We provide CS0-001 Free Practice Questions in two formats. Download PDF & Practice Tests. Pass CompTIA CS0-001 Exam quickly & easily. The CS0-001 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CS0-001 Dumps Questions product and material, you can easily pass the CS0-001 exam.
Check CS0-001 free dumps before getting the full version:
NEW QUESTION 1
Creating an isolated environment in order to test and observe the behavior of unknown software is also known as:
- A. sniffing.
- B. hardening.
- C. hashing
- D. sandboxing
Answer: D
NEW QUESTION 2
A company invested ten percent of its entire annual budget in security technologies. The Chief Information Officer (CIO) is convinced that, without this investment, the company will risk being the next victim of the same cyber-attack its competitor experienced three months ago. However, despite this investment, users are sharing their usernames and passwords with their coworkers to get their jobs done. Which of the following will eliminate the risk introduced by this practice?
- A. Invest in and implement a solution to ensure non-repudiation
- B. Force a daily password change
- C. Send an email asking users not to share their credentials
- D. Run a report on all users sharing their credentials and alert their managers of further actions
Answer: C
NEW QUESTION 3
A company has been a victim of multiple volumetric DoS attacks. Packet analysis of the offending traffic shows the following: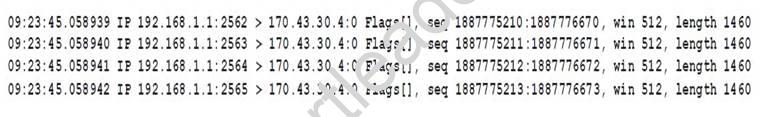
Which of the following mitigation techniques is MOST effective against the above attack?
- A. The company should contact the upstream ISP and ask that RFC1918 traffic be dropped.
- B. The company should implement a network-based sinkhole to drop all traffic coming from 192.168.1.1 at their gateway router.
- C. The company should implement the following ACL at their gateway firewall:DENY IP HOST 192.168.1.1 170.43.30.0/24.
- D. The company should enable the DoS resource starvation protection feature of the gateway NIPS.
Answer: A
Explanation: Topic 3, Exam Set C
NEW QUESTION 4
Datacenter access is controlled with proximity badges that record all entries and exits from the datacenter.
The access records are used to identify which staff members accessed the data center in the event of equipment theft.
Which of the following MUST be prevented in order for this policy to be effective?
- A. Password reuse
- B. Phishing
- C. Social engineering
- D. Tailgating
Answer: D
NEW QUESTION 5
Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. Servers 1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process which hosts this malware.
Instructions:
If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.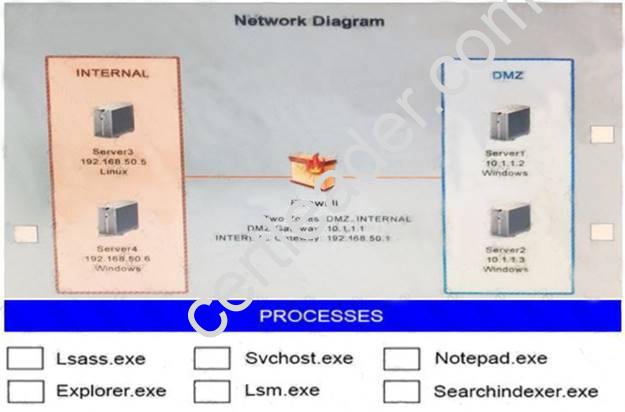
Answer:
Explanation: 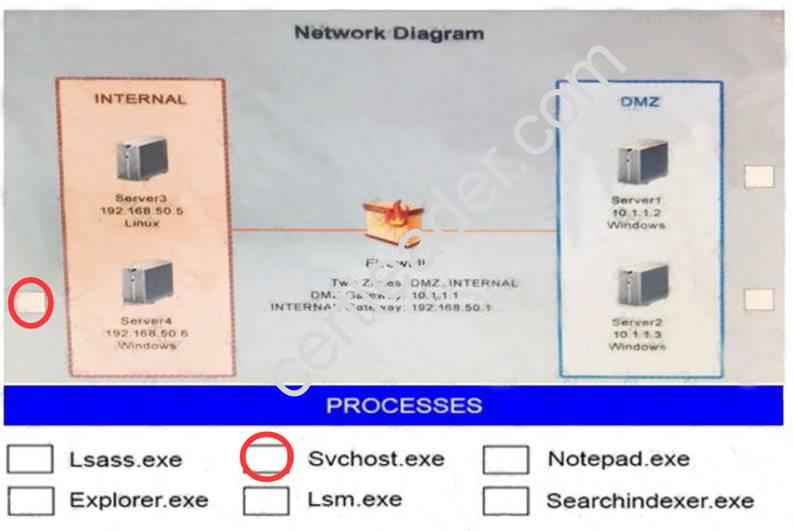
NEW QUESTION 6
A web application has a newly discovered vulnerability in the authentication method used to validate known company users. The user ID of Admin with a password of “password” grants elevated access to the application over the Internet. Which of the following is the BEST method to discover the vulnerability before a production deployment?
- A. Manual peer review
- B. User acceptance testing
- C. Input validation
- D. Stress test the application
Answer: C
NEW QUESTION 7
A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded. Which of the following should the security analyst recommend to add additional security to this device?
- A. The security analyst should recommend this device be place behind a WAF.
- B. The security analyst should recommend an IDS be placed on the network segment.
- C. The security analyst should recommend this device regularly export the web logs to a SIEM system.
- D. The security analyst should recommend this device be included in regular vulnerability scans.
Answer: A
NEW QUESTION 8
A systems administrator is trying to secure a critical system. The administrator has placed the system behind a firewall, enabled strong authentication, and required all administrators of this system to attend mandatory training.
Which of the following BEST describes the control being implemented?
- A. Audit remediation
- B. Defense in depth
- C. Access control
- D. Multifactor authentication
Answer: B
NEW QUESTION 9
A security analyst wants to scan the network for active hosts. Which of the following host characteristics help to differentiate between a virtual and physical host?
- A. Reserved MACs
- B. Host IPs
- C. DNS routing tables
- D. Gateway settings
Answer: A
NEW QUESTION 10
A new zero day vulnerability was discovered within a basic screen capture app, which is used throughout the environment Two days after discovering the vulnerability, the manufacturer of the software has not announced a remediation or it there will be a fix for this newly discovered vulnerability. The vulnerable application is not uniquely critical, but it is used occasionally by the management and executive management teams The vulnerability allows remote code execution to gam privileged access to the system Which of the following is the BEST course of action to mitigate this threat'
- A. Work with the manufacturer to determine the tone frame for the fix.
- B. Block the vulnerable application traffic at the firewall and disable the application services on each computer.
- C. Remove the application and replace it with a similar non-vulnerable application.
- D. Communicate with the end users that the application should not be used until the manufacturer has reserved the vulnerability.
Answer: D
NEW QUESTION 11
A production web server is experiencing performance issues. Upon investigation, new unauthorized applications have been installed and suspicious traffic was sent through an unused port. Endpoint security is not detecting any malware or virus. Which of the following types of threats would this MOST likely be classified as?
- A. Advanced persistent threat
- B. Buffer overflow vulnerability
- C. Zero day
- D. Botnet
Answer: A
NEW QUESTION 12
Which of the following are essential components within the rules of engagement for a penetration test? (Select TWO).
- A. Schedule
- B. Authorization
- C. List of system administrators
- D. Payment terms
- E. Business justification
Answer: AB
NEW QUESTION 13
A security analyst has noticed an alert from the SIEM. A workstation is repeatedly trying to connect to port 445 of a file server on the production network. All of the attempts are made with invalid credentials. Which of the following describes what is occurring?
- A. Malware has infected the workstation and is beaconing out to the specific IP address of the file server.
- B. The file server is attempting to transfer malware to the workstation via SMB.
- C. An attacker has gained control of the workstation and is attempting to pivot to the file server by creating an SMB session.
- D. An attacker has gained control of the workstation and is port scanning the network.
Answer: C
NEW QUESTION 14
A common mobile device vulnerability has made unauthorized modifications to a device. The device owner removes the vendor/carrier provided limitations on the mobile device. This is also known as:
- A. jailbreaking.
- B. cracking.
- C. hashing.
- D. fuzzing.
Answer: A
NEW QUESTION 15
Creating a lessons learned report following an incident will help an analyst to communicate which of the following information? (Select TWO)
- A. Root cause analysis of the incident and the impact it had on the organization
- B. Outline of the detailed reverse engineering steps for management to review
- C. Performance data from the impacted servers and endpoints to report to management
- D. Enhancements to the policies and practices that will improve business responses
- E. List of IP addresses, applications, and assets
Answer: AD
NEW QUESTION 16
A security administrator determines several months after the first instance that a local privileged user has been routinely logging into a server interactively as “root” and browsing the Internet. The administrator determines this by performing an annual review of the security logs on that server. For which of the following security architecture areas should the administrator recommend review and modification? (Select TWO).
- A. Log aggregation and analysis
- B. Software assurance
- C. Encryption
- D. Acceptable use policies
- E. Password complexity
- F. Network isolation and separation
Answer: AD
NEW QUESTION 17
An analyst was testing the latest version of an internally developed CRM system. The analyst created a basic user account. Using a few tools in Kali’s latest distribution, the analyst was able to access configuration files, change permissions on folders and groups, and delete and create new system objects. Which of the following techniques did the analyst use to perform these unauthorized activities?
- A. Impersonation
- B. Privilege escalation
- C. Directory traversal
- D. Input injection
Answer: C
NEW QUESTION 18
Following a data compromise, a cybersecurity analyst noticed the following executed query: SELECT * from Users WHERE name = rick OR 1=1
Which of the following attacks occurred, and which of the following technical security controls would BEST reduce the risk of future impact from this attack? (Select TWO).
- A. Cookie encryption
- B. XSS attack
- C. Parameter validation
- D. Character blacklist
- E. Malicious code execution
- F. SQL injection
Answer: CF
Explanation: Reference https://lwn.net/Articles/177037/
100% Valid and Newest Version CS0-001 Questions & Answers shared by DumpSolutions, Get Full Dumps HERE: https://www.dumpsolutions.com/CS0-001-dumps/ (New 242 Q&As)