Examcollection SY0-601 Questions are updated and all SY0-601 answers are verified by experts. Once you have completely prepared with our SY0-601 exam prep kits you will be ready for the real SY0-601 exam without a problem. We have Refresh CompTIA SY0-601 dumps study guide. PASSED SY0-601 First attempt! Here What I Did.
Free SY0-601 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
Joe, a user at a company, clicked an email link led to a website that infected his workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
- A. Install a definition-based antivirus.
- B. Implement an IDS/IPS
- C. Implement a heuristic behavior-detection solution.
- D. Implement CASB to protect the network shares.
Answer: C
NEW QUESTION 2
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS
Click on each firewall to do the following:  Deny cleartext web traffic.
Deny cleartext web traffic. Ensure secure management protocols are used.
Ensure secure management protocols are used.  Resolve issues at the DR site.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.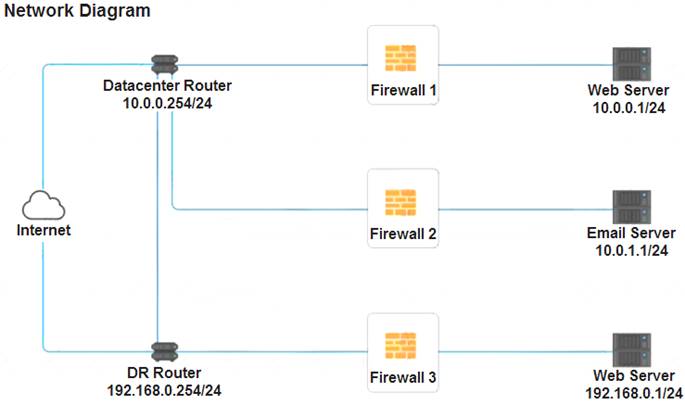
- A.
Answer: A
Explanation:
See explanation below.
Explanation
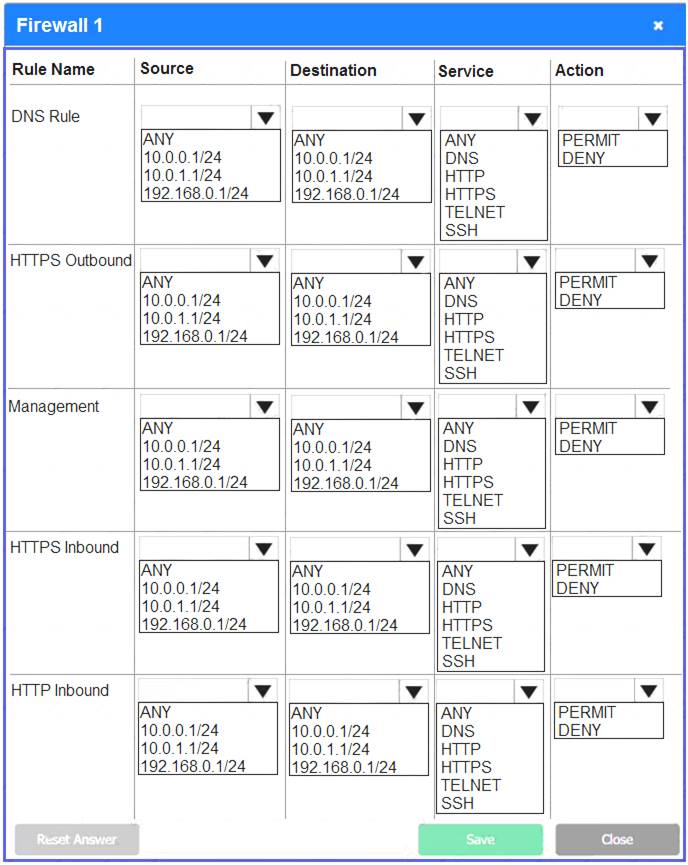
Firewall 1: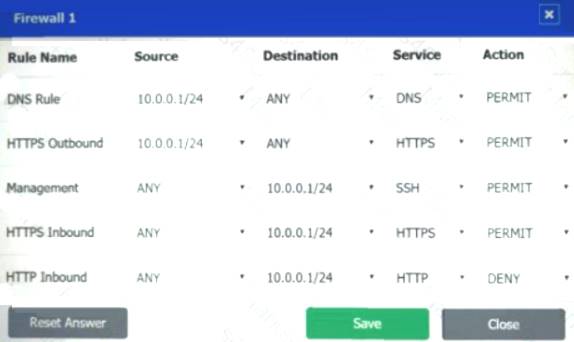
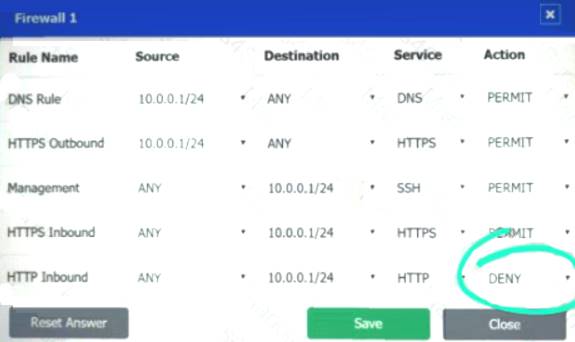
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
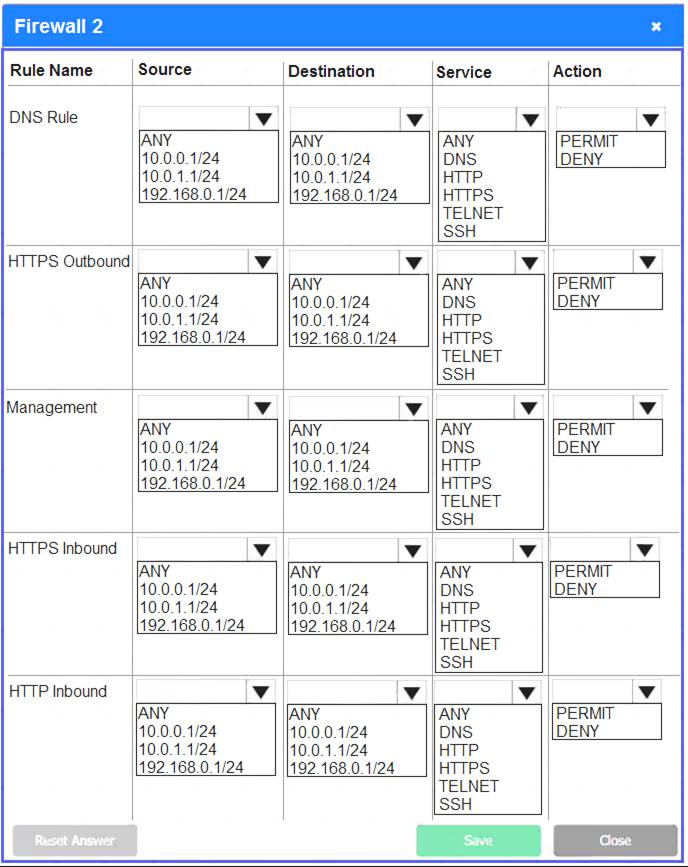
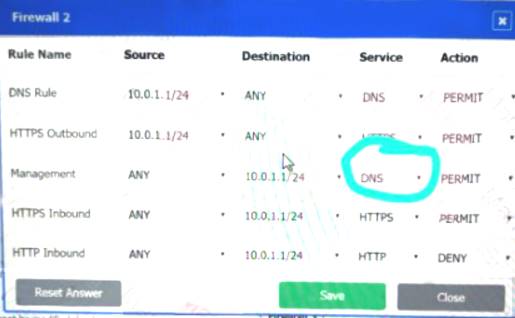
Firewall 2: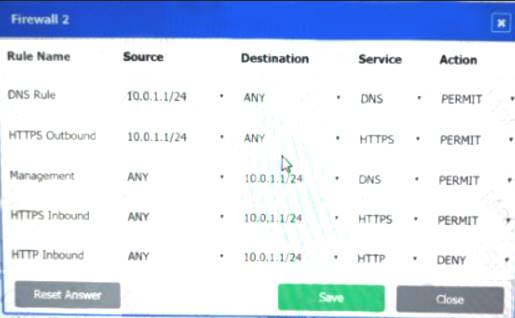
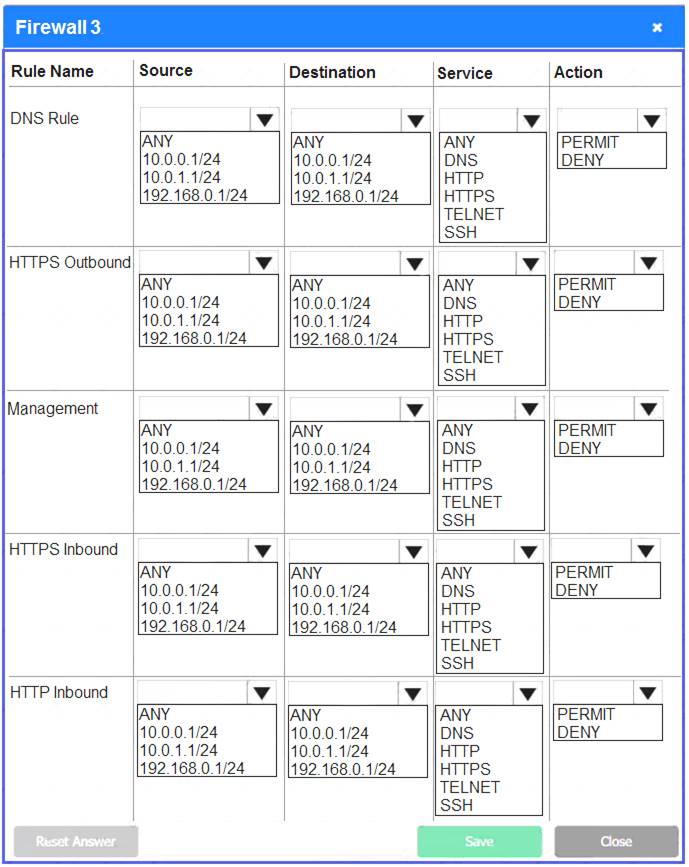
Firewall 3: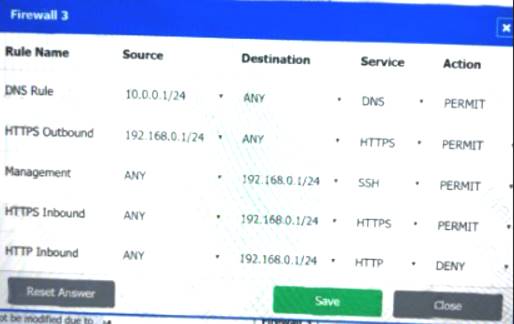
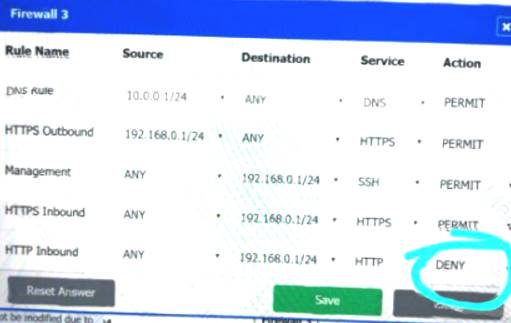
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
NEW QUESTION 3
Which of the following will MOST likely adversely impact the operations of unpatched traditional programmable-logic controllers, running a back-end LAMP server and OT systems with human-management interfaces that are accessible over the Internet via a web interface? (Choose two.)
- A. Cross-site scripting
- B. Data exfiltration
- C. Poor system logging
- D. Weak encryption
- E. SQL injection
- F. Server-side request forgery
Answer: DF
NEW QUESTION 4
An engineer wants to access sensitive data from a corporate-owned mobile device. Personal data is not allowed on the device. Which of the following MDM configurations must be considered when the engineer travels for business?
- A. Screen locks
- B. Application management
- C. Geofencing
- D. Containerization
Answer: D
NEW QUESTION 5
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.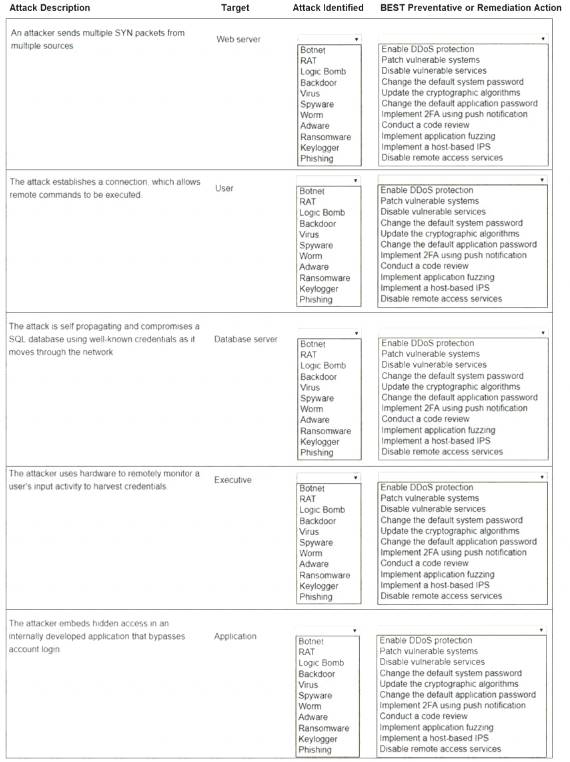
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 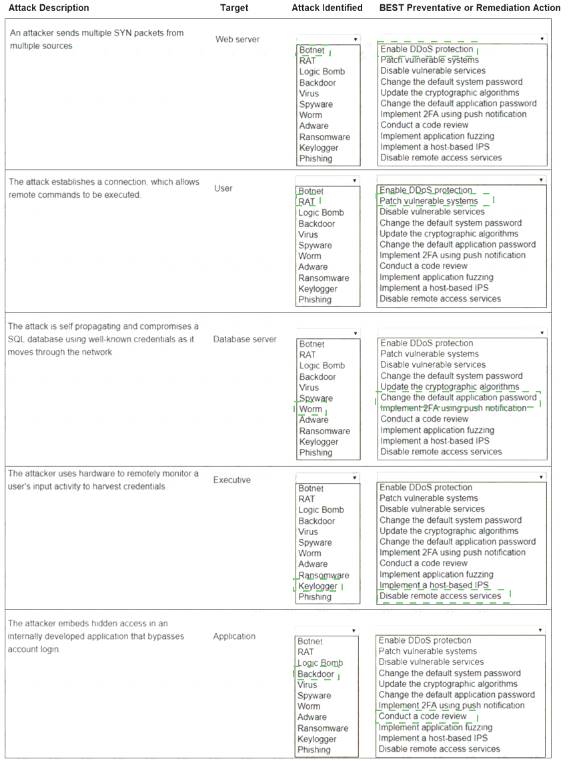
NEW QUESTION 6
Which of the following job roles would sponsor data quality and data entry initiatives that ensure business and regulatory requirements are met?
- A. The data owner
- B. The data processor
- C. The data steward
- D. The data privacy officer.
Answer: C
NEW QUESTION 7
A critical file server is being upgraded and the systems administrator must determine which RAID level the new server will need to achieve parity and handle two simultaneous disk failures. Which of the following RAID levels meets this requirements?
- A. RAID 0+1
- B. RAID 2
- C. RAID 5
- D. RAID 6
Answer: C
NEW QUESTION 8
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly. Which of the following technologies should the IT manager use when implementing MFA?
- A. One-time passwords
- B. Email tokens
- C. Push notifications
- D. Hardware authentication
Answer: C
NEW QUESTION 9
Which of the following describes the ability of code to target a hypervisor from inside
- A. Fog computing
- B. VM escape
- C. Software-defined networking
- D. Image forgery
- E. Container breakout
Answer: B
NEW QUESTION 10
A RAT that was used to compromise an organization’s banking credentials was found on a user’s computer. The RAT evaded antivirus detection. It was installed by a user who has local administrator rights to the system as part of a remote management tool set. Which of the following recommendations would BEST prevent this from reoccurring?
- A. Create a new acceptable use policy.
- B. Segment the network into trusted and untrusted zones.
- C. Enforce application whitelisting.
- D. Implement DLP at the network boundary.
Answer: C
NEW QUESTION 11
While checking logs, a security engineer notices a number of end users suddenly downloading files with the .t ar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external email containing an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
- A. A RAT was installed and is transferring additional exploit tools.
- B. The workstations are beaconing to a command-and-control server.
- C. A logic bomb was executed and is responsible for the data transfers.
- D. A fireless virus is spreading in the local network environment.
Answer: A
NEW QUESTION 12
A company provides mobile devices to its users to permit access to email and enterprise applications. The company recently started allowing users to select from several different vendors and device models. When configuring the MDM, which of the following is a key security implication of this heterogeneous device approach?
- A. The most common set of MDM configurations will become the effective set of enterprise mobile security controls.
- B. All devices will need to support SCEP-based enrollment; therefore, the heterogeneity of the chosen architecture may unnecessarily expose private keys to adversaries.
- C. Certain devices are inherently less secure than others, so compensatory controls will be needed to address the delta between device vendors.
- D. MDMs typically will not support heterogeneous deployment environments, so multiple MDMs will need to be installed and configured.
Answer: C
NEW QUESTION 13
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
- A. SDP
- B. AAA
- C. IaaS
- D. MSSP
- E. Microservices
Answer: D
NEW QUESTION 14
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
- A. A script kiddie
- B. Shadow IT
- C. Hacktivism
- D. White-hat
Answer: B
NEW QUESTION 15
A security assessment determines DES and 3DES at still being used on recently deployed production servers. Which of the following did the assessment identify?
- A. Unsecme protocols
- B. Default settings
- C. Open permissions
- D. Weak encryption
Answer: D
NEW QUESTION 16
An analyst needs to set up a method for securely transferring files between systems. One of the requirements is to authenticate the IP header and the payload. Which of the following services would BEST meet the criteria?
- A. TLS
- B. PFS
- C. ESP
- D. AH
Answer: A
NEW QUESTION 17
A network engineer needs to create a plan for upgrading the wireless infrastructure in a large office Priority must be given to areas that are currently experiencing latency and connection issues. Which of the following would be the BEST resource for determining the order of priority?
- A. Nmapn
- B. Heat maps
- C. Network diagrams
- D. Wireshark
Answer: C
NEW QUESTION 18
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which of the following methods would BEST prevent the exfiltration of data? (Select TWO).
- A. VPN
- B. Drive encryption
- C. Network firewall
- D. File level encryption
- E. USB blocker
- F. MFA
Answer: BE
NEW QUESTION 19
The following is an administrative control that would be MOST effective to reduce the occurrence of malware execution?
- A. Security awareness training
- B. Frequency of NIDS updates
- C. Change control procedures
- D. EDR reporting cycle
Answer: A
NEW QUESTION 20
A security analyst needs to complete an assessment. The analyst is logged into a server and must use native tools to map services running on it to the server's listening ports. Which of the following tools can BEST accomplish this talk?
- A. Netcat
- B. Netstat
- C. Nmap
- D. Nessus
Answer: B
NEW QUESTION 21
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site Upon investigation, a security analyst the identifies the following:
• The legitimate websites IP address is 10.1.1.20 and eRecruit local resolves to the IP
• The forged website's IP address appears to be 10.2.12.99. based on NetFtow records
• AH three at the organization's DNS servers show the website correctly resolves to the legitimate IP
• DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
- A. A reverse proxy was used to redirect network traffic
- B. An SSL strip MITM attack was performed
- C. An attacker temporarily pawned a name server
- D. An ARP poisoning attack was successfully executed
Answer: B
NEW QUESTION 22
......
P.S. Downloadfreepdf.net now are offering 100% pass ensure SY0-601 dumps! All SY0-601 exam questions have been updated with correct answers: https://www.downloadfreepdf.net/SY0-601-pdf-download.html (218 New Questions)