Our pass rate is high to 98.9% and the similarity percentage between our 300-410 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Cisco 300-410 exam in just one try? I am currently studying for the Cisco 300-410 exam. Latest Cisco 300-410 Test exam practice questions and answers, Try Cisco 300-410 Brain Dumps First.
Check 300-410 free dumps before getting the full version:
NEW QUESTION 1
Refer to the exhibit.
What does the imp-null tag represent in the MPLS VPN cloud?
- A. Pop the label
- B. Impose the label
- C. Include the EXP bit
- D. Exclude the EXP bit
Answer: A
Explanation:
The imp-null (implicit null) tag instructs the upstream router to pop the tag entry off the tag stack before forwarding the packet.
Note: pop means remove the top MPLS label
NEW QUESTION 2
Refer to the exhibit.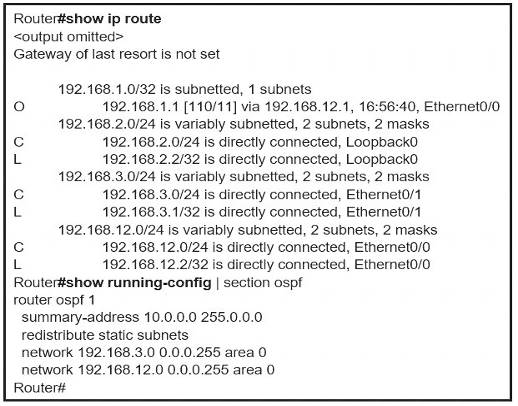
An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the summary route does not show up in the routing table. Why is the summary route missing?
- A. The summary-address command is used only for summarizing prefixes between areas.
- B. The summary route is visible only in the OSPF database, not in the routing table.
- C. There is no route for a subnet inside 10.0.0.0/8, so the summary route is not generated.
- D. The summary route is not visible on this router, but it is visible on other OSPF routers in the same area.
Answer: C
Explanation:
The summary-address is only used to create aggregate addresses for OSPF at an autonomous system boundary. It means this command should only be used on the ASBR when you are trying to summarize externally redistributed routes from another protocol domain or you have a NSSA area. But a requirement to create a summarized route is:
The ASBR compares the summary route’s range of addresses with all routes redistributed into OSPF on that ASBR to find any subordinate subnets (subnets that sit inside the summary route range). If at least one subordinate subnet exists, the ASBR advertises the summary route.
NEW QUESTION 3
The network administrator configured R1 for Control Plane Policing so that the inbound Telnet traffic is policed to 100 kbps. This policy must not apply to traffic coming in from 10.1.1.1/32 and 172.16.1.1/32. The administrator has configured this: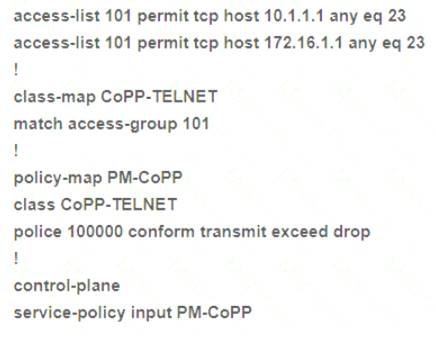
The network administrator is not getting the desired results. Which set of configurations resolves this issue?
- A. control-planeno service-policy input PM-CoPP!interface Ethernet 0/0service-policy input PM-CoPP
- B. control-planeno service-policy input PM-CoPP service-policy input PM-CoPP
- C. no access-list 101access-list 101 deny tcp host 10,1,1.1 any eq 23access-list 101 deny tcp host 172,16.1.1 any eq 23 access-list 101 permit ip any any
- D. no access-list 101access-list 101 deny tcp host 10,1.1.1 any eq 23access-list 101 deny tcp host 172.16.1.1 any eq 23 access-list 101 permit ip any any!interface E0/0service-policy input PM-CoPP
Answer: C
Explanation:
Packets that match a deny rule are excluded from that class and cascade to the next class (if one exists) for classification. Therefore if we don’t want to CoPP traffic from 10.1.1.1/32 and 172.16.1.1/32, we must “deny” them in the ACL.
NEW QUESTION 4
Drag and drop the descriptions from the left onto the corresponding MPLS components on the right.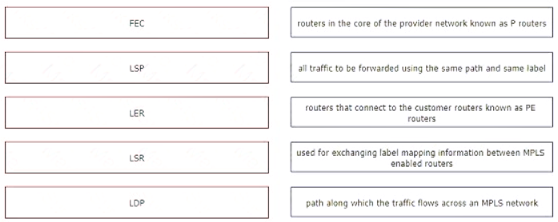
Solution:
Table Description automatically generated
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Which protocol is used to determine the NBMA address on the other end of a tunnel when mGRE is used?
- A. NHRP
- B. IPsec
- C. MP-BGP
- D. OSPF
Answer: A
NEW QUESTION 6
A customer reports to the support desk that they cannot print from their PC to the local printer id:401987778. Which tool must be used to diagnose the issue using Cisco DNA Center Assurance?
- A. application trace
- B. path trace
- C. ACL trace
- D. device trace
Answer: B
NEW QUESTION 7
How is VPN routing information distributed in an MPLS network?
- A. The top level of the customer data packet directs it to the correct CE device
- B. It is established using VPN IPsec peers.
- C. It is controlled using of VPN target communities.
- D. It is controlled through the use of RD.
Answer: C
Explanation:
The distribution of virtual private network (VPN) routing information is controlled through the use of VPN route target communities, implemented by Border Gateway Protocol (BGP) extended communities.
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_l3_vpns/configuration/15-mt/mp-l3-vpns-15-mt-book/m
NEW QUESTION 8
Refer to the exhibit.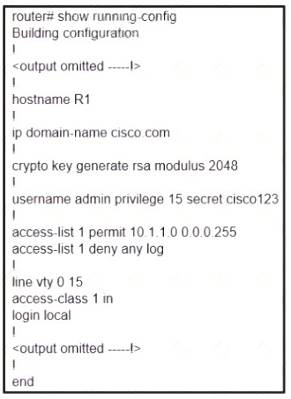
A user cannot SSH to the router. What action must be taken to resolve this issue?
- A. Configure transport input ssh
- B. Configure transport output ssh
- C. Configure ip ssh version 2
- D. Configure ip ssh source-interface loopback0
Answer: A
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960x/software/15-0_2_EX/security/configuration_
NEW QUESTION 9
Refer to the exhibit.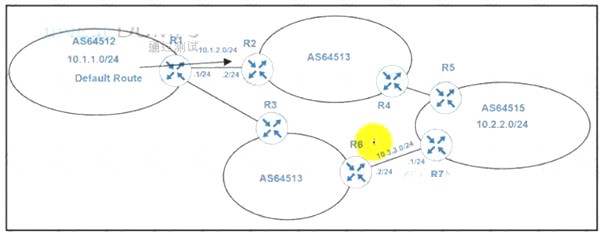
An engineer must configure PBR on R1 to reach to 10.2.2.0/24 via R3 AS64513 as the primary path and a backup route through default route via R2 AS64513. All BGP routes are in the routing table of R1. but a static default route overrides BGP routes. Which PBR configuration achieves the objective?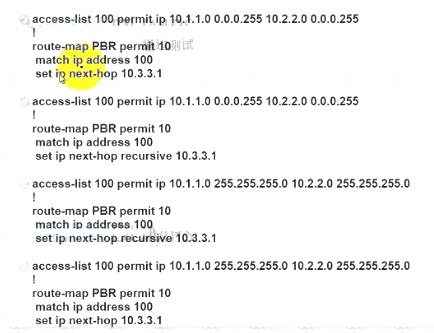
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
NEW QUESTION 10
Refer to the exhibit.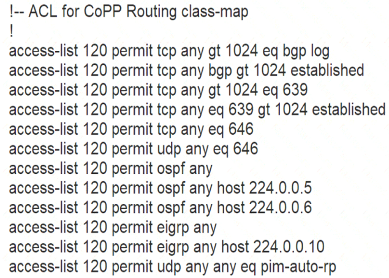
The control plane is heavily impacted after the CoPP configuration is applied to the router. Which command removal lessens the impact on the control plane?
- A. access-list 120 permit udp any any eq pim-auto-rp
- B. access-list 120 permit eigrp any host 224.0.0.10
- C. access-list 120 permit ospf any
- D. access-list 120 permit tcp any gt 1024 eq bgp log
Answer: A
NEW QUESTION 11
Refer to the exhibit.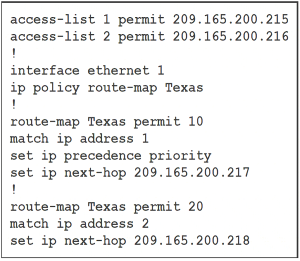
Packets arriving from source 209.165.200.215 must be sent with the precedence bit set to 1, and packets arriving from source 209.165.200.216 must be sent with the precedence bit set to 5. Which action resolves the issue?
- A. set ip precedence critical in route-map Texas permit 10
- B. set ip precedence critical in route-map Texas permit 20
- C. set ip precedence immediate in route-map Texas permit 10
- D. set ip precedence priority in route-map Texas permit 20
Answer: B
NEW QUESTION 12
Refer to the exhibit.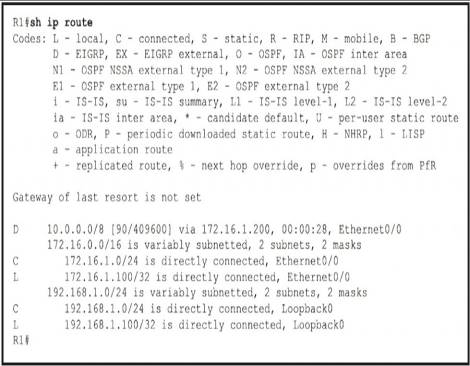
The R2 loopback interface is advertised with RIP and EIGRP using default values. Which configuration changes make R1 reach the R2 loopback using RIP?
- A. R1(config)# router rip R1(config-router)# distance 90
- B. R1(config)# router rip R1(config-router)# distance 100
- C. R1(config)# router eigrp 1R1(config-router)# distance eigrp 130 120
- D. R1(config)# router eigrp 1R1(config-router)# distance eigrp 120 120
Answer: C
Explanation:
distance (AD Number u want to change to) (neighbor IP) (Wildcard Mask) (access-list number)
NEW QUESTION 13
Refer to the exhibit.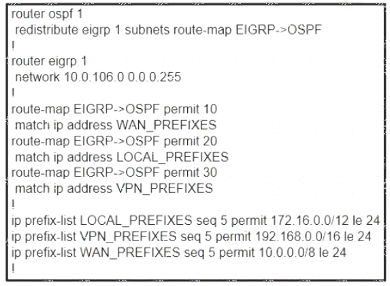
The network administrator configured redistribution on an ASBR to reach to all WAN networks but failed Which action resolves the issue?
- A. The route map must have the keyword prefix-list to evaluate the prefix list entries
- B. The OSPF process must have a metric when redistributing prefixes from EIGRP.
- C. The route map EIGRP->OSPF must have the 10.0.106.0/24 entry to exist in one of the three prefix lists to pass
- D. EIGRP must redistribute the 10.0.106.0/24 route instead of using the network statement
Answer: A
Explanation:
In order to use a prefix-list in a route-map, we must use the keyword “prefix-list” in the “match” statement. . For example:
match ip address prefix-list WAN_PREFIXES
Without this keyword, the router will try to find an access-list with the same name instead.
NEW QUESTION 14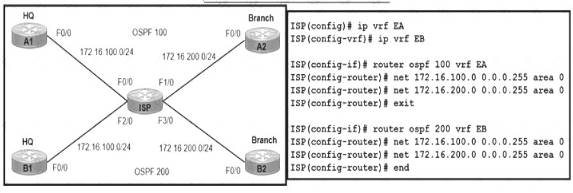
Refer to the exhibit. A network engineer is provisioning end-to-end traffic service for two different enterprise networks with these requirements The OSPF process must differ between customers on HQ and Branch office routers, and adjacencies should come up instantly.
The OSPF process must differ between customers on HQ and Branch office routers, and adjacencies should come up instantly. The enterprise networks are connected with overlapping networks between HO and a branch office Which configuration meets the requirements for a customer site?
The enterprise networks are connected with overlapping networks between HO and a branch office Which configuration meets the requirements for a customer site?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
NEW QUESTION 15
A company is expanding business by opening 35 branches over the Internet. A network engineer must configure DMVPN at the branch routers to connect with the hub router and allow NHRP to add spoke routers securely to the multicast NHRP mappings automatically Which configuration meets this requirement at the hub router?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
Explanation:
The command “ip nhrp map multicast dynamic” allows NHRP to automatically add spoke routers to the multicast NHRP mappings.
NEW QUESTION 16
Which two technologies optimize MPLS infrastructure using bandwidth protection services when experiencing slow response7 (Choose two.)
- A. IPLFA
- B. MPLS OAM
- C. VPLS
- D. SO-MPLS
- E. Fast-Rwoute
Answer: AE
NEW QUESTION 17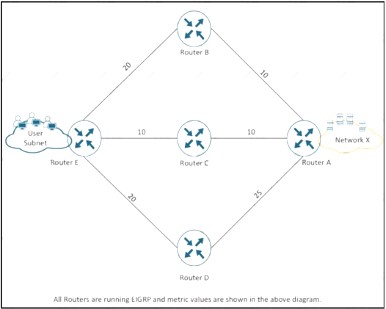
Refer to the exhibit. The IT manager received reports from users about slow application through network x. which action resolves the issue?
- A. Use the variance 2 command to enable load balancing.
- B. Increase the bandwidth from the service provider.
- C. Move the servers into the users subnet.
- D. Upgrade the IOS on router E.
Answer: A
NEW QUESTION 18
Which statement about IPv6 ND inspection is true?
- A. It learns and secures bindings for stateless autoconfiguration addresses in Layer 3 neighbor tables.
- B. It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables.
- C. It learns and secures bindings for stateful autoconfiguration addresses in Layer 3 neighbor tables.
- D. It learns and secures bindings for stateful autoconfiguration addresses in Layer 2 neighbor tables.
Answer: B
Explanation:
IPv6 ND inspection learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables. IPv6 ND inspection analyzes neighbor discovery messages in order to build a trusted binding table database, and IPv6 neighbor discovery messages that do not have valid bindings are dropped. A neighbor discovery message is considered trustworthy if its IPv6-to-MAC mapping is verifiable.
This feature mitigates some of the inherent vulnerabilities for the neighbor discovery mechanism, such as attacks on duplicate address detection (DAD), address resolution, device discovery, and the neighbor cache.
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipv6_fhsec/configuration/15-s/ip6f-15-s-book/ip6-snooping.p
NEW QUESTION 19
Refer to the exhibit.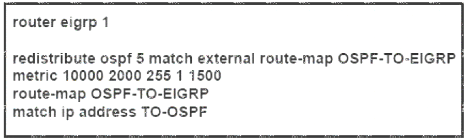
Which routes from OSPF process 5 are redistributed into EIGRP?
- A. E1 and E2 subnets matching access list TO-OSPF
- B. E1 and E2 subnets matching prefix list TO-OSPF
- C. only E2 subnets matching access list TO-OSPF
- D. only E1 subnets matching prefix listTO-OS1
Answer: A
NEW QUESTION 20
A network administrator is troubleshooting a failed AAA login issue on a Cisco Catalyst c3560 switch. When the network administrator tries to log in with SSH using TACACS+ username and password credentials, the switch is no longer authenticating and is failing back to the local account. Which action resolves this issue?
- A. Configure ip tacacs source-interface GigabitEthernet 1/1
- B. Configure ip tacacs source-ip 192.168.100.55
- C. Configure ip tacacs-server source-ip 192.168.100.55
- D. Configure ip tacacs-server source-interface GigabitEthernet 1/1
Answer: A
NEW QUESTION 21
......
P.S. Easily pass 300-410 Exam with 575 Q&As DumpSolutions.com Dumps & pdf Version, Welcome to Download the Newest DumpSolutions.com 300-410 Dumps: https://www.dumpsolutions.com/300-410-dumps/ (575 New Questions)