Exam Code: CS0-001 (CS0-001 Dumps), Exam Name: CompTIA CSA+ Certification Exam, Certification Provider: CompTIA Certifitcation, Free Today! Guaranteed Training- Pass CS0-001 Exam.
CompTIA CS0-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A company has received the results of an external vulnerability scan from its approved scanning vendor. The company is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within the time frame?
- A. Service level agreement
- B. Regulatory compliance
- C. Memorandum of understanding
- D. Organizational governance
Answer: A
NEW QUESTION 2
An organization uses Common Vulnerability Scoring System (CVSS) scores to prioritize remediation of vulnerabilities.
Management wants to modify the priorities based on a difficulty factor so that vulnerabilities with lower CVSS scores may get a higher priority if they are easier to implement with less risk to system functionality. Management also wants to quantify the priority. Which of the following would achieve management’s objective?
- A. (CVSS Score) * Difficulty = PriorityWhere Difficulty is a range from 0.1 to 1.0 with 1.0 being easiest and lowest risk to implement
- B. (CVSS Score) * Difficulty = PriorityWhere Difficulty is a range from 1 to 5 with 1 being easiest and lowest risk to implement
- C. (CVSS Score) / Difficulty = PriorityWhere Difficulty is a range from 1 to 10 with 10 being easiest and lowest risk to implement
- D. ((CVSS Score) * 2) / Difficulty = PriorityWhere CVSS Score is weighted and Difficulty is a range from 1 to 5 with 5 being easiest and lowest risk to implement
Answer: C
NEW QUESTION 3
A security analyst with an international response team is working to isolate a worldwide distribution of ransomware. The analyst is working with international governing bodies to distribute advanced intrusion detection routines for this variant of ransomware. Which of the following is the MOST important step with
which the security analyst should comply?
- A. Security operations privacy law
- B. Export restrictions
- C. Non-disclosure agreements
- D. Incident response forms
Answer: D
NEW QUESTION 4
A security administrator uses FTK to take an image of a hard drive that is under investigation. Which of the following processes are used to ensure the image is the same as the original disk? (Choose two.)
- A. Validate the folder and file directory listings on both.
- B. Check the hash value between the image and the original.
- C. Boot up the image and the original systems to compare.
- D. Connect a write blocker to the imaging device.
- E. Copy the data to a disk of the same size and manufacturer.
Answer: BC
NEW QUESTION 5
A company decides to move three of its business applications to different outsourced cloud providers. After moving the applications, the users report the applications time out too quickly and too much time is spent logging back into the different web-based applications throughout the day. Which of the following should a security architect recommend to improve the end-user experience without lowering the security posture?
- A. Configure directory services with a federation provider to manage accounts.
- B. Create a group policy to extend the default system lockout period.
- C. Configure a web browser to cache the user credentials.
- D. Configure user accounts for self-service account management.
Answer: B
NEW QUESTION 6
Joe, an analyst, has received notice that a vendor who is coming in for a presentation will require access to a server outside the network. Currently, users are only able to access remote sites through a VPN connection.
Which of the following should Joe use to BEST accommodate the vendor?
- A. Allow incoming IPSec traffic into the vendor’s IP address.
- B. Set up a VPN account for the vendor, allowing access to the remote site.
- C. Turn off the firewall while the vendor is in the office, allowing access to the remote site.
- D. Write a firewall rule to allow the vendor to have access to the remote site.
Answer: B
NEW QUESTION 7
A company has several internal-only, web-based applications on the internal network. Remote employees are allowed to connect to the internal corporate network with a company-supplied VPN client. During a project to upgrade the internal application, contractors were hired to work on a database server and were given copies of the VPN client so they could work remotely. A week later, a security analyst discovered an internal web-server had been compromised by malware that originated from one of the contractor’s laptops. Which of the following changes should be made to BEST counter the threat presented in this scenario?
- A. Create a restricted network segment for contractors, and set up a jump box for the contractors to use to access internal resources.
- B. Deploy a web application firewall in the DMZ to stop Internet-based attacks on the web server.
- C. Deploy an application layer firewall with network access control lists at the perimeter, and then create alerts for suspicious Layer 7 traffic.
- D. Require the contractors to bring their laptops on site when accessing the internal network instead of using the VPN from a remote location.
- E. Implement NAC to check for updated anti-malware signatures and location-based rules for PCs connecting to the internal network.
Answer: E
NEW QUESTION 8
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration
tester has received the following output from the latest scan: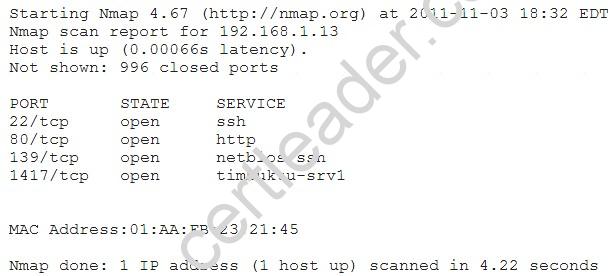
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
- A. nmap –sV 192.168.1.13 –p1417
- B. nmap –sS 192.168.1.13 –p1417
- C. sudo nmap –sS 192.168.1.13
- D. nmap 192.168.1.13 –v
Answer: A
NEW QUESTION 9
A start member reported that a laptop has (traded performance. The security analyst has investigated the issue and discovered that CPU utilization, memory utilization. and outbound network traffic are consuming the laptop resources. Which of the following is the BEST course of action to resolve the problem?
- A. Identity and remove malicious processes.
- B. Disable scheduled tasks
- C. Suspend virus scan
- D. Increase laptop memory.
- E. Ensure the laptop OS is property patched
Answer: A
NEW QUESTION 10
Which of the following describes why it is important to include scope within the rules of engagement of a
penetration test?
- A. To ensure the network segment being tested has been properly secured
- B. To ensure servers are not impacted and service is not degraded
- C. To ensure all systems being scanned are owned by the company
- D. To ensure sensitive hosts are not scanned
Answer: C
NEW QUESTION 11
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the web proxy generated an alert regarding the same indicator. The threat intelligence analyst states that related sites were not visited but were searched for in a search engine. Which of the following MOST likely happened in this situation?
- A. The analyst is not using the standard approved browser.
- B. The analyst accidently clicked a link related to the indicator.
- C. The analyst has prefetch enabled on the browser in use.
- D. The alert in unrelated to the analyst’s search.
Answer: C
NEW QUESTION 12
A cybersecurity consultant found common vulnerabilities across the Mowing, services used by multiple severs at an organization: VPN. SSH, and Ml I PS. Which of the following is the MOST likely reason for the discovered vulnerabilities?
- A. Leaked PKI private key
- B. Vulnerable version of OpenSSL
- C. Common initialization vector
- D. Weak level of encryption entropy
- E. Vulnerable implementation of PEAP
Answer: D
NEW QUESTION 13
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The security analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reactions, server functionality does not seem to be affected, and no malware was found after a scan.
Which of the following actions should the analyst take?
- A. Reschedule the automated patching to occur during business hours.
- B. Monitor the web application service for abnormal bandwidth consumption.
- C. Create an incident ticket for anomalous activity.
- D. Monitor the web application for service interruptions caused from the patching.
Answer: C
NEW QUESTION 14
A logistics company’s vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ: SQL injection on an infrequently used web server that provides files to vendors
SQL injection on an infrequently used web server that provides files to vendors  SSL/TLS not used for a website that contains promotional information
SSL/TLS not used for a website that contains promotional information
The scan also shows the following vulnerabilities on internal resources: Microsoft Office Remote Code Execution on test server for a human resources system
Microsoft Office Remote Code Execution on test server for a human resources system  TLS downgrade vulnerability on a server in a development network
TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?
- A. Microsoft Office Remote Code Execution
- B. SQL injection
- C. SSL/TLS not used
- D. TLS downgrade
Answer: A
NEW QUESTION 15
A security analyst is reviewing IDS logs and notices the following entry: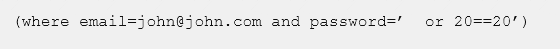
Which of the following attacks is occurring?
- A. Cross-site scripting
- B. Header manipulation
- C. SQL injection
- D. XML injection
Answer: C
NEW QUESTION 16
A company has decided to process credit card transactions directly. Which of the following would meet the requirements for scanning this type of data?
- A. Quarterly
- B. Yearly
- C. Bi-annually
- D. Monthly
Answer: A
NEW QUESTION 17
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?
- A. Wireshark
- B. Qualys
- C. netstat
- D. nmap
- E. ping
Answer: D
NEW QUESTION 18
Oven the following log snippet:
Which of the following describes the events that have occurred?
- A. An attempt to make an SSH connection from 'superman' was done using a password.
- B. An attempt to make an SSH connection from 192 168 1 166 was done using PKI.
- C. An attempt to make an SSH connection from outside the network was done using PKI.
- D. An attempt to make an SSH connection from an unknown IP address was done using a password.
Answer: B
P.S. DumpSolutions now are offering 100% pass ensure CS0-001 dumps! All CS0-001 exam questions have been updated with correct answers: https://www.dumpsolutions.com/CS0-001-dumps/ (242 New Questions)