanation:
To help employees remember fewer passwords, an identity architect should recommend setting up Salesforce as a service provider (SP) to the existing IdP. A SP is the system that relies on the IdP for authentication and provides access to its services based on the SAML assertions from the IdP. To set up Salesforce as a SP, you need to create a connected app for Salesforce in the IdP, enable SAML and configure the SAML settings, such as the entity ID, ACS URL, and subject type. You also need to enable SSO for your Salesforce org, upload the IdP certificate, and configure the SSO settings, such as the issuer, identity type, and service provider initiated request binding.
References: [SAML Single Sign-On]
[SAML Single Sign-On] [Set Up Salesforce as a Service Provider]
[Set Up Salesforce as a Service Provider]  [Enable Single Sign-On for Your Org]
[Enable Single Sign-On for Your Org]
NEW QUESTION 12
When designing a multi-branded Customer Identity and Access Management solution on the Salesforce Platform, how should an identity architect ensure a specific brand experience in Salesforce is presented?
- A. The Experience ID, which can be included in OAuth/Open ID flows and Security Assertion Markup Language (SAML) flows as a URL parameter.
- B. Provide a brand picker that the end user can use to select its sub-brand when they arrive on salesforce.
- C. Add a custom parameter to the service provider's OAuth/SAML call and implement logic on its login page to apply branding based on the parameters value.
- D. The Audience ID, which can be set in a shared cookie.
Answer: A
Explanation:
Configuring an authentication provider to delegate authentication to the LDAP directory ensures that users can only log in to Salesforce if they are active in the LDAP directory. This prevents terminated employees from accessing Salesforce with their old credentials. References: Authentication Providers, Delegated Authentication Single Sign-On
NEW QUESTION 13
Universal Containers (UC) wants its users to access Salesforce and other SSO-enabled applications from a custom web page that UC magnets. UC wants its users to use the same set of credentials to access each of the applications. what SAML SSO flow should an Architect recommend for UC?
- A. SP-Initiated with Deep Linking
- B. SP-Initiated
- C. IdP-Initiated
- D. User-Agent
Answer: C
Explanation:
The SAML SSO flow that an architect should recommend for UC is IdP-initiated. IdP-initiated SSO is a process that allows users to start at the IdP site, such as UC’s custom web page, and then be redirected to Salesforce or other SPs with a SAML assertion that contains information about the user’s identity and attributes. This flow enables UC to provide a single point of entry for its users to access multiple applications with the same credentials, as they do not need to enter their username and password again for each application. This flow also simplifies the configuration and maintenance of SSO, as UC does not need to create or manage deep links or URLs for each application.
The other options are not valid SAML SSO flows for this scenario. SP-initiated with deep linking is a process that allows users to start at a specific resource on the SP site, such as a report or dashboard, and then be redirected to the IdP for authentication and back to the resource with a SAML assertion. This flow is not suitable for UC’s scenario, as they want their users to start at their custom web page, not at a specific resource on Salesforce or other SPs. SP-initiated is a process that allows users to start at the SP site, such as Salesforce or other applications, and then be redirected to the IdP for authentication and back to the SP site with a SAML assertion. This flow is not suitable for UC’s scenario, as they want their users to start at their custom web page, not at each application separately. User-agent is not a standard term for SAML SSO, but it could refer to user-agent flow, which is an OAuth authorization flow that allows users to obtain an access token from Salesforce by using a browser or web-view. This flow is not suitable for UC’s scenario, as it does not use SAML or IdP for authentication. References: [SAML Single Sign-On], [IdP-Initiated Login], [SP-Initiated Login], [Deep Linking], [OAuth User-Agent Flow]
NEW QUESTION 14
Universal Containers is using OpenID Connect to enable a connection from their new mobile app to its production Salesforce org.
What should be done to enable the retrieval of the access token status for the OpenID Connect connection?
- A. Query using OpenID Connect discovery endpoint.
- B. A Leverage OpenID Connect Token Introspection.
- C. Create a custom OAuth scope.
- D. Enable cross-origin resource sharing (CORS) for the /services/oauth2/token endpoint.
Answer: B
Explanation:
According to the Salesforce documentation1, OpenID Connect Token Introspection allows all OAuth connected apps to check the current state of an OAuth 2.0 access or refresh token. The resource server or connected apps send the client app’s client ID and secret to the authorization server, initiating an OAuth authorization flow. As part of this flow, the authorization server validates, or introspects, the client app’s access token. If the access token is current and valid, the client app is granted access.
NEW QUESTION 15
Northern Trail Outfitters (NTO) wants its customers to use phone numbers to log in to their new digital portal, which was designed and built using Salesforce Experience Cloud. In order to access the portal, the user will need to do the following:
* 1. Enter a phone number and/or email address
* 2. Enter a verification code that is to be sent via email or text.
What is the recommended approach to fulfill this requirement?
- A. Create a Login Discovery page and provide a Login Discovery Handler Apex class.
- B. Create a custom login page with an Apex controlle
- C. The controller has logic to send and verify the identity.
- D. Create an authentication provider and implement a self-registration handler class.
- E. Create a custom login flow that uses an Apex controller to verify the phone numbers with the company's verification service.
Answer: A
Explanation:
To allow customers to use phone numbers to log in to their new digital portal, the identity architect should create a Login Discovery page and provide a Login Discovery Handler Apex class. A Login Discovery page is a custom page that allows users to enter their phone number or email address and receive a verification code via email or text. A Login Discovery Handler is a class that implements the Auth.LoginDiscoveryHandler interface and defines how to handle the user input and verification code. This approach can provide a passwordless login experience for the customers. References: Login Discovery, Create a Login Discovery Page
NEW QUESTION 16
An identity architect's client has a homegrown identity provider (IdP). Salesforce is used as the service provider (SP). The head of IT is worried that during a SP initiated single sign-on (SSO), the Security Assertion Markup Language (SAML) request content will be altered.
What should the identity architect recommend to make sure that there is additional trust between the SP and the IdP?
- A. Ensure that there is an HTTPS connection between IDP and SP.
- B. Ensure that on the SSO settings page, the "Request Signing Certificate" field has a self-signed certificate.
- C. Ensure that the Issuer and Assertion Consumer service (ACS) URL is property configured between SP and IDP.
- D. Encrypt the SAML Request using certification authority (CA) signed certificate and decrypt on IdP.
Answer: D
Explanation:
Encrypting the SAML Request using a CA signed certificate and decrypting it on the IdP ensures that the request content is not altered or tampered with during transit. This also adds an extra layer of security and trust between the SP and the IdP. References: SAML Single Sign-On Overview, SAML Assertion Encryption
NEW QUESTION 17
Containers (UC) has decided to implement a federated single Sign-on solution using a third-party Idp. In reviewing the third-party products, they would like to ensure the product supports the automated provisioning and deprovisioning of users. What are the underlining mechanisms that the UC Architect must ensure are part of the product?
- A. SOAP API for provisioning; Just-in-Time (JIT) for Deprovisioning.
- B. Just-In-time (JIT) for Provisioning; SOAP API for Deprovisioning.
- C. Provisioning API for both Provisioning and Deprovisioning.
- D. Just-in-Time (JIT) for both Provisioning and Deprovisionin
Answer: D
Explanation:
Just-in-Time (JIT) provisioning and deprovisioning can be used to create, update, or deactivate users in Salesforce based on the information in the SAML assertion sent by the IdP. This way, the user lifecycle can be managed automatically without the need for a separate provisioning API. Reference: [Salesforce Help:
Just-in-Time Provisioning for SAML]
NEW QUESTION 18
Universal Containers (UC) has implemented SAML-based Single Sign-On to provide seamless access to its Salesforce Orgs, financial system, and CPQ system. Below is the SSO implementation landscape.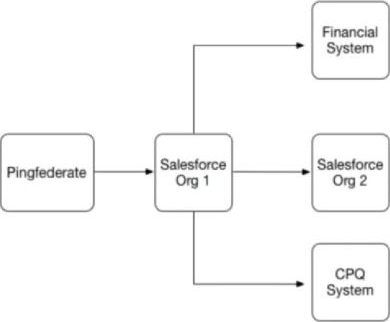
What role combination is represented by the systems in this scenario''
- A. Financial System and CPQ System are the only Service Providers.
- B. Salesforce Org1 and Salesforce Org2 are the only Service Providers.
- C. Salesforce Org1 and Salesforce Org2 are acting as Identity Providers.
- D. Salesforce Org1 and PingFederate are acting as Identity Providers.
Answer: B
Explanation:
In a SAML-based SSO scenario, the identity provider (IdP) is the system that performs authentication and passes the user’s identity and authorization level to the service provider (SP), which trusts the IdP and authorizes the user to access the requested resource1. In this case, PingFederate is the IdP that authenticates users for UC and sends SAML assertions to the SPs. The SPs are the systems that rely on PingFederate for authentication and provide access to their services based on the SAML assertions. The SPs in this scenario are Salesforce Org1, Salesforce Org2, Financial System, and CPQ System2. Therefore, the correct answer is B.
References: SAML web-based authentication guide
SAML web-based authentication guide SAML-based single sign-on: Configuration and Limitations
SAML-based single sign-on: Configuration and Limitations
NEW QUESTION 19
Universal containers (UC) wants to implement Delegated Authentication for a certain subset of Salesforce users. Which three items should UC take into consideration while building the Web service to handle the Delegated Authentication request? Choose 3 answers
- A. The web service needs to include Source IP as a method parameter.
- B. UC should whitelist all salesforce ip ranges on their corporate firewall.
- C. The web service can be written using either the soap or rest protocol.
- D. Delegated Authentication is enabled for the system administrator profile.
- E. The return type of the Web service method should be a Boolean value
Answer: ABE
Explanation:
Delegated authentication is a feature that allows Salesforce to delegate the authentication process to an external web service. The web service needs to include the source IP address of the user as a method parameter, so that Salesforce can pass it along with the username and password. UC should whitelist all Salesforce IP ranges on their corporate firewall, so that the web service can accept requests from Salesforce. The return type of the web service method should be a Boolean value, indicating whether the authentication was successful or not. The web service can be written using either SOAP or REST protocol, but this is not a consideration for UC while building the web service. Delegated authentication is not enabled for the system administrator profile, but it can be enabled for other profiles or permission sets. References: Certification - Identity and Access Management Architect - Trailhead, [Delegated Authentication Single Sign-On], [Implementing Single Sign-On Across Multiple Organizations]
NEW QUESTION 20
......
P.S. Easily pass Identity-and-Access-Management-Architect Exam with 246 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com Identity-and-Access-Management-Architect Dumps: https://www.dumpscollection.net/dumps/Identity-and-Access-Management-Architect/ (246 New Questions)