We provide real PCCET exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Paloalto-Networks PCCET Exam quickly & easily. The PCCET PDF type is available for reading and printing. You can print more and practice many times. With the help of our Paloalto-Networks PCCET dumps pdf and vce product and material, you can easily pass the PCCET exam.
Free demo questions for Paloalto-Networks PCCET Exam Dumps Below:
NEW QUESTION 1
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Dynamic
- B. Pre-exploit protection
- C. Bare-metal
- D. Static
Answer: A
NEW QUESTION 2
Which characteristic of serverless computing enables developers to quickly deploy application code?
- A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
- B. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
- C. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
- D. Using Container as a Service (CaaS) to deploy application containers to run their code.
Answer: A
NEW QUESTION 3
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
- A. Expedition
- B. AutoFocus
- C. MineMeld
- D. Cortex XDR
Answer: D
NEW QUESTION 4
Which option is a Prisma Access security service?
- A. Compute Security
- B. Firewall as a Service (FWaaS)
- C. Virtual Private Networks (VPNs)
- D. Software-defined wide-area networks (SD-WANs)
Answer: B
NEW QUESTION 5
The customer is responsible only for which type of security when using a SaaS application?
- A. physical
- B. platform
- C. data
- D. infrastructure
Answer: C
NEW QUESTION 6
Which option is an example of a North-South traffic flow?
- A. Lateral movement within a cloud or data center
- B. An internal three-tier application
- C. Client-server interactions that cross the edge perimeter
- D. Traffic between an internal server and internal user
Answer: C
NEW QUESTION 7
Which activities do local organization security policies cover for a SaaS application?
- A. how the data is backed up in one or more locations
- B. how the application can be used
- C. how the application processes the data
- D. how the application can transit the Internet
Answer: B
NEW QUESTION 8
On an endpoint, which method should you use to secure applications against exploits?
- A. endpoint-based firewall
- B. strong user passwords
- C. full-disk encryption
- D. software patches
Answer: A
NEW QUESTION 9
Which aspect of a SaaS application requires compliance with local organizational security policies?
- A. Types of physical storage media used
- B. Data-at-rest encryption standards
- C. Acceptable use of the SaaS application
- D. Vulnerability scanning and management
Answer: C
NEW QUESTION 10
Which network analysis tool can be used to record packet captures?
- A. Smart IP Scanner
- B. Wireshark
- C. Angry IP Scanner
- D. Netman
Answer: B
NEW QUESTION 11
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
- A. Computer
- B. Switch
- C. Infrastructure
- D. Cloud
Answer: C
NEW QUESTION 12
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
- A. Benign
- B. Tolerated
- C. Sanctioned
- D. Secure
Answer: C
NEW QUESTION 13
DRAG DROP
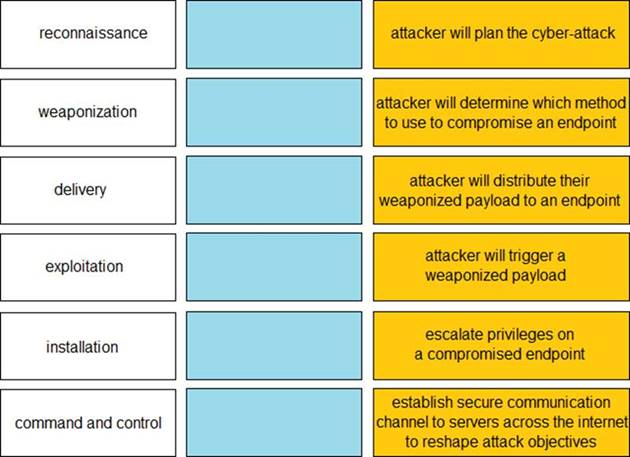
Given the graphic, match each stage of the cyber-attack lifecycle to its description.:
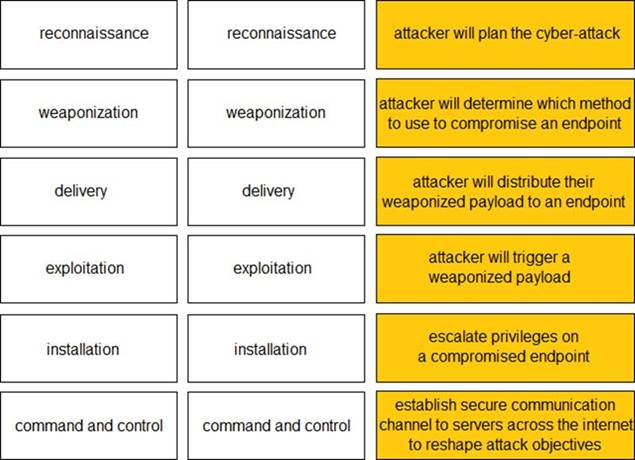
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
- A. Cortex XDR
- B. AutoFocus
- C. MineMild
- D. Cortex XSOAR
Answer: A
NEW QUESTION 15
What does SIEM stand for?
- A. Security Infosec and Event Management
- B. Security Information and Event Management
- C. Standard Installation and Event Media
- D. Secure Infrastructure and Event Monitoring
Answer: B
NEW QUESTION 16
Which endpoint product from Palo Alto Networks can help with SOC visibility?
- A. STIX
- B. Cortex XDR
- C. WildFire
- D. AutoFocus
Answer: B
NEW QUESTION 17
Which IoT connectivity technology is provided by satellites?
- A. 4G/LTE
- B. VLF
- C. L-band
- D. 2G/2.5G
Answer: C
NEW QUESTION 18
Which two network resources does a directory service database contain? (Choose two.)
- A. Services
- B. /etc/shadow files
- C. Users
- D. Terminal shell types on endpoints
Answer: AC
NEW QUESTION 19
......
Recommend!! Get the Full PCCET dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/PCCET-pdf-download.html (New 75 Q&As Version)