It is more faster and easier to pass the Microsoft SC-300 exam by using Download Microsoft Microsoft Identity and Access Administrator questuins and answers. Immediate access to the Refresh SC-300 Exam and find the same core area SC-300 questions with professionally verified answers, then PASS your exam with a high score now.
Online Microsoft SC-300 free dumps demo Below:
NEW QUESTION 1
You have an on-premises Microsoft Exchange organization that uses an SMTP address space of contoso.com. You discover that users use their email address for self-service sign-up to Microsoft 365 services.
You need to gain global administrator privileges to the Azure Active Directory (Azure AD) tenant that contains the self-signed users.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.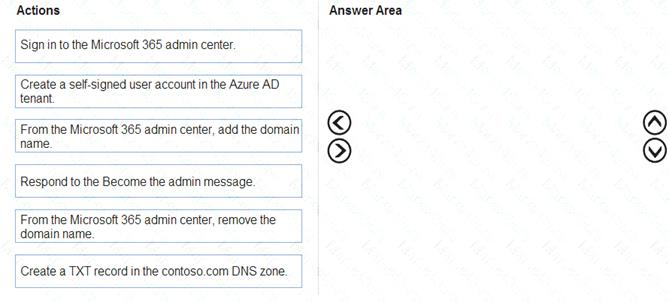
- A.
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/domains-admin-takeover
NEW QUESTION 2
You have a Microsoft 365 E5 tenant. You purchase a cloud app named App1.
You need to enable real-time session-level monitoring of App1 by using Microsoft Cloud app Security.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.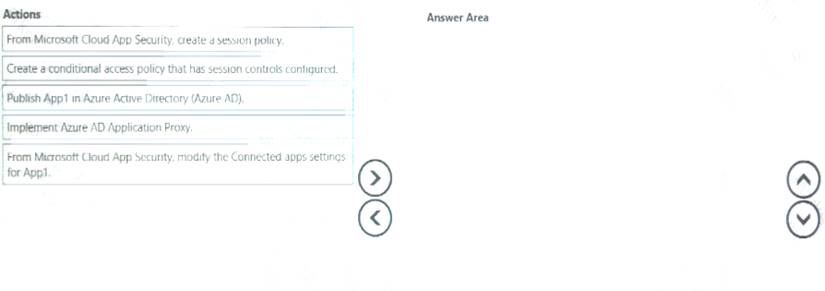
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 3
You have a Microsoft 365 tenant named contoso.com. Guest user access is enabled.
Users are invited to collaborate with contoso.com as shown in the following table.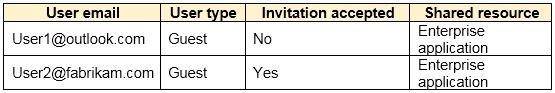
From the External collaboration settings in the Azure Active Directory admin center, you configure the Collaboration restrictions settings as shown in the following exhibit.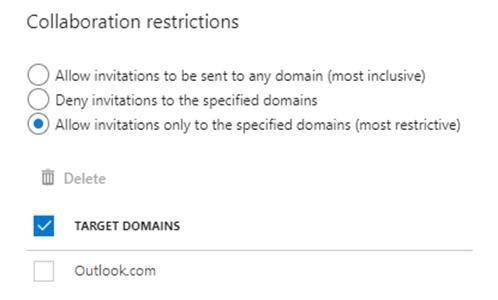
From a Microsoft SharePoint Online site, a user invites user3@adatum.com to the site.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE:Each correct selection is worth one point.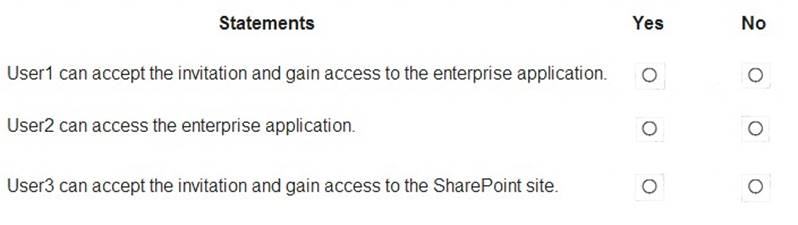
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Yes
Invitations can only be sent to outlook.com. Therefore, User1 can accept the invitation and access the application.
Box 2. Yes
Invitations can only be sent to outlook.com. However, User2 has already received and accepted an invitation so User2 can access the application.
Box 3. No
Invitations can only be sent to outlook.com. Therefore, User3 will not receive an invitation.
NEW QUESTION 4
You need to implement password restrictions to meet the authentication requirements. You install the Azure AD password Protection DC agent on DC1.
What should you do next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.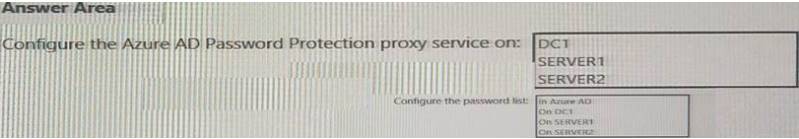
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 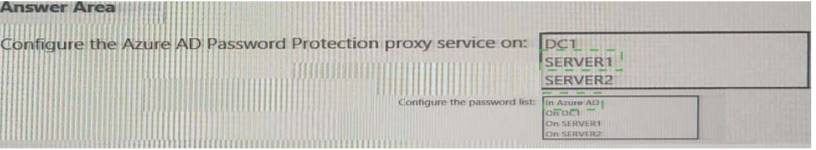
NEW QUESTION 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click theExhibittab.)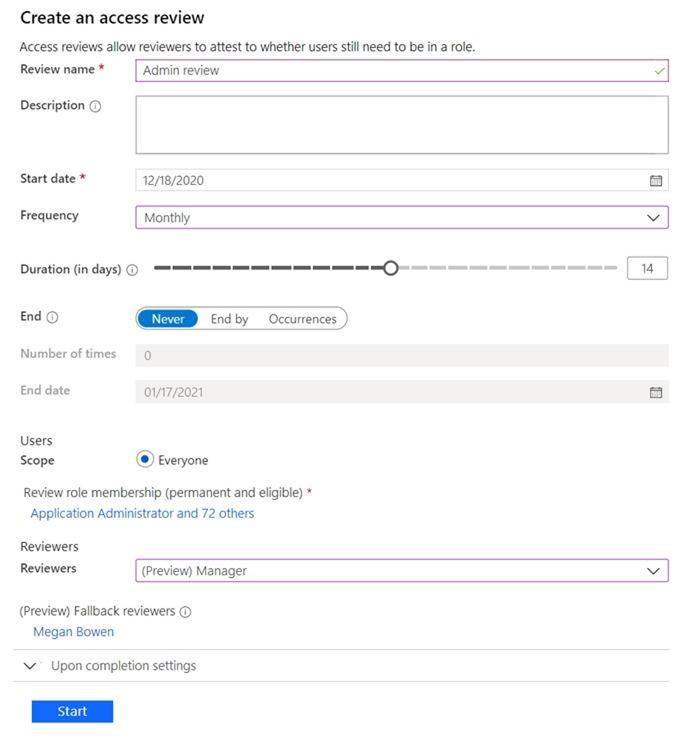
You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You modify the properties of the IT administrator user accounts. Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation:
Reference:
D18912E1457D5D1DDCBD40AB3BF70D5D
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
NEW QUESTION 6
Your network contains an Active Directory forest named contoso.com that is linked to an Azure Active
Directory (Azure AD) tenant named contoso.com by using Azure AD Connect. Attire AD Connect is installed on a server named Server 1.
You deploy a new server named Server? that runs Windows Server 2019.
You need to implement a failover server for Azure AD Connect. The solution must minimize how long it takes to fail over if Server1 fails.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 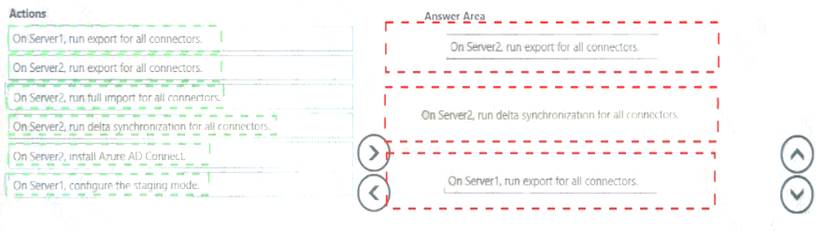
NEW QUESTION 7
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1 and the groups shown in the following table.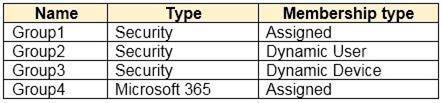
In the tenant, you create the groups shown in the following table.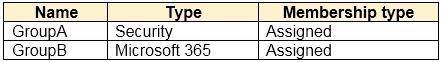
Which members can you add to GroupA and GroupB? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.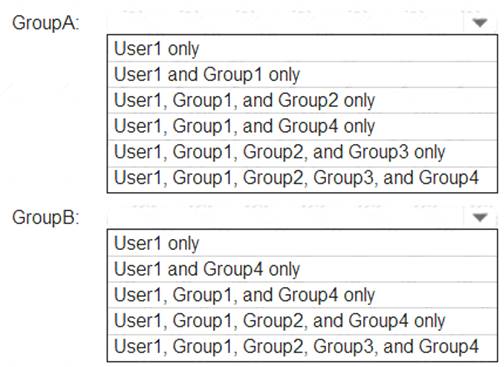
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference:
https://bitsizedbytes.wordpress.com/2018/12/10/distribution-security-and-office-365-groups-nesting/
NEW QUESTION 8
Your network contains an on-premises Active Directory domain that sync to an Azure Active Directory (Azure AD) tenant. The tenant contains the shown in the following table.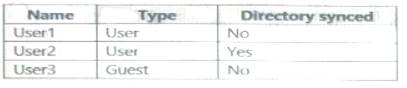
All the users work remotely.
Azure AD Connect is configured in Azure as shown in the following exhibit.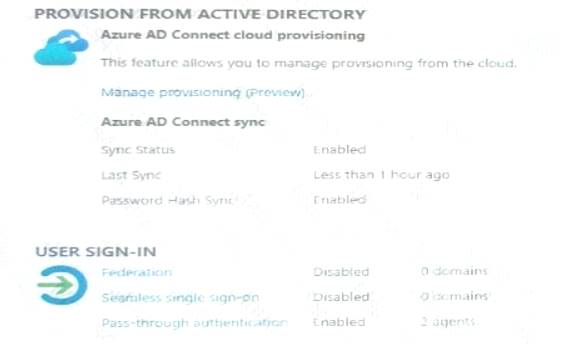
Connectivity from the on-premises domain to the internet is lost. Which user can sign in to Azure AD?
- A. User1 only
- B. User1 and User 3 only
- C. User1, and User2 only
- D. User1, User2, and User3
Answer: A
NEW QUESTION 9
You have a new Microsoft 365 tenant that uses a domain name of contoso.conmicrosoft.com. You register the name contoso.com with a domain registrar.
You need to use contoso.com as the default domain name for new Microsoft 365 users.
Which four actions should you perform in sequenced? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.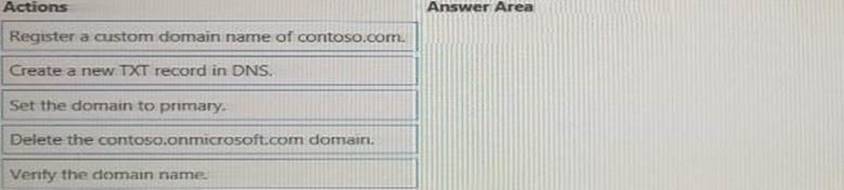
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 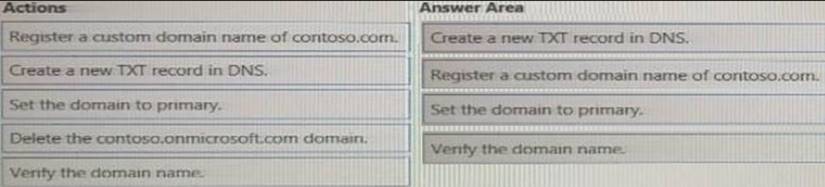
NEW QUESTION 10
Your company recently implemented Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
While you review the roles in PIM, you discover that all 15 users in the IT department at the company have permanent security administrator rights.
You need to ensure that the IT department users only have access to the Security administrator role when required.
What should you configure for the Security administrator role assignment?
- A. Expire eligible assignments afterfrom the Role settings details
- B. Expire active assignments afterfrom the Role settings details
- C. Assignment type toActive
- D. Assignment type toEligible
Answer: D
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
NEW QUESTION 11
You have an Azure subscription that contains the resource shown in the following table.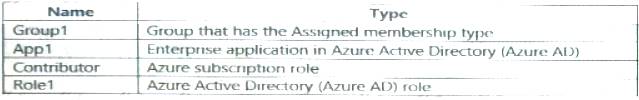
For which resources can you create an access review?
- A. Group1, App1, Contributor, and Role1
- B. Hotel and Contributor only
- C. Group1, Role1, and Contributor only
- D. Group1 only
Answer: D
NEW QUESTION 12
You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not Initiate. Solution: From the Azure portal, you configure the Block/unblock users settings for multi-factor
authentication (MFA).
Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click theExhibittab.)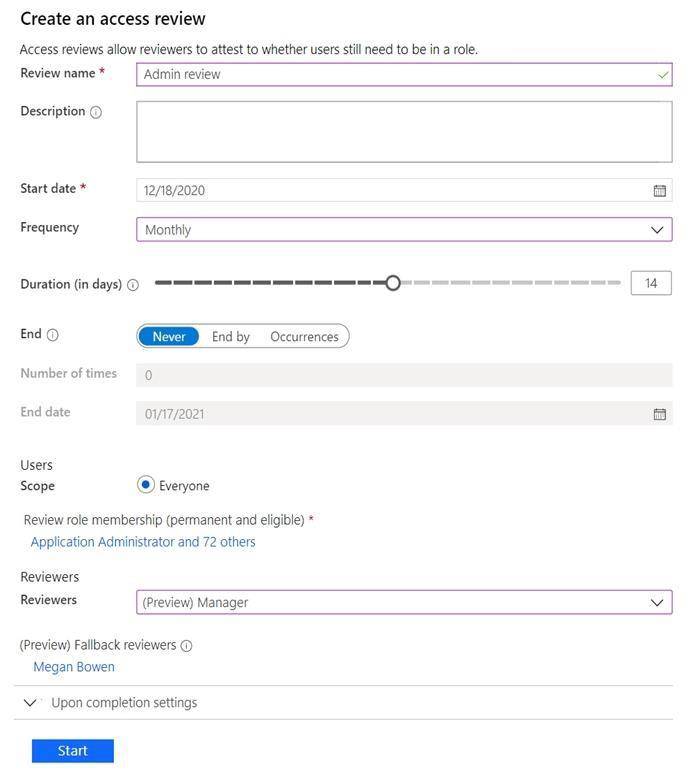
You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You create a separate access review for each role.
Does this meet the goal?
- A. Yes
- B. NoD18912E1457D5D1DDCBD40AB3BF70D5D
Answer: B
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
NEW QUESTION 14
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and the users who access them.
What should you use to gather the information?
- A. Application Insights in Azure Monitor
- B. access reviews in Azure AD
- C. Cloud App Discovery in Microsoft Cloud App Security
- D. enterprise applications in Azure AD
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/create-snapshot-cloud-discovery-reports#using-traffic-logs
NEW QUESTION 15
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click theExhibittab.)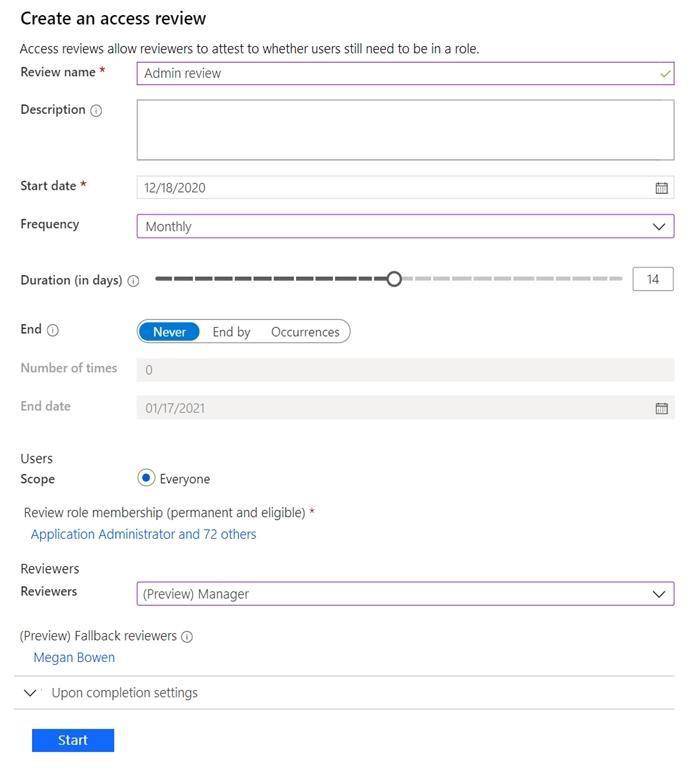
You discover that all access review requests are received by Megan Bowen.
You need to ensure that the manager of each department receives the access reviews of their respective department.
Solution: You set Reviewers to Member (self).
Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 16
You have an Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.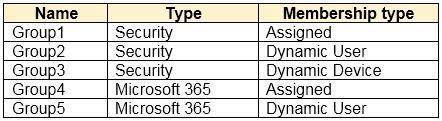
For which groups can you create an access review?
- A. Group1 only
- B. Group1 and Group4 only
- C. Group1 and Group2 only
- D. Group1, Group2, Group4, and Group5 only
- E. Group1, Group2, Group3, Group4 and Group5
Answer: D
Explanation:
You cannot create access reviews for device groups. Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
NEW QUESTION 17
You use Azure Monitor to analyze Azure Active Directory (Azure AD) activity logs.
Yon receive more than 100 email alerts each day for tailed Azure Al) user sign-in attempts. You need to ensure that a new security administrator receives the alerts instead of you. Solution: From Azure AD, you create an assignment for the Insights at administrator role. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 18
Your company has two divisions named Contoso East and Contoso West. The Microsoft 365 identity architecture tor both divisions is shown in the following exhibit.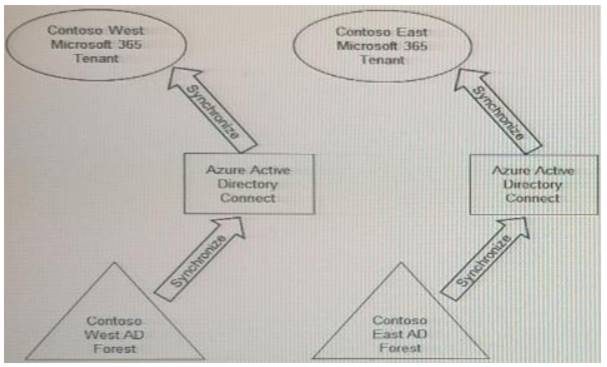
You need to assign users from the Contoso East division access to Microsoft SharePoint Online sites in the Contoso West tenant. The solution must not require additional Microsoft 3G5 licenses.
What should you do?
- A. Configure The exiting Azure AD Connect server in Contoso Cast to sync the Contoso East Active Directory forest to the Contoso West tenant.
- B. Configure Azure AD Application Proxy in the Contoso West tenant.
- C. Deploy a second Azure AD Connect server to Contoso East and configure the server to sync theContoso East Active Directory forest to the Contoso West tenant.
- D. Create guest accounts for all the Contoso East users in the West tenant.
Answer: D
NEW QUESTION 19
You need to configure the detection of multi-staged attacks to meet the monitoring requirements. What should you do?
- A. Customize the Azure Sentinel rule logic.
- B. Create a workbook.
- C. Add Azure Sentinel data connectors.
- D. Add an Azure Sentinel playbook.
Answer: A
NEW QUESTION 20
Your company has an Azure Active Directory (Azure AD) tenant named contosri.com. The company has the business partners shown in the following table.
users can request access by using package 1.
Users at Fabrikam and Litware use ail then respective domain names for email addresses.
You plan to create an access package named packaqel that will be accessible only to the Fabrikam and Litware users.
You need to configure connected organizations for Fabrikam and litware so that any of their users can request access by using package1.
What is the minimum of connected organization that you should create.
- A. 1
- B. 2
- C. 3
- D. 4
Answer: C
NEW QUESTION 21
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users.
From the Groups blade in the Azure Active Directory admin center, you assign Microsoft 365 Enterprise E5 licenses to the users.
You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort.
What should you use?
- A. the Identity Governance blade in the Azure Active Directory admin center
- B. theSet-AzureAdUsercmdlet
- C. the Licenses blade in the Azure Active Directory admin center
- D. theSet-WindowsProductKeycmdlet
Answer: C
NEW QUESTION 22
Your company has a Microsoft 365 tenant.
The company has a call center that contains 300 users. In the call center, the users share desktop computers and might use a different computer every day. The call center computers areNOTconfigured for biometric identification.
The users are prohibited from having a mobile phone in the call center.
You need to require multi-factor authentication (MFA) for the call center users when they access Microsoft 365
services.
What should you include in the solution?
- A. a named network location
- B. the Microsoft Authenticator app
- C. Windows Hello for Business authentication
- D. FIDO2 tokens
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless
NEW QUESTION 23
......
P.S. Easily pass SC-300 Exam with 52 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com SC-300 Dumps: https://www.dumps-hub.com/SC-300-dumps.html (52 New Questions)