It is impossible to pass Juniper JN0-230 exam without any help in the short term. Come to Ucertify soon and find the most advanced, correct and guaranteed Juniper JN0-230 practice questions. You will get a surprising result by our Refresh Security - Associate (JNCIA-SEC) practice guides.
Online JN0-230 free questions and answers of New Version:
NEW QUESTION 1
Which two feature on the SRX Series device are common across all Junos devices? (Choose two.)
- A. Stateless firewall filters
- B. UTM services
- C. The separation of control and forwarding planes
- D. screens
Answer: AC
NEW QUESTION 2
Exhibit.
Which two statements are true? (Choose two.)
- A. Logs for this security policy are generated.
- B. Logs for this security policy are not generated.
- C. Traffic static for this security policy are not generated.
- D. Traffic statistics for this security policy are generated.
Answer: AD
NEW QUESTION 3
Which statement about IPsec is correct?
- A. IPsec can be used to transport native Layer 2 packets.
- B. IPsec can provide encapsulation but not encryption
- C. IPsec is a standards-based protocol.
- D. IPsec is used to provide data replication
Answer: C
NEW QUESTION 4
What should you configure if you want to translate private source IP address to a single public IP address?
- A. Source NAT
- B. Destination NAT
- C. Content filtering
- D. Security Director
Answer: A
NEW QUESTION 5
Which actions would be applied for the pre-ID default policy unified policies?
- A. Redirect the session
- B. Reject the session
- C. Log the session
- D. Silently drop the session
Answer: C
NEW QUESTION 6
The Sky ATP premium or basic-Threat Feed license is needed fort which two features? (Choose two.)
- A. Outbound protection
- B. C&C feeds
- C. Executable inspection
- D. Custom feeds
Answer: BD
NEW QUESTION 7
You have configured a Web filtering UTM policy?
Which action must be performed before the Web filtering UTM policy takes effect?
- A. The UTM policy must be linked to an egress interface
- B. The UTM policy be configured as a routing next hop.
- C. The UTM policy must be linked to an ingress interface.
- D. The UTM policy must be linked to a security policy
Answer: D
NEW QUESTION 8
Which statement about IPsec is correct?
- A. IPsec can provide encryption but not data integrity.
- B. IPsec support packet fragmentation by intermediary devices.
- C. IPsec support both tunnel and transport modes.
- D. IPsec must use certificates to provide data encryption
Answer: C
NEW QUESTION 9
Users should not have access to Facebook, however, a recent examination of the logs security show that users are accessing Facebook.
Referring to the exhibit,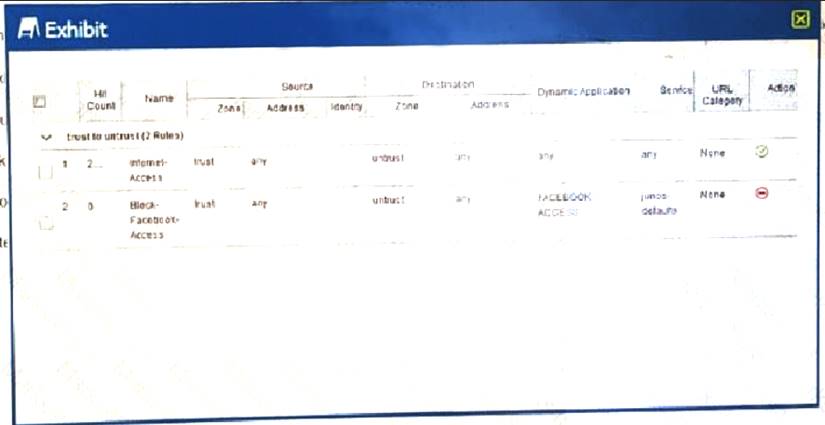
what should you do to solve this problem?
- A. Change the source address for the Block-Facebook-Access rule to the prefix of the users
- B. Move the Block-Facebook-Access rule before the Internet-Access rule
- C. Move the Block-Facebook-Access rule from a zone policy to a global policy
- D. Change the Internet-Access rule from a zone policy to a global policy
Answer: B
NEW QUESTION 10
Users on the network are restricted from accessing Facebook, however, a recent examination of the logs show that users are accessing Facebook.
Referring to the exhibit,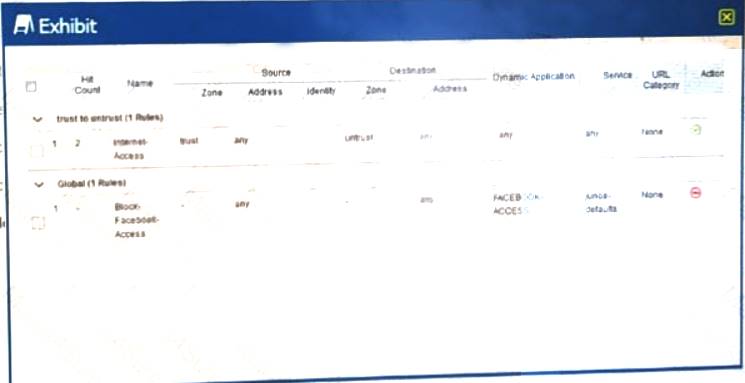
Why is this problem happening?
- A. Global rules are honored before zone-based rules.
- B. The internet-Access rule has a higher precedence value
- C. The internet-Access rule is listed first
- D. Zone-based rules are honored before global rules
Answer: D
NEW QUESTION 11
Firewall filters define which type of security?
- A. Stateful
- B. Stateless
- C. NGFW
- D. Dynamic enforcement
Answer: B
NEW QUESTION 12
Which statements is correct about SKY ATP?
- A. Sky ATP is an open-source security solution.
- B. Sky ATP is used to automatically push out changes to the AppSecure suite.
- C. Sky ATP only support sending threat feeds to vSRX Series devices
- D. Sky ATP is a cloud-based security threat analyzer that performs multiple tasks
Answer: D
NEW QUESTION 13
You verify that the SSH service is configured correctly on your SRX Series device, yet administrators attempting to connect through a revenue port are not able to connect.
In this scenario, what must be configured to solve this problem?
- A. A security policy allowing SSH traffic.
- B. A host-inbound-traffic setting on the incoming zone
- C. An MTU value target than the default value
- D. A screen on the internal interface
Answer: B
NEW QUESTION 14
You have created a zones-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so.
What are two reasons for this access failure? (Choose two.)
- A. You failed to change the source zone to include any source zone.
- B. You failed to position the policy after the policy that denies access to the webserver.
- C. You failed to commit the policy change.
- D. You failed to position the policy before the policy that denies access the webserver
Answer: CD
NEW QUESTION 15
Which two statements are true about security policy actions? (Choose two.)
- A. The reject action drops the traffic and sends a message to the source device.
- B. The deny action silently drop the traffic.
- C. The deny action drops the traffic and sends a message to the source device.
- D. The reject action silently drops the traffic.
Answer: AB
NEW QUESTION 16
Which security feature is applied to traffic on an SRX Series device when the device is running n packet mode?
- A. Sky ATP
- B. ALGs
- C. Firewall filters
- D. Unified policies
Answer: C
NEW QUESTION 17
Your company has been assigned one public IP address. You want to enable internet traffic to reach multiple servers in your DMZ that are configured with private address.
In this scenario, which type of NAT would be used to accomplish this tasks?
- A. Static NAT
- B. Destination NAT
- C. Source NAT
- D. NAT without PAT
Answer: B
NEW QUESTION 18
Which flow module components handles processing for UTM?
- A. Policy
- B. Zones
- C. Services
- D. Screen options
Answer: C
NEW QUESTION 19
BY default, revenue interface are placed into which system-defined security zone on an SRX series device?
- A. Trust
- B. Null
- C. Junos-trust
- D. untrust
Answer: D
NEW QUESTION 20
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office-using a dynamic IP address?
- A. Configure the IPsec policy to use MDS authentication.
- B. Configure the IKE policy to use aggressive mode.
- C. Configure the IPsec policy to use aggressive mode.
- D. Configure the IKE policy to use a static IP address
Answer: B
NEW QUESTION 21
......
100% Valid and Newest Version JN0-230 Questions & Answers shared by Simply pass, Get Full Dumps HERE: https://www.simply-pass.com/Juniper-exam/JN0-230-dumps.html (New 65 Q&As)