we provide High quality CompTIA SY0-601 free question which are the best for clearing SY0-601 test, and to get certified by CompTIA CompTIA Security+ Exam. The SY0-601 Questions & Answers covers all the knowledge points of the real SY0-601 exam. Crack your CompTIA SY0-601 Exam with latest dumps, guaranteed!
Also have SY0-601 free dumps questions for you:
NEW QUESTION 1
A recently discovered zero-day exploit utilizes an unknown vulnerability in the SMB network protocol to rapidly infect computers. Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
- A. Configure the perimeter firewall to deny inbound external connections to SMB ports.
- B. Ensure endpoint detection and response systems are alerting on suspicious SMB connections.
- C. Deny unauthenticated users access to shared network folders.
- D. Verify computers are set to install monthly operating system, updates automatically.
Answer: A
NEW QUESTION 2
Which of the following would be BEST to establish between organizations to define the responsibilities of each party outline the key deliverables and include monetary penalties for breaches to manage third-party risk?
- A. An ARO
- B. An MOU
- C. An SLA
- D. A BPA
Answer: B
NEW QUESTION 3
A security engineer needs to implement an MDM solution that complies with the corporate mobile device policy. The policy states that in order for mobile users to access corporate resources on their devices the following requirements must be met:
• Mobile device OSs must be patched up to the latest release
• A screen lock must be enabled (passcode or biometric)
• Corporate data must be removed if the device is reported lost or stolen
Which of the following controls should the security engineer configure? (Select TWO)
- A. Containerization
- B. Storage segmentation
- C. Posturing
- D. Remote wipe
- E. Full-device encryption
- F. Geofencing
Answer: DE
NEW QUESTION 4
In the middle of a cybersecurity, a security engineer removes the infected devices from the network and lock down all compromised accounts. In which of the following incident response phases is the security engineer currently operating?
- A. Identification
- B. Preparation
- C. Eradiction
- D. Recovery
- E. Containment
Answer: E
NEW QUESTION 5
Which of the following would BEST identify and remediate a data-loss event in an enterprise using third-party, web-based services and file-sharing platforms?
- A. SIEM
- B. CASB
- C. UTM
- D. DLP
Answer: D
NEW QUESTION 6
Which of the following are the MOST likely vectors for the unauthorized inclusion of vulnerable code in a software company’s final software releases? (Select TWO.)
- A. Unsecure protocols
- B. Use of penetration-testing utilities
- C. Weak passwords
- D. Included third-party libraries
- E. Vendors/supply chain
- F. Outdated anti-malware software
Answer: AD
NEW QUESTION 7
A Chief Security Officer (CSO) is concerned about the amount of PII that is stored locally on each salesperson’s laptop. The sales department has a higher-than-average rate of lost equipment. Which of the following recommendations would BEST address the CSO’s concern?
- A. Deploy an MDM solution.
- B. Implement managed FDE.
- C. Replace all hard drives with SEDs.
- D. Install DLP agents on each laptop.
Answer: B
NEW QUESTION 8
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company’s data?
- A. Containerization
- B. Geofencing
- C. Full-disk encryption
- D. Remote wipe
Answer: C
NEW QUESTION 9
A security administrator checks the table of a network switch, which shows the following output: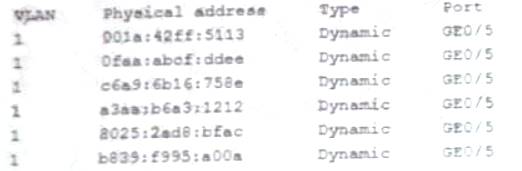
Which of the following is happening to this switch?
- A. MAC Flooding
- B. DNS poisoning
- C. MAC cloning
- D. ARP poisoning
Answer: A
NEW QUESTION 10
An employee has been charged with fraud and is suspected of using corporate assets. As authorities collect evidence, and to preserve the admissibility of the evidence, which of the following forensic techniques should be used?
- A. Order of volatility
- B. Data recovery
- C. Chain of custody
- D. Non-repudiation
Answer: C
NEW QUESTION 11
Which of the following relets to applications and systems that are used within an organization without consent or approval?
- A. Shadow IT
- B. OSINT
- C. Dark web
- D. Insider threats
Answer: A
NEW QUESTION 12
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account credentials of the Windows server first. Which of the following would be the BEST method to increase the security on the Linux server?
- A. Randomize the shared credentials
- B. Use only guest accounts to connect.
- C. Use SSH keys and remove generic passwords
- D. Remove all user accounts.
Answer: C
NEW QUESTION 13
Which of the following disaster recovery tests is The LEAST time-consuming for the disaster recovery team?
- A. Tabletop
- B. Parallel
- C. Full interruption
- D. Simulation
Answer: D
NEW QUESTION 14
A vulnerability assessment report will include the CVSS score of the discovered vulnerabilities because the score allows the organization to better.
- A. validate the vulnerability exists in the organization's network through penetration testing
- B. research the appropriate mitigation techniques in a vulnerability database
- C. find the software patches that are required to mitigate a vulnerability
- D. prioritize remediation of vulnerabilities based on the possible impact.
Answer: D
NEW QUESTION 15
A forensics examiner is attempting to dump password cached in the physical memory of a live system but keeps receiving an error message. Which of the following BEST describes the cause of the error?
- A. The examiner does not have administrative privileges to the system
- B. The system must be taken offline before a snapshot can be created
- C. Checksum mismatches are invalidating the disk image
- D. The swap file needs to be unlocked before it can be accessed
Answer: A
NEW QUESTION 16
A network technician is installing a guest wireless network at a coffee shop. When a customer purchases an Item, the password for the wireless network is printed on the recent so the customer can log in. Which of the following will the technician MOST likely configure to provide the highest level of security with the least amount of overhead?
- A. WPA-EAP
- B. WEP-TKIP
- C. WPA-PSK
- D. WPS-PIN
Answer: A
NEW QUESTION 17
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output: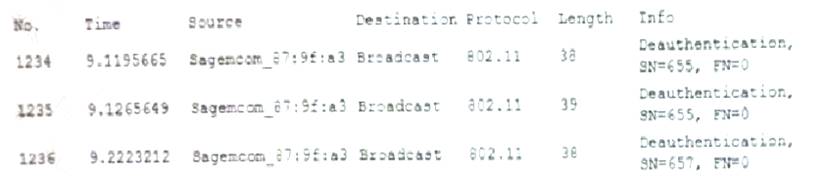
Which of the following attacks does the analyst MOST likely see in this packet capture?
- A. Session replay
- B. Evil twin
- C. Bluejacking
- D. ARP poisoning
Answer: B
NEW QUESTION 18
A forensics investigator is examining a number of unauthorized payments the were reported on the company's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
Which of the following will the forensics investigator MOST likely determine has occurred?
- A. SQL injection
- B. CSRF
- C. XSS
- D. XSRF
Answer: B
NEW QUESTION 19
Which of the following control sets should a well-written BCP include? (Select THREE)
- A. Preventive
- B. Detective
- C. Deterrent
- D. Corrective
- E. Compensating
- F. Physical
- G. Recovery
Answer: ADG
NEW QUESTION 20
A symmetric encryption algorithm Is BEST suited for:
- A. key-exchange scalability.
- B. protecting large amounts of data.
- C. providing hashing capabilities,
- D. implementing non-repudiation.
Answer: D
NEW QUESTION 21
Which of the following allows for functional test data to be used in new systems for testing and training purposes to protect the read data?
- A. Data encryption
- B. Data masking
- C. Data deduplication
- D. Data minimization
Answer: B
NEW QUESTION 22
......
P.S. Easily pass SY0-601 Exam with 218 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam SY0-601 Dumps: https://www.surepassexam.com/SY0-601-exam-dumps.html (218 New Questions)