Ucertify offers free demo for PT0-001 exam. "CompTIA PenTest+ Certification Exam", also known as PT0-001 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA PT0-001 exam, will help you answer those questions. The PT0-001 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA PT0-001 exams and revised by experts!
Free demo questions for CompTIA PT0-001 Exam Dumps Below:
NEW QUESTION 1
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable The Client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
- A. SOW
- B. NDA
- C. EULA
- D. BRA
Answer: D
NEW QUESTION 2
Which of the following types of physical security attacks does a mantrap mitigate-?
- A. Lock picking
- B. Impersonation
- C. Shoulder surfing
- D. Tailgating
Answer: D
NEW QUESTION 3
DRAG DROP
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once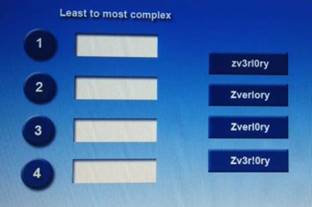
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Zverlory
Zverl0ry
zv3rlory
Zv3r!0ry
NEW QUESTION 4
A penetration tester is utilizing social media to gather information about employees at a company. The tester has created a list of popular words used in employee profile s. For which of the following types of attack would this information be used?
- A. Explogt chaining
- B. Session hijacking
- C. Dictionary
- D. Karma
Answer: B
NEW QUESTION 5
A penetration tester notices that the X-Frame-Optjons header on a web application is not set. Which of the following would a malicious actor do to explogt this configuration setting?
- A. Use path modification to escape the application's framework.
- B. Create a frame that overlays the application.
- C. Inject a malicious iframe containing JavaScript.
- D. Pass an iframe attribute that is maliciou
Answer: B
NEW QUESTION 6
Which of the following reasons does penetration tester needs to have a customer's point-of -contact information available at all time? (Select THREE).
- A. To report indicators of compromise
- B. To report findings that cannot be explogted
- C. To report critical findings
- D. To report the latest published explogts
- E. To update payment information
- F. To report a server that becomes unresponsive
- G. To update the statement o( work
- H. To report a cracked password
Answer: DEF
NEW QUESTION 7
A penetration testet is attempting to capture a handshake between a client and an access point by monitoring a WPA2-PSK secured wireless network The (ester is monitoring the correct channel tor the identified network but has been unsuccessful in capturing a handshake Given this scenario, which of the following attacks would BEST assist the tester in obtaining this handshake?
- A. Karma attack
- B. Deauthentication attack
- C. Fragmentation attack
- D. SSID broadcast flood
Answer: B
NEW QUESTION 8
Given the following Python script: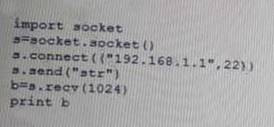
Which of the following actions will it perform?
- A. ARP spoofing
- B. Port scanner
- C. Reverse shell
- D. Banner grabbing
Answer: A
NEW QUESTION 9
Click the exhibit button.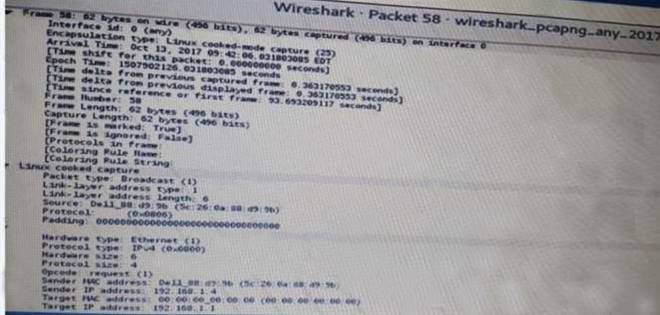
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network Which of the following types of attacks should the tester stop?
- A. SNMP brute forcing
- B. ARP spoofing
- C. DNS cache poisoning
- D. SMTP relay
Answer: B
NEW QUESTION 10
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before it can run a static code analyzer?
- A. Run the application through a dynamic code analyzer.
- B. Employ a fuzzing utility.
- C. Decompile the application.
- D. Check memory allocation
Answer: D
NEW QUESTION 11
A penetration tester successfully explogts a DM2 server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use few this purpose? (Select TWO)
- A. Tcpdump
- B. Nmap
- C. Wiresrtark
- D. SSH
- E. Netcat
- F. Cain and Abel
Answer: CD
NEW QUESTION 12
While prioritizing findings and recommendations for an executive summary, which of the following considerations would De MOST valuable to the client?
- A. Levels of difficulty to explogt identified vulnerabilities
- B. Time taken to accomplish each step
- C. Risk tolerance of the organization
- D. Availability of patches and remediations
Answer: C
NEW QUESTION 13
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
- A. Script kiddies
- B. APT actors
- C. Insider threats
- D. Hacktrvist groups
Answer: B
NEW QUESTION 14
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikazt. Which of the following registry changes would allow for credential caching in memory?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 15
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
- A. dsrm -users "DN=compony.com; OU=hq CN=usera"
- B. dsuser -name -account -limit 3
- C. dsquery uaer -inactive 3
- D. dsquery -o -rein -limit 21
Answer: B
NEW QUESTION 16
A recently concluded penetration test revealed that a legacy web application is vulnerable lo SQL injection Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not m a position to risk the availability of the application Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Select TWO).
- A. Identify and eliminate inline SQL statements from the code.
- B. Identify and eliminate dynamic SQL from stored procedures.
- C. Identify and sanitize all user inputs.
- D. Use a whitelist approach for SQL statements.
- E. Use a blacklist approach for SQL statements.
- F. Identify the source of malicious input and block the IP addres
Answer: DE
NEW QUESTION 17
A. penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 18
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for the penetration tester to take?
- A. Obtain staff information by calling the company and using social engineering techniques.
- B. Visit the client and use impersonation to obtain information from staff.
- C. Send spoofed emails to staff to see if staff will respond with sensitive information.
- D. Search the Internet for information on staff such as social networking site
Answer: C
NEW QUESTION 19
Which of Ihe following commands would allow a penetration tester to access a private network from the Internet in Metasplogt?
- A. set rhost 192.168.1.10
- B. run autoroute -a 192.168.1.0/24
- C. db_nm«p -iL /tmp/privatehoots . txt
- D. use auxiliary/servet/aocka^a
Answer: D
NEW QUESTION 20
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
- A. Badge cloning
- B. Lock picking
- C. Tailgating
- D. Piggybacking
Answer: A
NEW QUESTION 21
A penetration tester runs the following from a compromised box 'python -c -import pty;Pty.sPawn( "/bin/bash").' Which of the following actions is the tester taking?
- A. Removing the Bash history
- B. Upgrading the shell
- C. Creating a sandbox
- D. Capturing credentials
Answer: A
NEW QUESTION 22
......
Recommend!! Get the Full PT0-001 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/PT0-001/ (New 145 Q&As Version)