It is more faster and easier to pass the Paloalto-Networks PCNSA exam by using Realistic Paloalto-Networks Palo Alto Networks Certified Network Security Administrator questuins and answers. Immediate access to the Most up-to-date PCNSA Exam and find the same core area PCNSA questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Paloalto-Networks PCNSA Exam Dumps Below:
NEW QUESTION 1
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
- A. Create an Application Filter and name it Office Programs, the filter it on the business-systems category, office-programs subcategory
- B. Create an Application Group and add business-systems to it
- C. Create an Application Filter and name it Office Programs, then filter it on the business-systems category
- D. Create an Application Group and add Office 365, Evernote, Google Docs, and Libre Office
Answer: B
NEW QUESTION 2
Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone. Complete the security policy to ensure only Telnet is allowed.
Security Policy: Source Zone: Internal to DMZ Zone services “Application defaults”, and action = Allow
- A. Destination IP: 192.168.1.123/24
- B. Application = ‘Telnet’
- C. Log Forwarding
- D. USER-ID = ‘Allow users in Trusted’
Answer: B
NEW QUESTION 3
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
- A. Windows-based agent deployed on the internal network
- B. PAN-OS integrated agent deployed on the internal network
- C. Citrix terminal server deployed on the internal network
- D. Windows-based agent deployed on each of the WAN Links
Answer: A
NEW QUESTION 4
Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall?
- A. Threat Prevention License
- B. Threat Implementation License
- C. Threat Environment License
- D. Threat Protection License
Answer: A
NEW QUESTION 5
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
- A. Rule Usage Filter > No App Specified
- B. Rule Usage Filter >Hit Count > Unused in 30 days
- C. Rule Usage Filter > Unused Apps
- D. Rule Usage Filter > Hit Count > Unused in 90 days
Answer: D
NEW QUESTION 6
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
- A. control
- B. network processing
- C. data
- D. security processing
Answer: A
NEW QUESTION 7
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
- A. domain controller
- B. TACACS+
- C. LDAP
- D. RADIUS
Answer: C
NEW QUESTION 8
Which User-ID mapping method should be used for an environment with clients that do not authenticate to Windows Active Directory?
- A. Windows session monitoring via a domain controller
- B. passive server monitoring using the Windows-based agent
- C. Captive Portal
- D. passive server monitoring using a PAN-OS integrated User-ID agent
Answer: C
NEW QUESTION 9
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
- A. GlobalProtect
- B. AutoFocus
- C. Aperture
- D. Panorama
Answer: CD
Explanation:
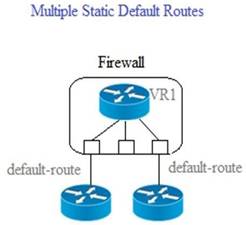 44. Given the scenario, which two statements are correct regarding multiple static default routes? (Choose two.)
44. Given the scenario, which two statements are correct regarding multiple static default routes? (Choose two.)
A. Path monitoring does not determine if route is useable
B. Route with highest metric is actively used
C. Path monitoring determines if route is useable
D. Route with lowest metric is actively used
NEW QUESTION 10
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?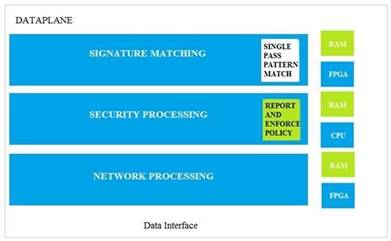
- A. Signature Matching
- B. Network Processing
- C. Security Processing
- D. Security Matching
Answer: A
NEW QUESTION 11
How many zones can an interface be assigned with a Palo Alto Networks firewall?
- A. two
- B. three
- C. four
- D. one
Answer: BC
Explanation:
 5. Which two configuration settings shown are not the default? (Choose two.)
5. Which two configuration settings shown are not the default? (Choose two.)
A. Enable Security Log
B. Server Log Monitor Frequency (sec)
C. Enable Session
D. Enable Probing
NEW QUESTION 12
Which two App-ID applications will need to be allowed to use Facebook- chat? (Choose two.)
- A. facebook
- B. facebook-chat
- C. facebook-base
- D. facebook-email
Answer: BC
NEW QUESTION 13
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- A. Block List
- B. Custom URL Categories
- C. PAN-DB URL Categories
- D. Allow List
Answer: AD
NEW QUESTION 14
What are three differences between security policies and security profiles? (Choose three.)
- A. Security policies are attached to security profiles
- B. Security profiles are attached to security policies
- C. Security profiles should only be used on allowed traffic
- D. Security profiles are used to block traffic by themselves
- E. Security policies can block or allow traffic
Answer: BCE
NEW QUESTION 15
Which option shows the attributes that are selectable when setting up application filters?
- A. Category, Subcategory, Technology, and Characteristic
- B. Category, Subcategory, Technology, Risk, and Characteristic
- C. Name, Category, Technology, Risk, and Characteristic
- D. Category, Subcategory, Risk, Standard Ports, and Technology
Answer: B
NEW QUESTION 16
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
- A. 2-3-4-1
- B. 1-4-3-2
- C. 3-1-2-4
- D. 1-3-2-4
Answer: D
NEW QUESTION 17
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
- A. Active Directory monitoring
- B. Windows session monitoring
- C. Windows client probing
- D. domain controller monitoring
Answer: A
NEW QUESTION 18
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?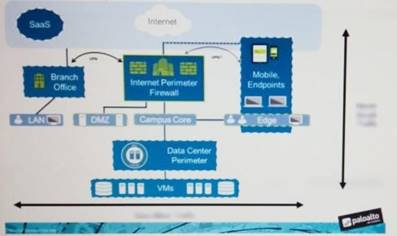
- A. branch office traffic
- B. north-south traffic
- C. perimeter traffic
- D. east-west traffic
Answer: D
NEW QUESTION 19
In the example security policy shown, which two websites would be blocked? (Choose two.)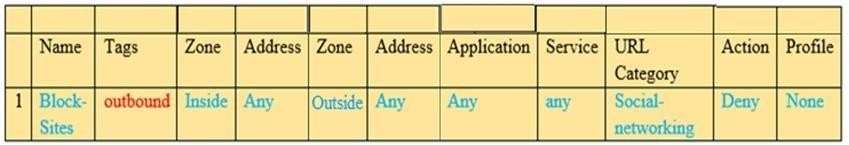
- A. LinkedIn
- B. Facebook
- C. YouTube
- D. Amazon
Answer: AB
NEW QUESTION 20
Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application?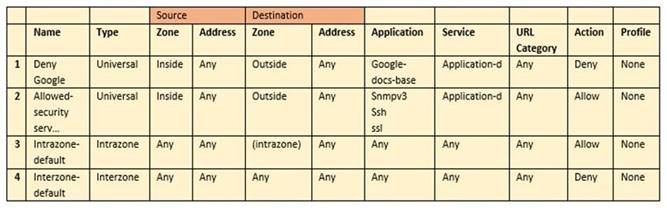
- A. intrazone-default
- B. Deny Google
- C. allowed-security services
- D. interzone-default
Answer: D
NEW QUESTION 21
......
Recommend!! Get the Full PCNSA dumps in VCE and PDF From Dumpscollection.com, Welcome to Download: https://www.dumpscollection.net/dumps/PCNSA/ (New 115 Q&As Version)