Proper study guides for 70-414 Implementing an Advanced Server Infrastructure certified begins with preparation products which designed to deliver the by making you pass the 70-414 test at your first time. Try the free right now.
Also have 70-414 free dumps questions for you:
NEW QUESTION 1
You need to recommend a solution that meets the technical requirements for DHCP. What should you include in the recommendation for each office?
- A. DHCP failover
- B. Network Load Balancing (NLB)
- C. DHCP server policies
- D. IP Address Management (IPAM)
Answer: A
NEW QUESTION 2
You need to implement a new highly available storage solution for the Hyper-V environment. Which servers should you include in the scale-out file cluster?
- A. CHI-SERVER1 and CHI-SERVER2
- B. SEA3-HVNODE1 and SEA3-HVNODE2
- C. SEA-SERVER1 and SEA-SERVER2
- D. CHIl-HVNODE1 and CHI1-HVNODE2
Answer: C
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System Center 2012 infrastructure.
You deploy a service named Service1 by using a service template. Service1 contains two virtual machines. The virtual machines are configured as shown in the following table.
You need to recommend a monitoring solution to ensure that an administrator can review the availability information of Service1.
You need to recommend a monitoring solution to ensure that an administrator can review the availability information of Service1.
Solution: From Configuration Manager, you create a Collection and a Desired Configuration Management baseline.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 4
Your network contains an Active Directory domain named contoso.com. The domain contains four servers named Server1, Server2, Server3 and Server4 that run Windows Server 2012.
Server1 and Server2 are configured as file servers and are part of a failover cluster named Cluster1. Server3 and Server4 have Microsoft SQL Server 2012 installed and are part of a failover cluster named Cluster2.
You add a disk named Disk1 to the nodes in Cluster1. Disk1 will be used to store the data files and log files used by SQL Server 2012.
You need to configure the environment so that access to Disk1 remains available when a node on Cluster1 fails over or fails back.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.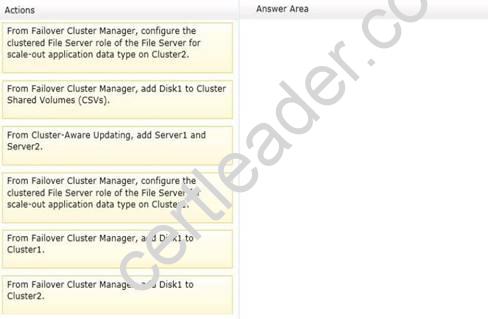
Answer:
Explanation: 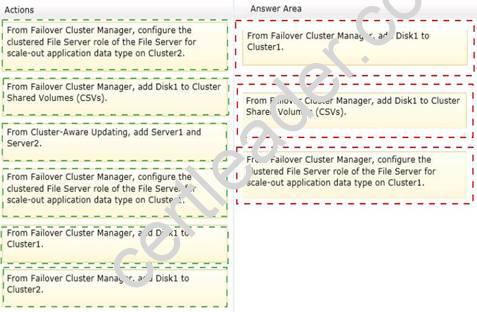
NEW QUESTION 5
Your network contains 10 servers that run Windows Server 2012. The servers have the Hyper-V server role installed. The servers host a Virtual Desktop Infrastructure (VDI) that contains persistent virtual machines. Each virtual machine is assigned to a specific user. Users can install software on their specific virtual machine.
You need to implement a solution to generate monthly reports that contain a list of all the installed software on the virtual machines. The solution must NOT require the installation of additional software on the virtual machines.
Which solution should you implement?
- A. A Microsoft System Center 2012 Configuration Manager software inventory
- B. A Microsoft System Center 2012 Configuration Manager hardware inventory
- C. Microsoft Assessment and Planning (MAP) Toolkit scans
- D. Microsoft Audit Collection Services (ACS) audit logs
Answer: C
Explanation: 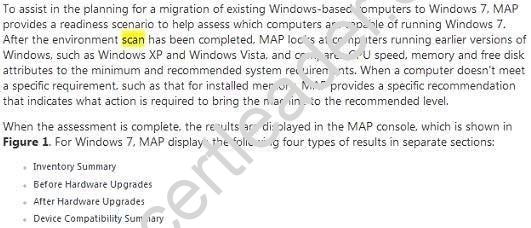
NEW QUESTION 6
An organization uses an Active Directory Rights Management Services (AD RMS) cluster named RMS1 to protect content for a project. You uninstall AD RMS when the project is complete. You need to ensure that the protected content is still available after AD RMS is uninstalled.
Solution: You enable the decommissioning service by using the AD RMS management console. You grant all users the Read & Execute permission to the decommission pipeline.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: The proper procedure is:
Inform your users that you are decommissioning the AD RMS installation and advise them to connect to the cluster to save their content without AD RMS protection. Alternatively, you could delegate a trusted person to decrypt all rights-protected content by temporarily adding that person to the AD RMS super users group.
After you believe that all of the content is unprotected and saved, you should export the server licensor certificate, and then uninstall AD RMS from the server.
NEW QUESTION 7
You need to implement the network Unlock feature to meet the BitLocker requirements.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.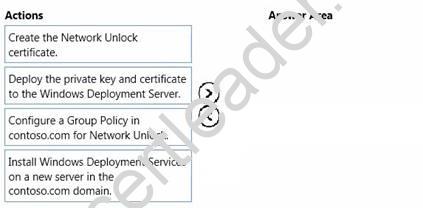
Answer:
Explanation: 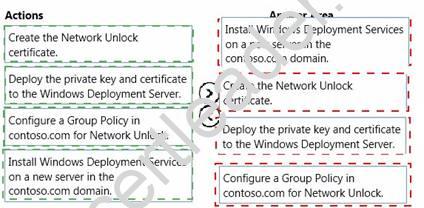
NEW QUESTION 8
You plan to implement 20 highly available virtual machines on FC1, All of the virtual machines must be stored in a single shared folder You need to ensure that the VHD Files of the virtual machines can be stored on SAN1, VHD files must be available from any node in FC2.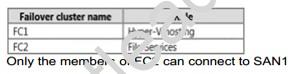
What should you do on FC2 ?
- A. Configure the clustered File server role o( the filer server tor general use.
- B. Add the iSCSI target server cluster role.
- C. Configure the clustered file server role of the scale-out file server for application data.
- D. Add the storage services role service.
Answer: BC
NEW QUESTION 9
You need to recommend a solution for updating the virtualization hosts. The solution must meet the visualization requirements.
What should you include in the recommendation?
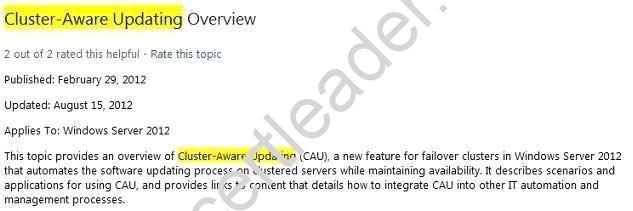
- A. Cluster-Aware Updating
- B. WSUS
- C. System Center Updates Publisher 2011
- D. System Center 2012 Configuration Manager
Answer: A
Explanation: 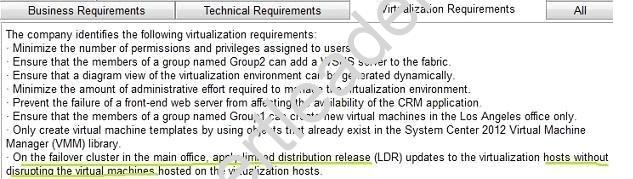
NEW QUESTION 10
You need to configure access to the Certificate Revocation Lists (CRLs).
How should you configure the access? To answer, drag the appropriate protocol or servers to the correct network type. Each protocol or server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.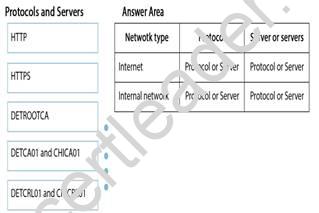
Answer:
Explanation: First line: Protocol: HTTP, Server or servers: DETCA01 and CHICA01 Second line: Protocol: HTTP, Server or servers: DETCA01 and CHICA01
NEW QUESTION 11
Your network contains an Active Directory domain named contoso.com. The network has an Active Directory Certificate Services (AD CS) infrastructure.
You publish the certificate revocation list (CRL) to a farm of Web servers. You are creating a disaster recovery plan for the AD CS infrastructure. You need to recommend which actions must be performed to restore certificate revocation checking if a certification authority (CA) is offline for an extended period of time.
Which three actions should you recommend? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.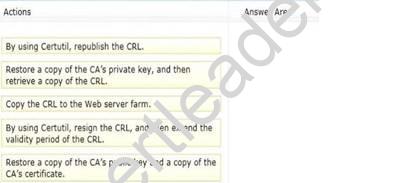
Answer:
Explanation: 
NEW QUESTION 12
You need to enable virtual machine network health detection on all supported clusters. What should you do?
- A. On the virtual machine settings page for Cluster4, select the Protect network checkbox for each virtual machine on the cluster.
- B. On the virtual machine settings page for Cluster1, select the Protect network checkbox for each virtual machine on the cluster.
- C. On each guest virtual machine in Cluster4, configure protected access for the network interface card.
- D. On each guest virtual machine in Cluster3, configure protected access for the network interface card.
- E. On the virtual machine settings page for Cluster3, select the Protect network checkbox for each virtual machine on the cluster.
- F. On each guest virtual machine in Cluster1, configure protected access for the network interface card.
Answer: E
Explanation: Protected network option is available on the VM settings page for the cluster, not on each VM. Also Protected Network is a 2012R2 feature. Cluster1 is all 2012. And, Cluster4 is 2012R2, but only has a single network. The only option left is E with Cluster3.
NEW QUESTION 13
Your network contains multiple servers that run Windows Server 2012.
You plan to implement three virtual disks. The virtual disks will be configured as shown in the following table.
You need to identify the minimum number of physical disks required for each virtual disk. How many disks should you identify?
To answer, drag the appropriate number of disks to the correct virtual disk in the answer area. Each number of disks may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.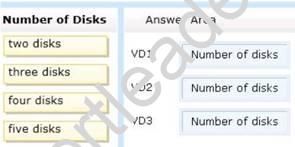
Answer:
Explanation: http://technet.microsoft.com/es-es/library/jj822938.aspx
They are not talking about Clusters, a single server only, so a standalone server.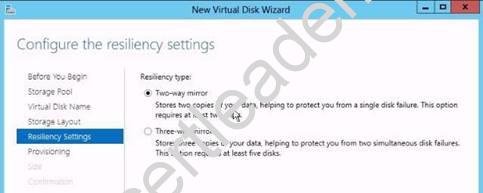
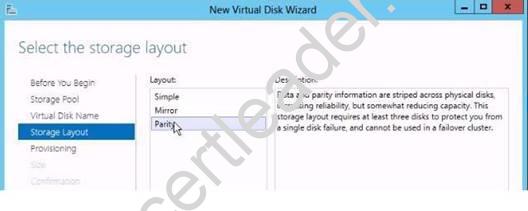
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System Center 2012 infrastructure.
You deploy a second System Center 2012 infrastructure in a test environment.
You create a service template named Template1 in both System Center 2012 infrastructures.
For self-service users, you create a service offering for Template1. The users create 20 instances of Template1. You modify Template1 in the test environment. You export the service template to a file named
Template1.xml.
You need to ensure that the changes to Template1 can be applied to the existing instances in the production environment.
What should you do when you import the template?
- A. Overwrite the current service template.
- B. Change the name of the service template.
- C. Create a new service template.
- D. Change the release number of the service template.
Answer: D
NEW QUESTION 15
You have a Hyper-V host named Hyper1 that has Windows Server 2012 installed. Hyper1 hosts 20 virtual machines.
Hyper1 has one physical network adapter.
You need to implement a networking solution that evenly distributes the available bandwidth on Hyper1 to all of the virtual machines.
What should you modify?
- A. The settings of the virtual switch
- B. The settings of the virtual network adapter
- C. The Quality of Service (QoS) Packet Scheduler settings of the physical network adapter
- D. The settings of the legacy network adapter
Answer: A
NEW QUESTION 16
This question consists of two statements: One is named Assertion and the other is named Reason. Both of these statements may be true; both may be false; or one may be true, while the other may be false.
To answer this question, you must first evaluate whether each statement is true on its own. If both statements are true, then you must evaluate whether the Reason (the second statement) correctly explains the Assertion (the first statement). You will then select the answer from the list of answer choices that matches your evaluation of the two statements.
Assertion:
You can manage VMware ESX hosts and virtual machines by using a System Center Virtual Machine Manager (SCVMM) server.
Reason:
SCVMM automatically imports ESX hosts and virtual machines when you add the corresponding VMware vCenter to the SCVMM server.
Evaluate the Assertion and Reason statements and choose the correct answer option.
- A. Both the Assertion and Reason are true, and the Reason is the correct explanation for the Assertion.
- B. Both the Assertion and Reason are true, but the Reason is not the correct explanation for the Assertion.
- C. The Assertion is true, but the Reason is false.
- D. The Assertion is false, but the Reason is true.
- E. Both the Assertion and the Reason are false.
Answer: C
Explanation: * Assertion: true
Virtual Machine Manager (VMM) enables you to deploy and manage virtual machines and services across multiple hypervisor platforms, including VMware ESX and ESXi hosts.
* Reason: False
When you add a vCenter Server, VMM no longer imports, merges and synchronizes the VMware tree structure with VMM. Instead, after you add a vCenter Server, you can add selected ESX servers and hosts to any VMM host group. Therefore, there are fewer issues with synchronization.
NEW QUESTION 17
You have a System Center 2012 R2 Virtual Machine Manager (VMM) deployment. You implement Hyper-V Recovery Manager for the deployment.
You create two new clouds named Cloud1 and Cloud2. Metadata for both clouds is uploaded to Windows Azure.
You need to ensure that the virtual machines in Cloud1 are protected by using replicas in Cloud2.
Where should you perform each action? To answer, select the appropriate tool for each action in the answer area.
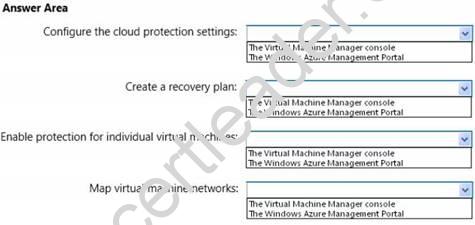
Answer:
Explanation: 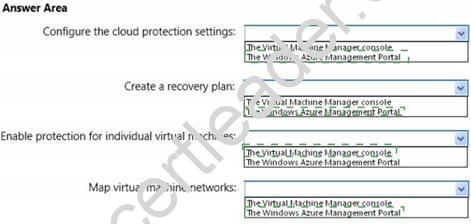
Recommend!! Get the Full 70-414 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/70-414-dumps.html (New 270 Q&As Version)