Act now and download your today! Do not waste time for the worthless tutorials. Download with real questions and answers and begin to learn with a classic professional.
Check 70-414 free dumps before getting the full version:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com.
You plan to deploy an Active Directory Federation Services (AD FS) farm that will contain eight federation servers.
You need to identify which technology or technologies must be deployed on the network before you install the federation servers.
Which technology or technologies should you identify? (Each correct answer presents part of the solution. Choose all that apply.)
- A. Network Load Balancing (NLB)
- B. Microsoft Forefront Identity Manager (FIM) 2010
- C. The Windows Internal Database feature
- D. Microsoft SQL Server 2012
- E. The Windows Identity Foundation 3.5 feature
Answer: AD
Explanation: Explanation:
Best practices for deploying a federation server farm. We recommend the following best practices for deploying a federation server in a production environment:
* (A) Use NLB or some other form of clustering to allocate a single IP address for many federation server computers.
* (D) If the AD FS configuration database will be stored in an SQL database, avoid editing the SQL database
from multiple federation servers at the same time.
* If you will be deploying multiple federation servers at the same time or you know that you will be adding more servers to the farm over time, consider creating a server image of an existing federation server in the farm and then installing from that image when you need to create additional federation servers quickly.
* Reserve a static IP address for each federation server in the farm and, depending on your Domain Name System (DNS) configuration, insert an exclusion for each IP address in Dynamic Host Configuration Protocol (DHCP). Microsoft NLB technology requires that each server that participates in the NLB cluster be assigned a static IP address.
NEW QUESTION 2
You need to ensure that the developers can manage their own virtual machines. Solution: You perform the following tasks:
In Virtual Machine Manager, you create a new user role named DevUsers that uses the Application Administrator profile.
You add the virtual machines to the DevUsers role.
You grant Checkpoint permissions to the DevUsers role.
You install and configure App Controller.
You distribute the App Controller console URL to the developers. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. You deploy Active Directory Certificate Services (AD CS). You plan to deploy 100 external Web servers that will be publicly accessible and will require Secure Sockets Layer (SSL) certificates.
You also plan to deploy 50,000 certificates for secure email exchanges with Internet-based recipients. You need to recommend a certificate services solution for the planned deployment.
What should you recommend? More than one answer choice may achieve the goal. Select the BEST answer.
- A. Deploy a certification authority (CA) that is subordinate to an external root CA.
- B. Purchase 50,100 certificates from a trusted third-party root certification authority (CA).
- C. Distribute a copy of the root certification authority (CA) certificate to external relying parties.
- D. Instruct each user to request a Secure Email certificate from a trusted third-party root CA, and then purchase 100 Web server certificates.
Answer: A
Explanation: 
NEW QUESTION 4
Your network contains an Active Directory domain named contoso.com. The network contains two servers named Server1 and Server2.
You deploy Active Directory Certificate Services (AD CS). The certification authority (CA) is configured as shown in the exhibit. (Click the Exhibit button.)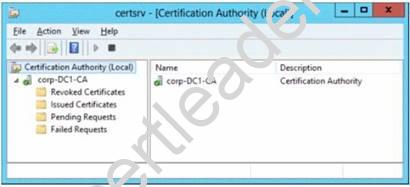
You need to ensure that you can issue certificates based on certificate templates. What should you do?
- A. On Server1, install the Network Device Enrollment Service role service.
- B. Configure Server2 as a standalone subordinate CA.
- C. On Server1, uninstall, and then reinstall AD CS.
- D. On Server1, run the Add-CertificateEnrollmentPolicyServer cmdlet.
Answer: C
Explanation: In a typical CA infrastructure the Stand-alone CAs are primarily intended to be used as Trusted Offline RootCAs in a CA hierarchy or when extranets and the Internet are involved. In a stand-alone CA Certificate templates are not used. An enterprise CA uses certificate types, which are based on a certificate template.
NEW QUESTION 5
You plan to allow users to run internal applications from outside the company’s network. You have a Windows Server 2012 R2 that has the Active Directory Federation Services (AD FS) role installed. You must secure on-premises resources by using multi-factor authentication (MFA). You need to design a solution to enforce different access levels for users with personal Windows 8.1 or iOS 8 devices.
Solution: You install a local instance of the MFA Server. You connect the instance to the Microsoft Azure MFA provider and then you use Microsoft Intune to manage personal devices.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 6
Your network contains an Active Directory domain named contoso.com. The network has an Active Directory Certificate Services (AD CS) infrastructure.
You need to issue a certificate to users to meet the following requirements:
Ensure that the users can encrypt files by using Encrypting File System (EFS).
Ensure that all of the users reenroll for their certificate every six months.
Solution: From the properties of the Basic EFS template, you assign the Allow - Enroll permission to the Authenticated Users group.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 7
You need to recommend a configuration for the CA extensions of Northwind Traders that meets the certificate revocation requirement of Customer1.
What should you recommend? To answer, select the appropriate prefix of the target location for the each extension settings in the answer area.

Answer:
Explanation: 
NEW QUESTION 8
In adatum.com, you install and configure a server that has the Active Directory Federation Services server role and all of the AD FS role services installed.
You need to recommend which AD FS configurations must be performed m adatum.com to meet the security requirements.
Which configurations should you recommend before creating a trust policy?
- A. Export the server authentication certificate and provide the certificate to Trey Researc
- B. Import the token-signing certificate from Trey Research.
- C. Export the server authentication certificate and provide the certificate to Trey Researc
- D. Import the server authentication certificate from Trey Research.
- E. Export the token-signing certificate and provide the certificate to Trey Researc
- F. Import the server authentication certificate from Trey Research.
- G. Export the token-signing certificate and provide the certificate to Trey Researc
- H. Import the token-signing certificate from Trey Research.
Answer: B
Explanation: 


NEW QUESTION 9
You need to recommend a solution that meets the notification requirements.
Which System Center 2012 components should you include in the recommendation?
- A. Service Manager, Orchestrator and App Controller
- B. Configuration Manager, Service Manager and Orchestrator
- C. App Controller, Configuration Manager and Operations Manager
- D. Operations Manager, Service Manager and Orchestrator
Answer: D
NEW QUESTION 10
Your company has 10,000 users located in 25 different sites.
All servers run Windows Server 2012. All client computers run either Windows 7 or Windows 8. You need to recommend a solution to provide self-service password reset for all of the users. What should you include in the recommendation?
- A. The Microsoft System Center 2012 Service Manager Self-Service Portal and Microsoft System Center 2012 Orchestrator runbooks
- B. Microsoft System Center 2012 Operations Manager management packs and Microsoft System Center2012 Configuration Manager collections
- C. The Microsoft System Center 2012 Service Manager Self-Service Portal and Microsoft System Center 2012 Operation Manager management packs
- D. Microsoft System Center 2012 App Controller and Microsoft System Center 2012 Orchestrator runbooks
Answer: A
NEW QUESTION 11
You need to collect the required security logs.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.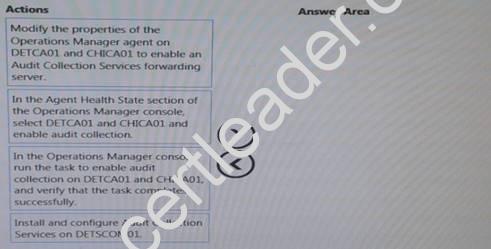
Answer:
Explanation: Note:
* Audit collection services (Box 1)
In System Center 2012 – Operations Manager, Audit Collection Services (ACS) provides a means to collect records generated by an audit policy and store them in a centralized database.
ACS requires the following components: ACS Forwarders, ACS Collector, ACS Database
* ACS Forwarders (box 2)
The service that runs on ACS forwarders is included in the Operations Manager agent. By default, this service is installed but not enabled when the Operations Manager agent is installed. You can enable this service for multiple agent computers at the same time using the Enable Audit Collection task.
* (box 3) Enable audit collection
After you install the ACS collector and database you can then remotely enable this service on multiple agents through the Operations Manager console by running the Enable Audit Collection task.
To enable audit collection on Operations Manager agents (see step 5 below)
Log on to the computer with an account that is a member of the Operations Manager Administrators role. This account must also have the rights of a local administrator on each agent computer that you want to enable as an ACS forwarder.
In the Operations console, click Monitoring.
In the navigation pane, expand Operations Manager, expand Agent Details, and then click Agent Health State. This view has two panes, and the actions in this procedure are performed in the right pane.
In the details pane, click all agents that you want to enable as ACS forwarders. You can make multiple selections by pressing CTRL or SHIFT.
In the Actions pane, under Health Service Tasks, click Enable Audit Collection to open the Run Task - Enable Audit Collection dialog box.
Etc.
NEW QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System Center 2012 infrastructure.
You deploy a service named Service1 by using a service template. Service1 contains two virtual machines. The virtual machines are configured as shown in the following table.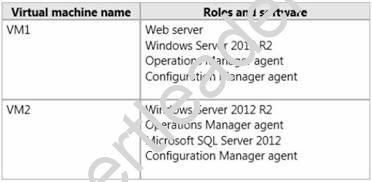
You need to recommend a monitoring solution to ensure that an administrator can review the availability information of Service1.
Solution: From Virtual Machine Manager (VMM), you modify the properties of the service template. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 13
Your network contains an Active Directory domain named contoso.com. The domain contains a System Center 2012 R2 Virtual Machine Manager (VMM) deployment.
The domain contains 20 Hyper-V hosts that run Windows Server 2012 R2. Currently, the computer accounts of all of the Hyper-V hosts are in organizational unit (OU) named Virtualization.
You plan to create two private clouds by using VMM named Cloud1 and Cloud2. The virtual machines for Cloud1 will be hosted on two Hyper-V hosts named Server1 and Server2. The virtual machines for Cloud2 will be hosted on two Hyper-V hosts named Server3 and Server4.
You need to recommend an administrative model for Cloud1 and Cloud2.
Which technology best achieves the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- A. Two sites and two Application Administrator (Self-Service User) user roles
- B. Two host groups and two Application Administrator (Self-Service User) user roles
- C. Two OUs and two Application Administrator (Self-Service User) user roles
- D. Two logical units and two Tenant Administrator user roles
Answer: B
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. You have a failover cluster named Cluster1 that contains two nodes named Server1 and Server2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
You plan to create two virtual machines that will run an application named App1. App1 will store data on a virtual hard drive named App1data.vhdx. App1data.vhdx will be shared by both virtual machines.
The network contains the following shared folders:
An SMB file share named Share1 that is hosted on a Scale-Out File Server.
An SMB file share named Share2 that is hosted on a standalone file server.
An NFS share named Share3 that is hosted on a standalone file server.
You need to ensure that both virtual machines can use App1data.vhdx simultaneously. What should you do? To answer, select the appropriate configurations in the answer area. Hot Area: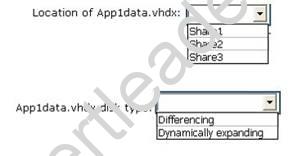
Answer:
Explanation: 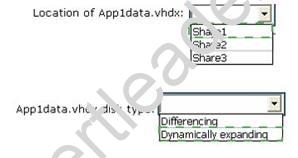
NEW QUESTION 15
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System Center 2012 infrastructure.
You deploy a service named Service1 by using a service template. Service1 contains two virtual machines. The virtual machines are configured as shown in the following table.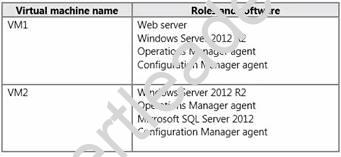
You need to recommend a monitoring solution to ensure that an administrator can review the availability information of Service1.
Solution: From Operations Manager, you create a Distributed Application and a Monitor Override.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 16
Your network contains a Hyper-V cluster named Cluster1.
You install Microsoft System Center 2012 Virtual Machine Manager (VMM). You create a user account for another administrator named User1.
You plan to provide User1 with the ability to manage only the virtual machines that User1 creates. You need to identify what must be created before you delegate the required permissions.
What should you identify?
- A. A service template
- B. A Delegated Administrator
- C. A cloud
- D. A host group
Answer: D
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. The domain contains a virtual machine named VM1. A developer wants to attach a debugger to VM1.
You need to ensure that the developer can connect to VM1 by using a named pipe. Which virtual machine setting should you configure?
- A. BIOS
- B. Network Adapter
- C. COM 1
- D. Processor
Answer: C
Explanation: Named pipes can be used to connect to a virtual machine by configuring COM 1. References:
http://support.microsoft.com/kb/819036 http://support.microsoft.com/kb/141709
Recommend!! Get the Full 70-414 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/70-414-exam-dumps.html (New 270 Q&As Version)