Your success in Cisco 200-201 is our sole target and we develop all our 200-201 braindumps in a way that facilitates the attainment of this target. Not only is our 200-201 study material the best you can find, it is also the most detailed and the most updated. 200-201 Practice Exams for Cisco 200-201 are written to the highest standards of technical accuracy.
Also have 200-201 free dumps questions for you:
NEW QUESTION 1
Refer to the exhibit.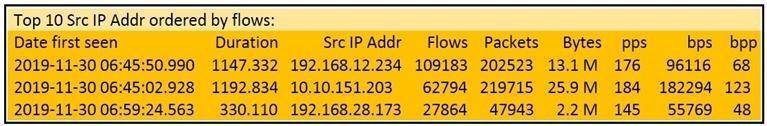
What information is depicted?
- A. IIS data
- B. NetFlow data
- C. network discovery event
- D. IPS event data
Answer: B
NEW QUESTION 2
What is a benefit of agent-based protection when compared to agentless protection?
- A. It lowers maintenance costs
- B. It provides a centralized platform
- C. It collects and detects all traffic locally
- D. It manages numerous devices simultaneously
Answer: B
NEW QUESTION 3
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
- A. true negative
- B. false negative
- C. false positive
- D. true positive
Answer: B
NEW QUESTION 4
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
- A. The computer has a HIPS installed on it.
- B. The computer has a NIPS installed on it.
- C. The computer has a HIDS installed on it.
- D. The computer has a NIDS installed on it.
Answer: C
NEW QUESTION 5
Which type of evidence supports a theory or an assumption that results from initial evidence?
- A. probabilistic
- B. indirect
- C. best
- D. corroborative
Answer: D
NEW QUESTION 6
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
- A. encapsulation
- B. TOR
- C. tunneling
- D. NAT
Answer: D
NEW QUESTION 7
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
- A. syslog messages
- B. full packet capture
- C. NetFlow
- D. firewall event logs
Answer: C
NEW QUESTION 8
Refer to the exhibit.
In which Linux log file is this output found?
- A. /var/log/authorization.log
- B. /var/log/dmesg
- C. var/log/var.log
- D. /var/log/auth.log
Answer: D
NEW QUESTION 9
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
- A. ClientStart, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
- B. ClientStart, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- C. ClientHello, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- D. ClientHello, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
Answer: C
NEW QUESTION 10
What is the function of a command and control server?
- A. It enumerates open ports on a network device
- B. It drops secondary payload into malware
- C. It is used to regain control of the network after a compromise
- D. It sends instruction to a compromised system
Answer: D
NEW QUESTION 11
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
- A. known-plaintext
- B. replay
- C. dictionary
- D. man-in-the-middle
Answer: D
NEW QUESTION 12
How does certificate authority impact a security system?
- A. It authenticates client identity when requesting SSL certificate
- B. It validates domain identity of a SSL certificate
- C. It authenticates domain identity when requesting SSL certificate
- D. It validates client identity when communicating with the server
Answer: B
NEW QUESTION 13
How is attacking a vulnerability categorized?
- A. action on objectives
- B. delivery
- C. exploitation
- D. installation
Answer: C
NEW QUESTION 14
Which regex matches only on all lowercase letters?
- A. [az]+
- B. [^az]+
- C. az+
- D. a*z+
Answer: A
NEW QUESTION 15
Refer to the exhibit.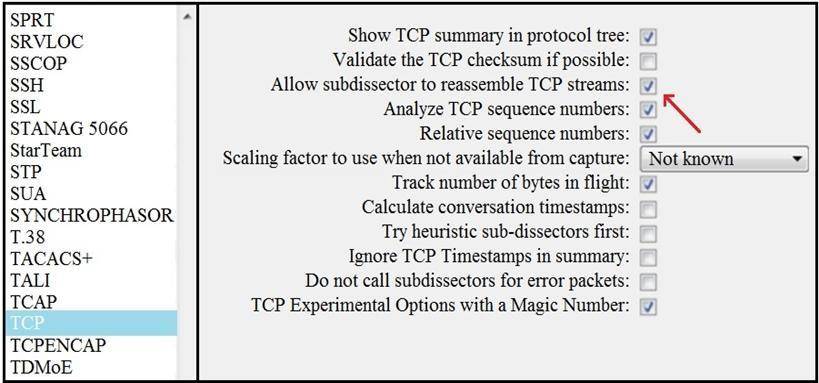
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
- A. insert TCP subdissectors
- B. extract a file from a packet capture
- C. disable TCP streams
- D. unfragment TCP
Answer: D
NEW QUESTION 16
Which action prevents buffer overflow attacks?
- A. variable randomization
- B. using web based applications
- C. input sanitization
- D. using a Linux operating system
Answer: C
NEW QUESTION 17
What is the difference between statistical detection and rule-based detection models?
- A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
- B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
- C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
- D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Answer: B
NEW QUESTION 18
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
- A. forgery attack
- B. plaintext-only attack
- C. ciphertext-only attack
- D. meet-in-the-middle attack
Answer: C
NEW QUESTION 19
......
Recommend!! Get the Full 200-201 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/200-201/ (New 98 Q&As Version)