We provide real CS0-002 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA CS0-002 Exam quickly & easily. The CS0-002 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA CS0-002 dumps pdf and vce product and material, you can easily pass the CS0-002 exam.
Online CompTIA CS0-002 free dumps demo Below:
NEW QUESTION 1
A human resources employee sends out a mass email to all employees that contains their personnel records. A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future.
Which of the following would be the BEST solution to recommend to the director?
- A. Install a data loss prevention system, and train human resources employees on its us
- B. Provide PII training to all employees at the compan
- C. Encrypt PII information.
- D. Enforce encryption on all emails sent within the compan
- E. Create a PII program and policy on how to handle dat
- F. Train all human resources employees.
- G. Train all employee
- H. Encrypt data sent on the company networ
- I. Bring in privacy personnel to present a plan on how PII should be handled.
- J. Install specific equipment to create a human resources policy that protects PII dat
- K. Train company employees on how to handle PII dat
- L. Outsource all PII to another compan
- M. Send the human resources director to training for PII handling.
Answer: A
NEW QUESTION 2
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
- A. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
- B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
- C. Development phases occurring at multiple sites may produce change management issues.
- D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
Answer: B
NEW QUESTION 3
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)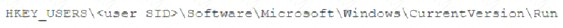
B)
C)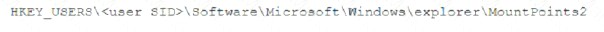
D)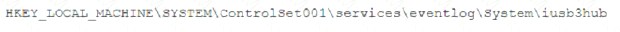
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
NEW QUESTION 4
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organization's financial assets.
Which of the following is the BEST example of the level of sophistication this threat actor is using?
- A. Social media accounts attributed to the threat actor
- B. Custom malware attributed to the threat actor from prior attacks
- C. Email addresses and phone numbers tied to the threat actor
- D. Network assets used in previous attacks attributed to the threat actor
- E. IP addresses used by the threat actor for command and control
Answer: D
NEW QUESTION 5
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
- A. Apply a firewall application server rule.
- B. Whitelist the application server.
- C. Sandbox the application server.
- D. Enable port security.
- E. Block the unauthorized networks.
Answer: B
NEW QUESTION 6
Ann, a user, reports to the security team that her browser began redirecting her to random sites while using her Windows laptop. Ann further reports that the OS shows the C: drive is out of space despite having plenty of space recently. Ann claims she not downloaded anything. The security team obtains the laptop and begins to investigate, noting the following: File access auditing is turned off.
File access auditing is turned off. When clearing up disk space to make the laptop functional, files that appear to be cached web pages are immediately created in a temporary directory, filling up the available drive space.
When clearing up disk space to make the laptop functional, files that appear to be cached web pages are immediately created in a temporary directory, filling up the available drive space. All processes running appear to be legitimate processes for this user and machine.
All processes running appear to be legitimate processes for this user and machine.  Network traffic spikes when the space is cleared on the laptop.
Network traffic spikes when the space is cleared on the laptop. No browser is open.
No browser is open.
Which of the following initial actions and tools would provide the BEST approach to determining what is happening?
- A. Delete the temporary files, run an Nmap scan, and utilize Burp Suite.
- B. Disable the network connection, check Sysinternals Process Explorer, and review netstat output.
- C. Perform a hard power down of the laptop, take a dd image, and analyze with FTK.
- D. Review logins to the laptop, search Windows Event Viewer, and review Wireshark captures.
Answer: B
NEW QUESTION 7
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the.
- A. email server that automatically deletes attached executables.
- B. IDS to match the malware sample.
- C. proxy to block all connections to <malwaresource>.
- D. firewall to block connection attempts to dynamic DNS hosts.
Answer: C
NEW QUESTION 8
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
- A. Create a security rule that blocks Internet access in the development VPC
- B. Place a jumpbox m between the developers' workstations and the development VPC
- C. Remove the administrator profile from the developer user group in identity and access management
- D. Create an alert that is triggered when a developer installs an application on a server
Answer: A
NEW QUESTION 9
A web developer wants to create a new web part within the company website that aggregates sales from individual team sites. A cybersecurity analyst wants to ensure security measurements are implemented during this process. Which of the following remediation actions should the analyst take to implement a vulnerability management process?
- A. Personnel training
- B. Vulnerability scan
- C. Change management
- D. Sandboxing
Answer: C
NEW QUESTION 10
While analyzing logs from a WAF, a cybersecurity analyst finds the following: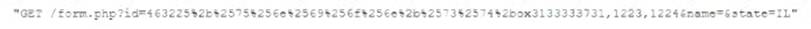
Which of the following BEST describes what the analyst has found?
- A. This is an encrypted GET HTTP request
- B. A packet is being used to bypass the WAF
- C. This is an encrypted packet
- D. This is an encoded WAF bypass
Answer: D
NEW QUESTION 11
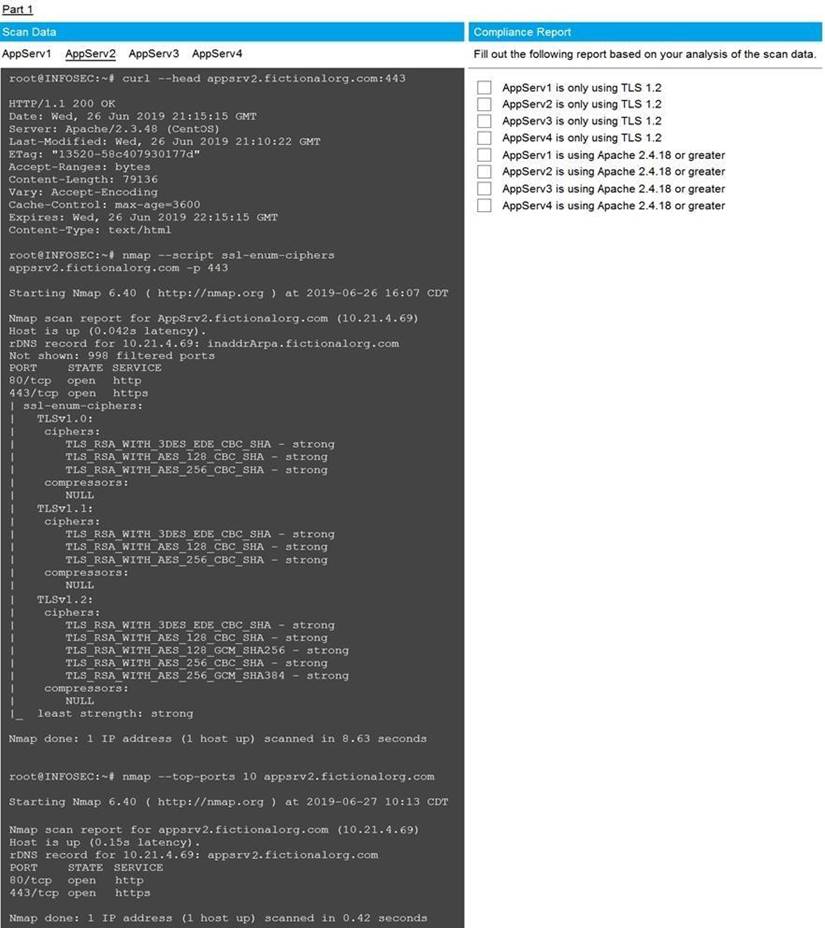
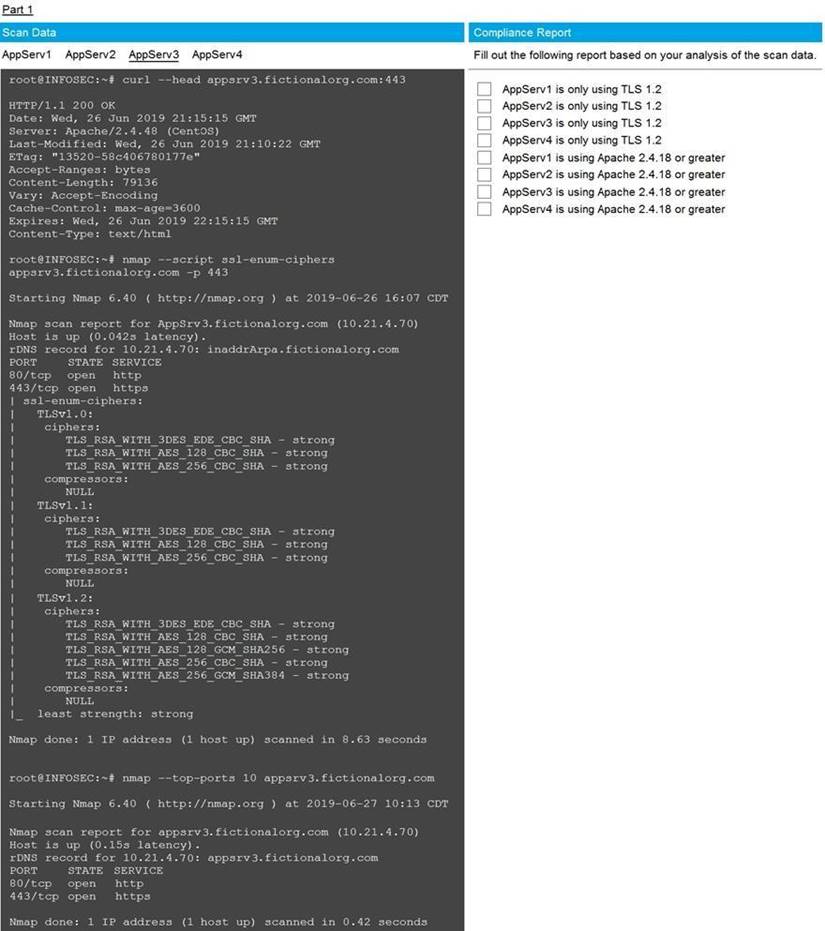
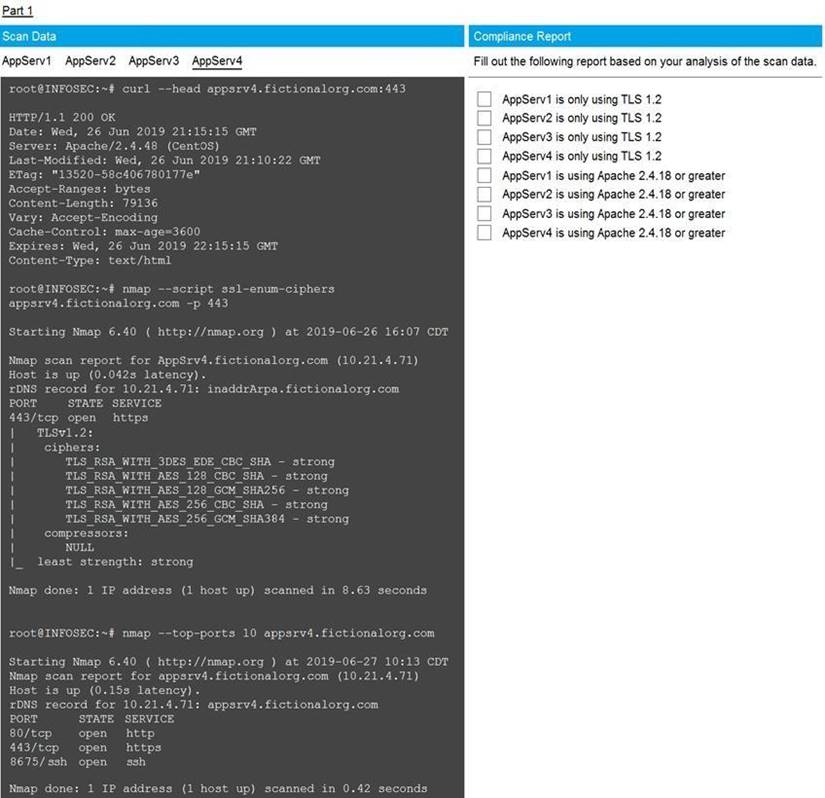
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
• TLS 1.2 is the only version of TLS running.
• Apache 2.4.18 or greater should be used.
• Only default ports should be used. INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.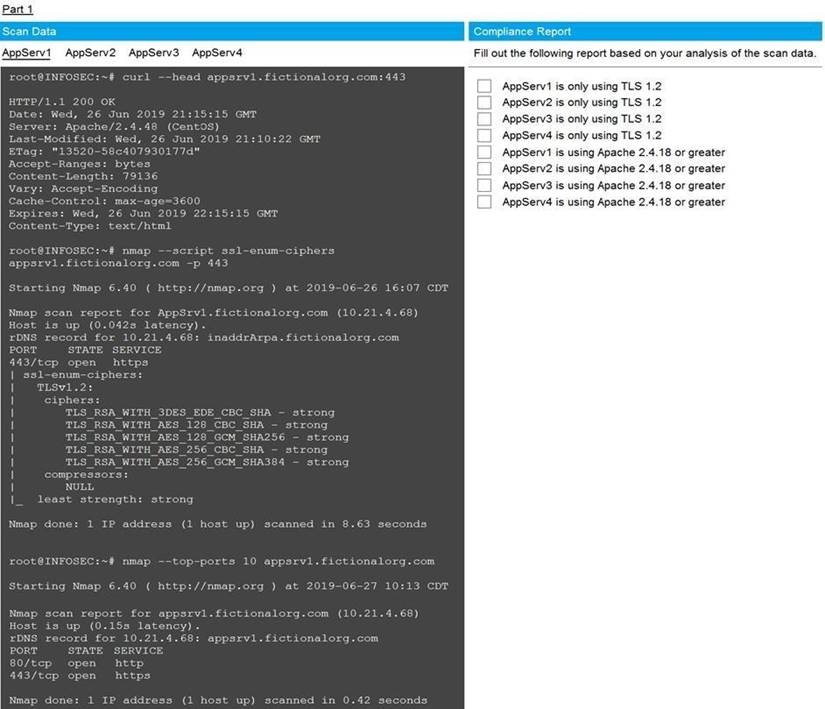
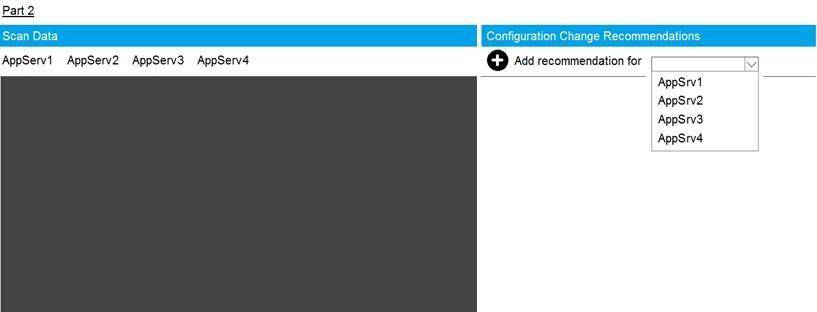
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Part 1 Answer
Check on the following:
AppServ1 is only using TLS.1.2
AppServ4 is only using TLS.1.2
AppServ1 is using Apache 2.4.18 or greater
AppServ3 is using Apache 2.4.18 or greater
AppServ4 is using Apache 2.4.18 or greater
Part 2 Answer
Recommendation:
Recommendation is to disable TLS v1.1 on AppServ2 and AppServ3. Also upgrade AppServ2 Apache to version 2.4.48 from its current version of 2.3.48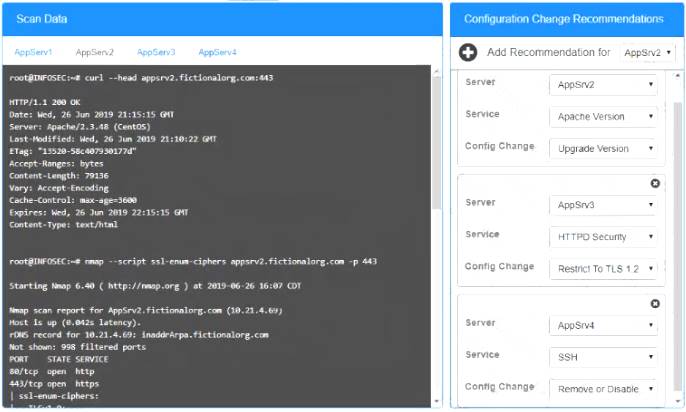
NEW QUESTION 12
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC.
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
- A. Gather information from providers, including datacenter specifications and copies of audit reports.
- B. Identify SLA requirements for monitoring and logging.
- C. Consult with senior management for recommendations.
- D. Perform a proof of concept to identify possible solutions.
Answer: B
NEW QUESTION 13
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
- A. The use of infrastructure-as-code capabilities leads to an increased attack surface.
- B. Patching the underlying application server becomes the responsibility of the client.
- C. The application is unable to use encryption at the database level.
- D. Insecure application programming interfaces can lead to data compromise.
Answer: D
NEW QUESTION 14
A security analyst has discovered suspicious traffic and determined a host is connecting to a known malicious website. The MOST appropriate action for the analyst to take would be lo implement a change request to:
- A. update the antivirus software
- B. configure the firewall to block traffic to the domain
- C. add the domain to the blacklist
- D. create an IPS signature for the domain
Answer: B
NEW QUESTION 15
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integration intelligence into hunt operations?
- A. It enables the team to prioritize the focus area and tactics within the company’s environment.
- B. It provide critically analyses for key enterprise servers and services.
- C. It allow analysis to receive updates on newly discovered software vulnerabilities.
- D. It supports rapid response and recovery during and followed an incident.
Answer: A
NEW QUESTION 16
A security analyst is investigating a compromised Linux server. The analyst issues the ps command and receives the following output.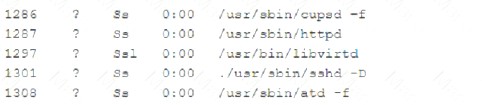
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
- A. strace /proc/1301
- B. rpm -V openash-server
- C. /bin/la -1 /proc/1301/exe
- D. kill -9 1301
Answer: A
NEW QUESTION 17
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful authentication, the user is then redirected back to the original page. Some users have reported receiving phishing emails with a link that takes them to the application login page but then redirects to a fake login page after successful authentication.
Which of the following will remediate this software vulnerability?
- A. Enforce unique session IDs for the application.
- B. Deploy a WAF in front of the web application.
- C. Check for and enforce the proper domain for the redirect.
- D. Use a parameterized query to check the credentials.
- E. Implement email filtering with anti-phishing protection.
Answer: D
NEW QUESTION 18
......
Recommend!! Get the Full CS0-002 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/CS0-002/ (New 186 Q&As Version)