Our pass rate is high to 98.9% and the similarity percentage between our 200-201 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Cisco 200-201 exam in just one try? I am currently studying for the Cisco 200-201 exam. Latest Cisco 200-201 Test exam practice questions and answers, Try Cisco 200-201 Brain Dumps First.
Cisco 200-201 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
What is rule-based detection when compared to statistical detection?
- A. proof of a user's identity
- B. proof of a user's action
- C. likelihood of user's action
- D. falsification of a user's identity
Answer: B
NEW QUESTION 2
What does an attacker use to determine which network ports are listening on a potential target device?
- A. man-in-the-middle
- B. port scanning
- C. SQL injection
- D. ping sweep
Answer: B
NEW QUESTION 3
Drag and drop the technology on the left onto the data type the technology provides on the right.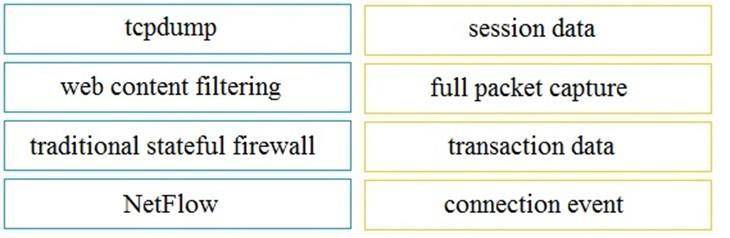
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 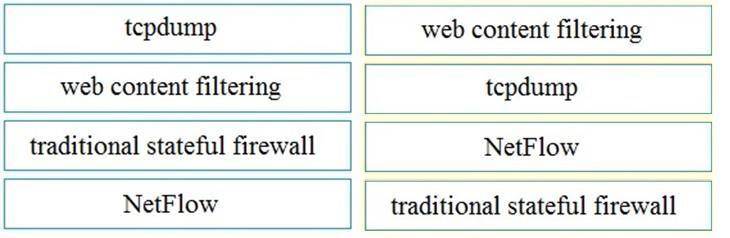
NEW QUESTION 4
What is a difference between SOAR and SIEM?
- A. SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
- B. SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
- C. SOAR receives information from a single platform and delivers it to a SIEM
- D. SIEM receives information from a single platform and delivers it to a SOAR
Answer: A
NEW QUESTION 5
Refer to the exhibit.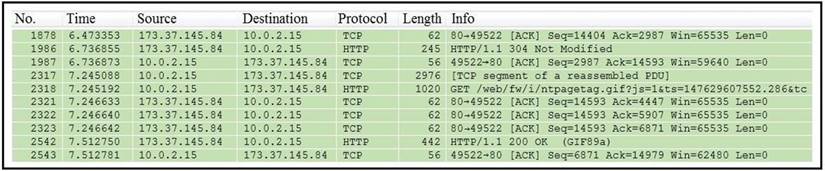
Which packet contains a file that is extractable within Wireshark?
- A. 2317
- B. 1986
- C. 2318
- D. 2542
Answer: D
NEW QUESTION 6
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
- A. context
- B. session
- C. laptop
- D. firewall logs
- E. threat actor
Answer: AE
NEW QUESTION 7
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
- A. ransomware communicating after infection
- B. users downloading copyrighted content
- C. data exfiltration
- D. user circumvention of the firewall
Answer: D
NEW QUESTION 8
Refer to the exhibit.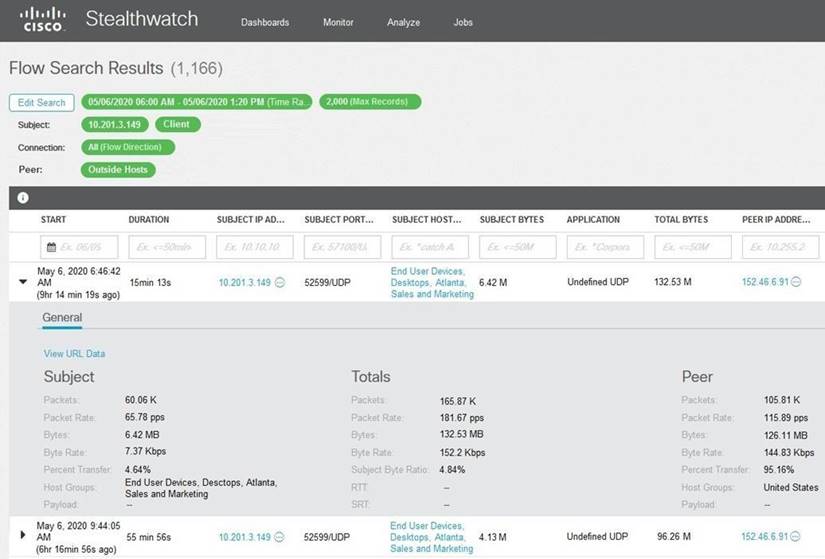
What is the potential threat identified in this Stealthwatch dashboard?
- A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
- B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
- C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
- D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Answer: D
NEW QUESTION 9
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
- A. Untampered images are used in the security investigation process
- B. Tampered images are used in the security investigation process
- C. The image is tampered if the stored hash and the computed hash match
- D. Tampered images are used in the incident recovery process
- E. The image is untampered if the stored hash and the computed hash match
Answer: BE
NEW QUESTION 10
Which system monitors local system operation and local network access for violations of a security policy?
- A. host-based intrusion detection
- B. systems-based sandboxing
- C. host-based firewall
- D. antivirus
Answer: C
NEW QUESTION 11
Refer to the exhibit.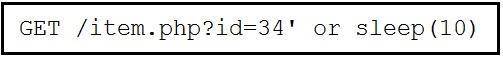
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
- A. parameter manipulation
- B. heap memory corruption
- C. command injection
- D. blind SQL injection
Answer: D
NEW QUESTION 12
Which regular expression matches "color" and "colour"?
- A. colo?ur
- B. col[08]+our
- C. colou?r
- D. col[09]+our
Answer: C
NEW QUESTION 13
What is a purpose of a vulnerability management framework?
- A. identifies, removes, and mitigates system vulnerabilities
- B. detects and removes vulnerabilities in source code
- C. conducts vulnerability scans on the network
- D. manages a list of reported vulnerabilities
Answer: A
NEW QUESTION 14
Which security technology allows only a set of pre-approved applications to run on a system?
- A. application-level blacklisting
- B. host-based IPS
- C. application-level whitelisting
- D. antivirus
Answer: C
NEW QUESTION 15
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
- A. queries Linux devices that have Microsoft Services for Linux installed
- B. deploys Windows Operating Systems in an automated fashion
- C. is an efficient tool for working with Active Directory
- D. has a Common Information Model, which describes installed hardware and software
Answer: D
NEW QUESTION 16
Which two components reduce the attack surface on an endpoint? (Choose two.)
- A. secure boot
- B. load balancing
- C. increased audit log levels
- D. restricting USB ports
- E. full packet captures at the endpoint
Answer: AD
NEW QUESTION 17
Which type of data consists of connection level, application-specific records generated from network traffic?
- A. transaction data
- B. location data
- C. statistical data
- D. alert data
Answer: A
NEW QUESTION 18
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
- A. least privilege
- B. need to know
- C. integrity validation
- D. due diligence
Answer: A
NEW QUESTION 19
......
P.S. Easily pass 200-201 Exam with 98 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com 200-201 Dumps: https://www.dumpscollection.net/dumps/200-201/ (98 New Questions)