Certleader C2150-612 Questions are updated and all C2150-612 answers are verified by experts. Once you have completely prepared with our C2150-612 exam prep kits you will be ready for the real C2150-612 exam without a problem. We have Replace IBM C2150-612 dumps study guide. PASSED C2150-612 First attempt! Here What I Did.
NEW QUESTION 1
What are Mow sources used to monitor?
- A. Vulnerability information
- B. End point network activity
- C. Server performance metrics
- D. User account credential usage activity
Answer: C
NEW QUESTION 2
Which QRadar component provides Layer 7 visibility within a physical network infrastructure?
- A. QRadar Data Node
- B. QRadar Flow Analyzer
- C. QRadar Flow Collector
- D. QRadar VFlow Collector
Answer: D
NEW QUESTION 3
What are the two available formats for exporting event and flow data for external analysis? (Choose two.)
- A. XML
- B. DOC
- C. PDF
- D. CSV
- E. HTML
Answer: AD
NEW QUESTION 4
Which three data sources contribute to the creation an updates of assets? (Choose three.)
- A. Log sources
- B. Flow sources
- C. Reference set imports
- D. Vulnerability scanners
- E. QRadar log source auto-updates
- F. X-Force reference list integration
Answer: BEF
NEW QUESTION 5
What is the largest differentiator between a flow and event?
- A. Events occur at a moment in time while flows have a duration.
- B. Events can be forwarded to another destination, but flows cannot.
- C. Events allow for the creation of custom properties, but flows cannot.
- D. Flows only contribute to local correlated rules, while events are global.
Answer: A
NEW QUESTION 6
What is the purpose of coalescing?
- A. To reduce the number of events which count against EPS licenses
- B. To reduce the amount of data received by QRadar event collectors
- C. To reduce the amount of data going through the pipeline and stored onto disk
- D. To reduce the number of offenses generated by QRadar as part of the tun.ng process
Answer: A
NEW QUESTION 7
What is the key difference between Rules and Building Blocks in QRadar?
- A. Rules have Actions and Responses; Building Blocks do not.
- B. The Response Limiter is available on Building Blocks but not on Rules.
- C. Building Blocks are built-in to the product; Rules are customized for each deployment.
- D. Building Blocks are Rules which are evaluated on both Flows and Events; Rules are evaluated on Offenses of Flows or Events.
Answer: A
NEW QUESTION 8
Which three optional items can be added to the Default and Custom Dashboards without requiring additional licensing? (Choose three.)
- A. Offenses
- B. Log Activity
- C. Risk Change
- D. Flow Search
- E. Risk Monitoring
- F. Asset Management
Answer: ACE
NEW QUESTION 9
Which saved searches can be included on the Dashboard?
- A. Event and Flow saved searches
- B. Asset and Network saved searches
- C. User and Vulnerability saved searches
- D. Network Activity and Risk saved searches
Answer: A
NEW QUESTION 10
What ability does marking a custom property as "optimized" provide?
- A. Allows you to use the custom property in a rule test
- B. Allows you to process events above your license rating
- C. Allows offenses to merge both events & flows into the same offense
- D. Allows for offenses, events & flows to be compared directly in real time
Answer: D
NEW QUESTION 11
Given these default options for dashboards on the QRadar Dashboard Tab: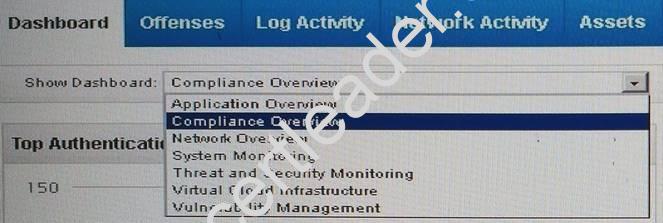
Which will display a list of offenses?
- A. Network Overview
- B. System Monitoring
- C. Vulnerability Management
- D. Threat and Security Monitoring
Answer: D
NEW QUESTION 12
Which QRadar component provides the user interface that delivers real-time flow views?
- A. QRadar Viewer
- B. QRadar Console
- C. QRadar Flow Collector
- D. QRadar Flow Processor
Answer: B
Explanation:
References:
http://www.ibm.com/support/knowledgecenter/en/SS42VS_7.2.7/com.ibm.qradar.doc/shc_qradar_comps.html
NEW QUESTION 13
Which type of rule requires a saved search that must be grouped around a common parameter
- A. Flow Rule
- B. Event Rule
- C. Common Rule
- D. Anomaly Rule
Answer: B
NEW QUESTION 14
Which list is only Rule Actions?
- A. Modify Credibility; Send SNMP trap; Drop the Detected Event; Dispatch New Event.
- B. Modify Credibility; Annotate Event; Send to Forwarding Destinations; Dispatch New Event.
- C. Modify Severity; Annotate Event; Drop the Detected Event; Ensure the detected event is part of an offense.
- D. Modify Severity; Send to Forwarding Destinations; Drop the Detected Event; Ensure the detected event is part of an offense.
Answer: A
Explanation:
References:
http://www.ibm.com/support/knowledgecenter/SSKMKU/com.ibm.qradar.doc/t_qradar_create_cust_rul.html
NEW QUESTION 15
Where could you get additional details on why the offense was triggered when Summary page?
- A. Display > Notes
- B. Display > Rules
- C. Display > Flows
- D. Display > Events
Answer: B
NEW QUESTION 16
In a distribution QReader deployment with multiple Event Collectors, from where can syslog and JDBC log sources collected?
- A. Syslog log sources and JDBC log sources may be collected by any Event Collector.
- B. One Event Collector must collect ALL syslog events and another Event Collector must collect All JDBC events.
- C. Syslog log sources and JDBC log sources are always collected by the collector assigned in the log source definition.
- D. Syslog log sources may be collected by any Event Collector, but JDBC log sources will always be collected by collector assigned in the log source definition.
Answer: C
NEW QUESTION 17
Which three options are available on the New Search on the My Offenses and All Offenses pages (Choose three.)
- A. Notes
- B. Source IP
- C. Magnitude
- D. Attack Name
- E. Malware Name
- F. Specific Interval
Answer: BDF
NEW QUESTION 18
A mapping of a username to a user’s manager can be stored in a Reference Table and output in a search or a report.
Which mechanism could be used to do this?
- A. Quick Search filters can select users based on their manager’s name.
- B. Reference Table lookup values can be accessed in an advanced search.
- C. Reference Table lookup values can be accessed as custom event properties.
- D. Reference Table lookup values are automatically used whenever a saved search is run.
Answer: B
NEW QUESTION 19
What is the definition of asset profile on QRadar?
- A. It is any network endpoint that sends or receives data across a network infrastructure.
- B. It is all the information that IBM Security QRadar SIEM collected over time about a specific asset.
- C. It is the information servers and hosts in a network provide to assist users when resolving security issues.
- D. It is an application used to configure and distribute settings to devices and computers in an organization, school, or business.
Answer: B
NEW QUESTION 20
What does the Network Hierachy provide relating to the "whole picture" that is helpful durin an investigation?
- A. It allows hosts that are marked to be known to have vulnerabilities to be seen quickly.
- B. It allows for the isolation of traffic between the hosts in question for more in depth analysis.
- C. It allows for the removal of infected hosts from the network before being added back into the network.
- D. It allows for the identification of known hosts on the network versus those that aren't members of the network.
Answer: D
NEW QUESTION 21
Which three could the considered a log source type? (Choose three.)
- A. Red Hat Network
- B. IBM ISS Proventia
- C. QRadar Event Processor
- D. Check Point Firewall-1
- E. Sourcefire Flow Injector
- F. McAfee ePolicy Orchestrator
Answer: BDF
Explanation:
https://www.ibm.com/support/knowledgecenter/SS42VS_DSM/c_LogSourceGuide_ExtDocs_typeIDs.html
NEW QUESTION 22
When reviewing Network Activity, a flow shows a communication between a local server on port 443, and a random, remote port. The bytes from the local destination host are 2 GB, and the bytes from the remote, source host address are 40KB.
What is the flow bias of this session?
- A. Other
- B. Mostly in
- C. Near-same
- D. Mostly out
Answer: D
NEW QUESTION 23
Which Anomaly Detection Rule type can test events or flows for volume changes that occur in regular patterns to detect outliers?
- A. Outlier Rule
- B. Anomaly Rule
- C. Threshold Rule
- D. Behavioral Rule
Answer: D
Explanation:
References:
http://www.ibm.com/support/knowledgecenter/en/SS42VS_7.2.7/com.ibm.qradar.doc/c_qradar_rul_anomaly_de
NEW QUESTION 24
Which capability is common to both Rules and Building Blocks?
- A. Rules and Building Blocks both set the Magnitude of an Event.
- B. Rules and Building blocks both have the same selection of tests.
- C. Rules and Building Blocks can both be Enabled/Disabled through the GUI.
- D. Rules and Building Blocks both have Actions; Building Blocks do not have Responses.
Answer: D
NEW QUESTION 25
An event is happening regularly and frequently; each event indicates the same target username. There is a rule configured to test for this event which has a rule action to create an offense indexed on the username.
What will QRadar do with the triggered rule assuming no offenses exist for the username and no offenses are closed during this time?
- A. Each matching event will be tagged with the Rule name, but only one Offense will be created.
- B. Each matching event will cause a new Offense to be created and will be tagged with the Rule name.
- C. Events will be tagged with the rule name as long as the Rule Response limiter is satisfie
- D. Only one offense will be created.
- E. Each matching event will be tagged with the Rule name, and an Offense will be created if the event magnitude is greater than 6.
Answer: C
NEW QUESTION 26
......
100% Valid and Newest Version C2150-612 Questions & Answers shared by Dumpscollection, Get Full Dumps HERE: http://www.dumpscollection.net/dumps/C2150-612/ (New 106 Q&As)