Act now and download your CompTIA CV0-002 test today! Do not waste time for the worthless CompTIA CV0-002 tutorials. Download Regenerate CompTIA CompTIA Cloud+ Exam exam with real questions and answers and begin to learn CompTIA CV0-002 with a classic professional.
Also have CV0-002 free dumps questions for you:
NEW QUESTION 1
A company upgraded a hosted vulnerability scanner to the latest version, and now tickets are not
being created to assign critical vulnerabilities. After confirming the ticketing issue, all the scanning services are confirmed to be running on the VM. Which of the following is the MOST likely cause and best method to fix the issue?
- A. There was an IP change to the V
- B. Make changes to the server properties.
- C. The upgrade has a bug Reboot the server and attempt the upgrade again.
- D. The vulnerability scanner is on a different subne
- E. Open the ports, and it will reconnect.
- F. There is an application compatibility issu
- G. Roll back to the previous working backup.
Answer: D
NEW QUESTION 2
A company has an SLA of 15ms for storage latency.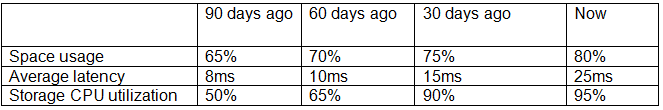
Given the above metrics, which of the following is the MOST appropriate change to the environment?
- A. Add computing nodes and data nodes on the storage side.
- B. Add more storage shelves to the current array.
- C. Enable compression on the storage side.
- D. Enable deduplication on the storage side.
Answer: C
NEW QUESTION 3
An e-commerce business recently experienced a two-hour outage from its hosted web service
provider. According to the SLA, the business needs to determine how much data can be restored. On which of the following service-level components should the business focus?
- A. MTTR
- B. RPO
- C. MTBF
- D. RTO
Answer: C
NEW QUESTION 4
An administrator is responsible for managing a private cloud that has servers that require a significant amount of RAM, but does not have the resources to dedicate to the guests. Which of the following features should the administrator configure on the hypervisor?
- A. Resource pooled memory
- B. Memory reservation
- C. Dynamic memory
- D. Static memory
Answer: B
NEW QUESTION 5
For budget purposes, the accounting department has asked an administrator to provide a disaster
recovery solution that will comply with the following requirements:
– Systems have to be operational within two days
– No disaster will be declared if the primary site is fully operational within 24 hours
Which of the following is the BEST solution the administrator can propose to the accounting department?
- A. Warm site
- B. Cold site
- C. Hot site
- D. Mirrored site
Answer: A
NEW QUESTION 6
Which of the following is often a difficult process when working with internationally-based cloud
providers?
- A. Litigation hold
- B. Data segregation
- C. Network isolation
- D. Multi-tenancy
Answer: A
NEW QUESTION 7
Tenants in a shared datacenter environment are concerned with the privacy of their data as it moves
from the application to the database servers in clear text. Which of the following can the provider implement to isolate tenants’ data?
- A. Bandwidth hard limits
- B. Reservations
- C. Resource pooling
- D. VLANs
Answer: D
NEW QUESTION 8
An administrator needs to monitor server applications in the company’s data center. Which of the
following tools would the administrator need to accomplish this objective?
- A. SMS
- B. SMTP
- C. IPMI
- D. SNMP
Answer: C
NEW QUESTION 9
Before doing a change on a VM, a systems administrator wants to ensure there is an easy and fast
way to rollback if needed. The change and testing should take approximately two hours. Which of the following is the EASIEST way to meet this requirement?
- A. Create a snapshot on the hypervisor.
- B. Make an on-demand, incremental backup to a VTL.
- C. Make an on-demand, full backup to a secondary location.
- D. Create a snapshot on a remote storage array.
Answer: A
NEW QUESTION 10
An administrator is tasked with encrypting all Personally Identifiable Information (PII) within a cloud- based database. Which of the following types of encryption will ensure that ONLY this type of information is encrypted while the rest of the database remains unencrypted?
- A. File and folder encryption
- B. Transport encryption
- C. Hard drive encryption
- D. Table encryption
Answer: D
NEW QUESTION 11
A cloud administrator is required to implement a solution to handle data-at-rest encryption requirements for a database. Which of the following would BEST satisfy the requirements?
- A. Install an SSL certificate and only allow secure connections to the server.
- B. Enable two-factor authentication on connections to the database server and log activities.
- C. Activate memory encryption on the virtual server and store the certificates remotely.
- D. Create a virtual encrypted disk, add it to the virtual server, and have the database write to it.
Answer: A
NEW QUESTION 12
Which of the following can be used to physically restrict employees from accessing a datacenter?
- A. Access badge
- B. Password
- C. Mantrap
- D. PIN
Answer: A
NEW QUESTION 13
Which of the following is a benefit of virtualization in a cloud environment?
- A. Decrease in the scalability of services
- B. Decrease in the time to implement certain services
- C. Decrease in the amount of resource pooling for services
- D. Increase in the time to service for certain services
Answer: B
NEW QUESTION 14
Which of the following describes connecting a physical Ethernet adapter to a virtual Ethernet adapter?
- A. Resource pooling
- B. Virtual switching
- C. Bridging
- D. Resource allocation
Answer: C
NEW QUESTION 15
In an IaaS model, to which of the following methodologies would the client apply a list of OS patches,
assuming approval from CAB has been given?
- A. Using a patch management system, identify the hypervisor type, select a group of hypervisors to be patched, and perform a rolling application of patches.
- B. Using a patch management system, identify the guests that require patching, and select and apply the patches.
- C. Using a patch management system, identify the applications needing the patch, select the required application in a patch management console, and apply the patches.
- D. Using a patch management system, identify the services that require patching, and select and apply the patches.
Answer: A
NEW QUESTION 16
A hosting company provides 10 VM web servers for a financial institution. The financial institution recently introduced a new web application and now their web traffic has significantly increased. Which of the following could the administrator implement to assist in reducing the load on the web servers?
- A. Clustering
- B. Virtual switching
- C. Load balancing
- D. Site mirroring
Answer: C
NEW QUESTION 17
The requirements for a web application state that it must be architected for high availability. The web application consists of front-end web server and back-end database server components respectively. Which of the following describes a solution that meets this requirement, while minimizing costs?
- A. One front-end web server and two clustered back-end database servers
- B. Two front-end web servers and two back-end database servers
- C. Two front-end web servers and one back-end database server
- D. Two load balanced front-end web servers and two clustered back-end database servers
Answer: D
NEW QUESTION 18
A number of VMs in a host are experiencing processor contention, showing down operations Which
of the following host hardware upgrade paths would yield higher VM performance, for the same VMs in the given hypervisor host?
- A. Replace CPUs to move from 32-bit architecture o 64-bit
- B. Replace CPUs to move from 64-bit architecture to 32-bit
- C. Replace CPUs to increase current core speed
- D. Replace CPUs to increase CPU core count
Answer: A
NEW QUESTION 19
The InfoSec team has directed compliance database activity monitoring without agents on a hosted
database server in the public IaaS. Which of the following configurations is needed to ensure this requirement is achieved?
- A. Configure the agent configuration file to log to the syslog server.
- B. Configure sniffing mode on database traffic.
- C. Implement built-in database tracking functionality.
- D. Implement database encryption and secure copy to the NAS.
Answer: B
NEW QUESTION 20
Which of the following network topologies should an administrator use to segment traffic?
- A. Metropolitan Area Networks
- B. Local Area Networks
- C. Virtual Local Area Networks
- D. Wide Area Networks
Answer: C
NEW QUESTION 21
A customer wants to schedule a backup job that compares and saves changes from the last full
backup. Which of the following backup types should be used?
- A. Differential
- B. Full
- C. Clone
- D. Incremental
Answer: A
Explanation:
Reference:
http://www.backup4all.com/kb/backup-types-115.html
NEW QUESTION 22
A university is running a DNA decoding project that will take seven years if it runs on its current
internal mainframe. The university negotiated a deal with a large cloud provider, which will donate its cloud resource to process the DNA decoding during the low peak time throughout the world. Which of the following is the MOST important resource the university should ask the cloud provider to donate?
- A. A large storage for the DNA decoding results
- B. A larger pipe to transfer the results
- C. A closer datacenter to the university
- D. Any available compute resource
Answer: C
NEW QUESTION 23
A cloud service administrator is consuming PaaS services and is performing baseline configuration
tests. Which of the following is part of the PaaS consumer’s responsibility with respect to the baseline confirmation tests?
- A. Application versions
- B. CPU utilization
- C. RAM utilization
- D. Operating system versions
Answer: B
NEW QUESTION 24
An administrator is deploying a new application platform with the following resource utilization: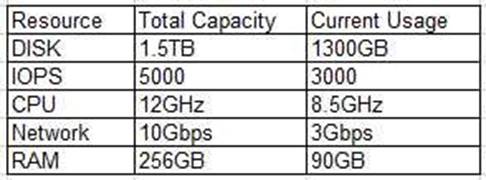
Company policy requires that no resource utilization surpasses 80%. Which of the following resources will need to be upgraded prior to deployment?
- A. Disk
- B. IOPS
- C. CPU
- D. Network
- E. RAM
Answer: A
NEW QUESTION 25
A company is interested in a DRP. The purpose of the plan is to recover business as soon as possible.
The MOST effective technique is:
- A. archiving.
- B. network clustering.
- C. site mirroring.
- D. active/active.
Answer: D
NEW QUESTION 26
A company purchased a SaaS CRM application. The signed SLA meets year-round performance
requirements. Three months after deployment, customers start reporting a slow application response time. System availability, connectivity, and proper functionality still meet the SL
- A. Which of the following is MOST likely the reason for the poor response time?
- B. Incorrect business requirements are invalidating the testing results.
- C. Bandwidth restrictions are causing poor performance.
- D. The application version is causing compatibility issues.
- E. Inadequate documentation is affecting the user interface.
Answer: C
NEW QUESTION 27
A cloud administrator is securing access to a VM using an IaaS cloud platform. The administrator
must perform this task using an automated method, allow administrators to perform any method and expose any property of the VM, deny access for everyone else, and allow only read-only access to everyone else. Given this scenario, which of the following should the administrator use to BEST meet these requirements?
- A. jQuery
- B. JavaScript
- C. Java
- D. JSON
Answer: C
NEW QUESTION 28
......
Thanks for reading the newest CV0-002 exam dumps! We recommend you to try the PREMIUM Exambible CV0-002 dumps in VCE and PDF here: https://www.exambible.com/CV0-002-exam/ (317 Q&As Dumps)